Troubleshooting the deployment of SCEP certificates profile to devices in Intune
This articles gives troubleshooting guidance for issues deploying of Simple Certificate Enrollment Protocol (SCEP) certificate profiles with Microsoft Intune. Certificate deployment is Step 1 of the SCEP communication flow overview.
The SCEP certificate profile, and the trusted certificate profile specified in the SCEP profile, must both be assigned to the same user, or the same device. The following table shows the expected result of mixed assignments:
| Trusted certificate profile assignment includes User | Trusted certificate profile assignment includes Device | Trusted certificate profile assignment includes User and Device | |
|---|---|---|---|
| SCEP certificate profile assignment includes User | Success | Failure | Success |
| SCEP certificate profile assignment includes Device | Failure | Success | Success |
| SCEP certificate profile assignment includes User and Device | Success | Success | Success |
Android
SCEP certificate profiles for Android come down to the device as a SyncML and are logged in the OMADM log.
Validate that the Android device was sent the policy
To validate a profile was sent to the device you expect, in the Microsoft Intune admin center go to Troubleshooting + Support > Troubleshoot. On the Troubleshoot window, set Assignments to Configuration profiles and then validate the following configurations:
Specify the user who should receive the SCEP certificate profile.
Review the user's group membership to ensure they are in the security group you used with the SCEP certificate profile.
Review when the device last checked in with Intune.
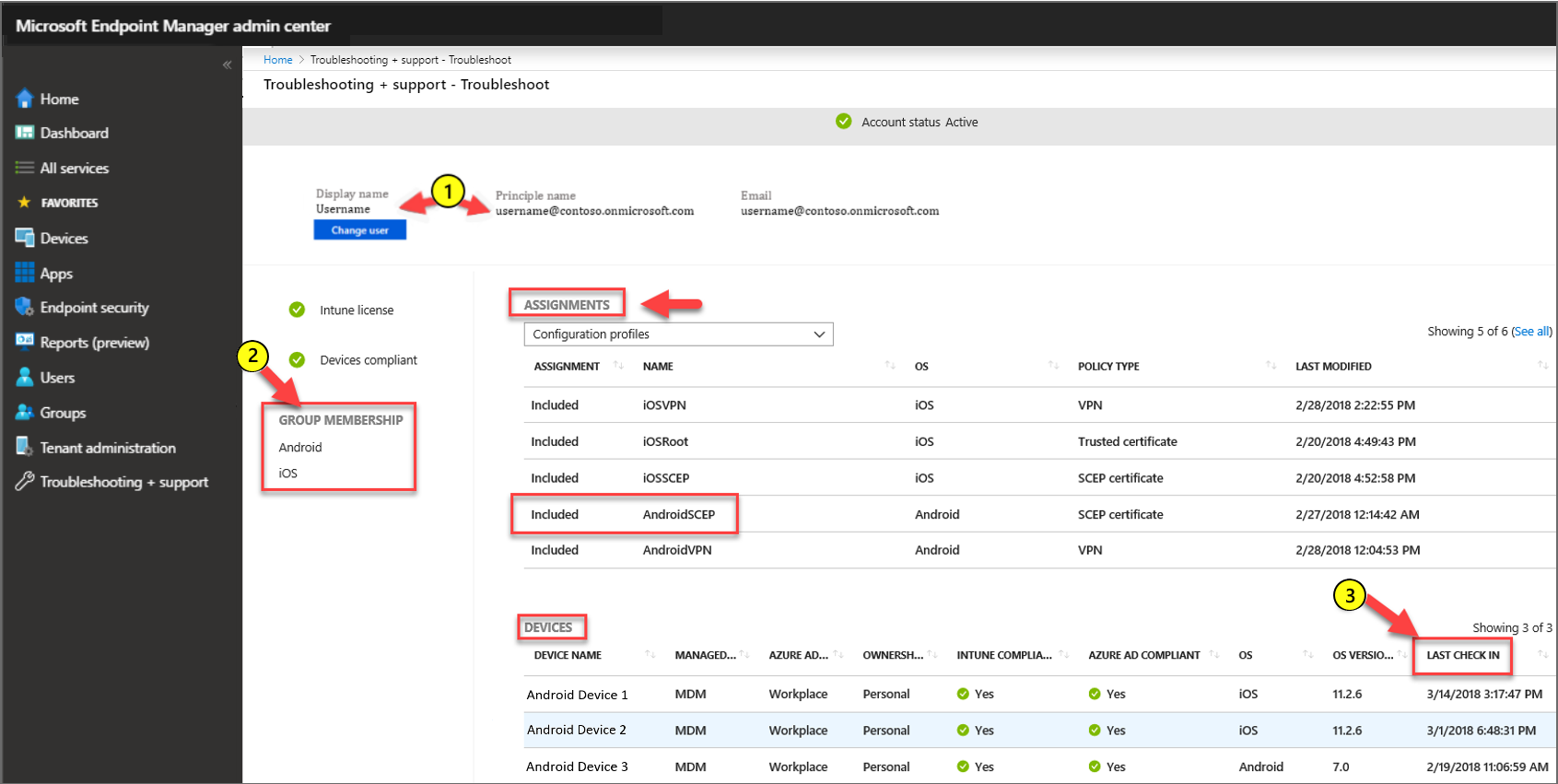
Validate the policy reached the Android device
Review the devices OMADM log. Look for entries that resemble the following examples, which are logged when the device gets the profile from Intune:
Time VERB Event com.microsoft.omadm.syncml.SyncmlSession 9595 9 <?xml version="1.0" encoding="utf-8"?><SyncML xmlns="SYNCML:SYNCML1.2"><SyncHdr><VerDTD>1.2</VerDTD><VerProto>DM/1.2</VerProto><SessionID>1</SessionID><MsgID>6</MsgID><Target><LocURI>urn:uuid:UUID</LocURI></Target><Source><LocURI>https://a.manage.microsoft.com/devicegatewayproxy/AndroidHandler.ashx</LocURI></Source><Meta><MaxMsgSize xmlns="syncml:metinf">524288</MaxMsgSize></Meta></SyncHdr><SyncBody><Status><CmdID>1</CmdID><MsgRef>6</MsgRef><CmdRef>0</CmdRef><Cmd>SyncHdr</Cmd><Data>200</Data></Status><Replace><CmdID>2</CmdID><Item><Target><LocURI>./Vendor/MSFT/Scheduler/IntervalDurationSeconds</LocURI></Target><Meta><Format xmlns="syncml:metinf">int</Format><Type xmlns="syncml:metinf">text/plain</Type></Meta><Data>28800</Data></Item></Replace><Replace><CmdID>3</CmdID><Item><Target><LocURI>./Vendor/MSFT/EnterpriseAppManagement/EnterpriseIDs</LocURI></Target><Data>contoso.onmicrosoft.com</Data></Item></Replace><Exec><CmdID>4</CmdID><Item><Target><LocURI>./Vendor/MSFT/EnterpriseAppManagement/EnterpriseApps/ClearNotifications</LocURI></Target></Item></Exec><Add><CmdID>5</CmdID><Item><Target><LocURI>./Vendor/MSFT/CertificateStore/Root/{GUID}/EncodedCertificate</LocURI></Target><Data>Data</Data></Item></Add><Add><CmdID>6</CmdID><Item><Target><LocURI>./Vendor/MSFT/CertificateStore/Enroll/ModelName=AC_51…%2FLogicalName_39907…%3BHash=-1518303401/Install</LocURI></Target><Meta><Format xmlns="syncml:metinf">xml</Format><Type xmlns="syncml:metinf">text/plain</Type></Meta><Data><CertificateRequest><ConfigurationParametersDocument>&lt;ConfigurationParameters xmlns="http://schemas.microsoft.com/SystemCenterConfigurationManager/2012/03/07/CertificateEnrollment/ConfigurationParameters"&gt;&lt;ExpirationThreshold&gt;20&lt;/ExpirationThreshold&gt;&lt;RetryCount&gt;3&lt;/RetryCount&gt;&lt;RetryDelay&gt;1&lt;/RetryDelay&gt;&lt;TemplateName /&gt;&lt;SubjectNameFormat&gt;{ID}&lt;/SubjectNameFormat&gt;&lt;SubjectAlternativeNameFormat&gt;{ID}&lt;/SubjectAlternativeNameFormat&gt;&lt;KeyStorageProviderSetting&gt;0&lt;/KeyStorageProviderSetting&gt;&lt;KeyUsage&gt;32&lt;/KeyUsage&gt;&lt;KeyLength&gt;2048&lt;/KeyLength&gt;&lt;HashAlgorithms&gt;&lt;HashAlgorithm&gt;SHA-1&lt;/HashAlgorithm&gt;&lt;HashAlgorithm&gt;SHA-2&lt;/HashAlgorithm&gt;&lt;/HashAlgorithms&gt;&lt;NDESUrls&gt;&lt;NDESUrl&gt;https://breezeappproxy-contoso.msappproxy.net/certsrv/mscep/mscep.dll&lt;/NDESUrl&gt;&lt;/NDESUrls&gt;&lt;CAThumbprint&gt;{GUID}&lt;/CAThumbprint&gt;&lt;ValidityPeriod&gt;2&lt;/ValidityPeriod&gt;&lt;ValidityPeriodUnit&gt;Years&lt;/ValidityPeriodUnit&gt;&lt;EKUMapping&gt;&lt;EKUMap&gt;&lt;EKUName&gt;Client Authentication&lt;/EKUName&gt;&lt;EKUOID&gt;1.3.6.1.5.5.7.3.2&lt;/EKUOID&gt;&lt;/EKUMap&gt;&lt;/EKUMapping&gt;&lt;/ConfigurationParameters&gt;</ConfigurationParametersDocument><RequestParameters><CertificateRequestToken>PENlcnRFbn... Hash: 1,010,143,298</CertificateRequestToken><SubjectName>CN=name</SubjectName><Issuers>CN=FourthCoffee CA; DC=fourthcoffee; DC=local</Issuers><SubjectAlternativeName><SANs><SAN NameFormat="ID" AltNameType="2" OID="{OID}"></SAN><SAN NameFormat="ID" AltNameType="11" OID="{OID}">[email protected]</SAN></SANs></SubjectAlternativeName><NDESUrl>https://breezeappproxy-contoso.msappproxy.net/certsrv/mscep/mscep.dll</NDESUrl></RequestParameters></CertificateRequest></Data></Item></Add><Get><CmdID>7</CmdID><Item><Target><LocURI>./Vendor/MSFT/CertificateStore/SCEP</LocURI></Target></Item></Get><Add><CmdID>8</CmdID><Item><Target><LocURI>./Vendor/MSFT/GCM</LocURI></Target><Data>Data</Data></Item></Add><Replace><CmdID>9</CmdID><Item><Target><LocURI>./Vendor/MSFT/GCM</LocURI></Target><Data>Data</Data></Item></Replace><Get><CmdID>10</CmdID><Item><Target><LocURI>./Vendor/MSFT/NodeCache/SCConfigMgr</LocURI></Target></Item></Get><Get><CmdID>11</CmdID><Item><Target><LocURI>./Vendor/MSFT/NodeCache/SCConfigMgr/CacheVersion</LocURI></Target></Item></Get><Get><CmdID>12</CmdID><Item><Target><LocURI>./Vendor/MSFT/NodeCache/SCConfigMgr/ChangedNodes</LocURI></Target></Item></Get><Get><CmdID>13</CmdID><Item><Target><LocURI>./DevDetail/Ext/Microsoft/LocalTime</LocURI></Target></Item></Get><Get><CmdID>14</CmdID><Item><Target><LocURI>./Vendor/MSFT/DeviceLock/DevicePolicyManager/IsActivePasswordSufficient</LocURI></Target></Item></Get><Get><CmdID>15</CmdID><Item><Target><LocURI>./Vendor/MSFT/WorkProfileLock/DevicePolicyManager/IsActivePasswordSufficient</LocURI></Target></Item></Get><Final /></SyncBody></SyncML>
Examples of key entries:
ModelName=AC_51bad41f-3854-4eb5-a2f2-0f7a94034ee8%2FLogicalName_39907e78_e61b_4730_b9fa_d44a53e4111c%3BHash=-1518303401NDESUrls&gt;&lt;NDESUrl&gt;https://<server>-contoso.msappproxy.net/certsrv/mscep/mscep.dll&lt;/NDESUrl&gt;&lt;/NDESUrls
iOS/iPadOS
Validate that the iOS/iPadOS device was sent the policy
To validate a profile was sent to the device you expect, in the Microsoft Intune admin center go to Troubleshooting + Support > Troubleshoot. On the Troubleshoot window, set Assignments to Configuration profiles and then validate the following configurations:
Specify the user who should receive the SCEP certificate profile.
Review the user's group Membership to ensure they are in the security group you used with the SCEP certificate profile.
Review when the device last checked in with Intune.
Validate the policy reached the iOS or iPadOS device
Review the devices debug log. Look for entries that resemble the following examples, which are logged when the device gets the profile from Intune:
debug 18:30:54.638009 -0500 profiled Adding dependent ModelName=AC_51bad41f.../LogicalName_1892fe4c...;Hash=-912418295 to parent 636572740000000000000012 in domain PayloadDependencyDomainCertificate to system\
Examples of key entries:
ModelName=AC_51bad41f.../LogicalName_1892fe4c...;Hash=-912418295PayloadDependencyDomainCertificate
Windows
Validate that the Windows device was sent the policy
To validate the profile was sent to the device you expect, in the Microsoft Intune admin center, go to Troubleshooting + Support > Troubleshoot. On the Troubleshoot window, set Assignments to Configuration profiles and then validate the following configurations:
Specify the user who should receive the SCEP certificate profile.
Review the user's group membership to ensure they are in the security group you used with the SCEP certificate profile.
Review when the device last checked in with Intune.
Validate the policy reached the Windows device
The arrival of the policy for the profile is logged in a Windows device's DeviceManagement-Enterprise-Diagnostics-Provider > Admin log, with an event ID 306.
To open the log:
On the device, run eventvwr.msc to open Windows Event Viewer.
Expand Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostic-Provider > Admin.
Look for Event 306, which resembles the following example:
Event ID: 306 Task Category: None Level: Information User: SYSTEM Computer: <Computer Name> Description: SCEP: CspExecute for UniqueId : (ModelName_<ModelName>_LogicalName_<LogicalName>_Hash_<Hash>) InstallUserSid : (<UserSid>) InstallLocation : (user) NodePath : (clientinstall) KeyProtection: (0x2) Result : (Unknown Win32 Error code: 0x2ab0003).The error code 0x2ab0003 translates to DM_S_ACCEPTED_FOR_PROCESSING.
A non-successful error code might provide indication of the underlying problem.
Next steps
If the profile reaches the device, the next step is to review the device to NDES server communication.