Invite users with Microsoft Entra B2B collaboration
You can invite other users to access your environment. A user with the User Administrator role can do this through the Azure portal. Learn more at Add guest users to the directory. Invited users can access your environment using their own login credentials once a license and a security role are assigned to them. The use of the apps created using Power Apps, customer engagement apps (such as Dynamics 365 Sales, Dynamics 365 Customer Service, Dynamics 365 Field Service, Dynamics 365 Customer Insights - Journeys, and Dynamics 365 Project Operations), and finance and operations apps are granted. You don’t need to create a new user account and temporary password for these invited users in your own Microsoft 365 tenant.
Requirements
To send business-to-business (B2B) user invitations, you must have at least the User Administrator role.
To bulk- invite users, get the latest Microsoft Entra IDPowerShell which can be downloaded from the PowerShell module's release page.
Incompatibilities
The following features aren't supported for B2B invited users.
Unified Service Desk client
Invited users won't be able to use the Unified Service Desk client to log into the host tenant’s environment.
Dynamics 365 App for Outlook
Invited users won't be able to use their own tenant email addresses when performing email related transactions in the host environment.
Microsoft 365 Groups
Microsoft 365 Groups connects a group to customer engagement apps. Data (including new conversations and documents) are stored in the Exchange and/or SharePoint system. Since invited users belong to a different Microsoft 365 tenant, the invited users don't have permission to create Microsoft 365 Groups in the invited-to Microsoft 365 tenant. However, they can participate in the Microsoft 365 Groups conversations as a guest in their Outlook Inbox, but not within customer engagement apps.
Dynamics 365 Customer Voice
Invited users won't be able to use Dynamics 365 Customer Voice. You must create a new user in your tenant and then provide access to the new user.
Invite a user
You can add users to through Microsoft Entra ID B2B user collaboration. Users with sufficient access such as user admins can use the Azure portal to invite B2B collaboration users to the directory, to any security group, or to any application.
Admins can use one of the following methods to invite B2B users to their environment:
Invite users to your environment that has a security group.
See Control user access to environments: security groups and licenses on how to use security groups for your environments.
Invite users to your environment that don't have a security group.
Bulk-invite guest users using a .csv file.
- See PowerShell example.
Your invited user receives an email invitation to get started with B2B user collaboration.
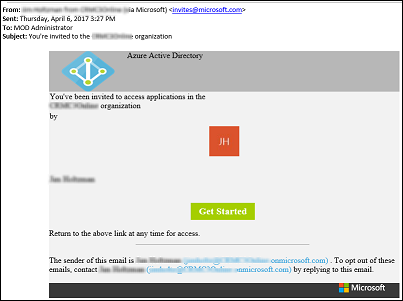
When your user accepts the invitation by clicking on the Get Started link on the invitation email, they're prompted to accept the invitation.
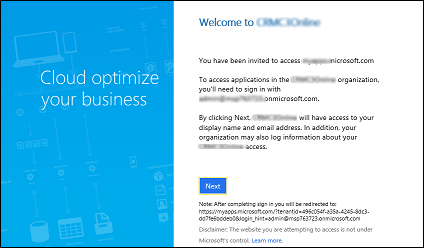
Note
Until you add a license to the user account, the user doesn't have access to customer engagement apps. Follow the steps below to add a license through the Azure portal.
Update user’s name and usage location
To assign a license, the invited user’s Usage location must be specified. Admins can update the invited user’s profile on the Azure portal.
Go to Microsoft Entra > Users and groups > All users. If you don't see the newly created user, refresh the page.
Click on the invited user, and then click Profile.

Update First name, Last name, and Usage location.
Click Save, and then close the Profile blade.
Assign invited users a license and security role
Assign your invited users a license and security role so the user can use customer engagement apps.
Go to Microsoft Entra > Users and groups > All users. If you don't see the newly created user, refresh the page.
Click on the invited user, and then click Licenses.
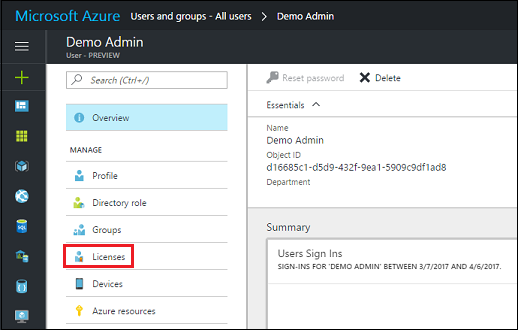
Click
 Assign.
Assign.Click Configure required settings.
Select the product to license.
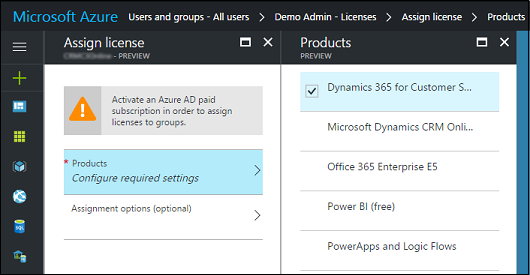
Click Select, and then click Assign.
Next, assign the invited users with appropriate security roles for the environment so they can access it. See Create users.
Notify your invited users
To complete the user invitation, notify your invited users and provide them with the URL for the environment they're invited to (for example, https://contoso.crm.dynamics.com).
Power Apps support for B2B guest maker
B2B guest users can run Power Apps.
Follow these steps to allow B2B collaboration users to create Power Apps.
Note
Ensure that you perform below steps on the resource tenant, and not on the home tenant.
- A resource tenant is where the app is expected to exist, and where the user is expected to create the app using Power Apps as a guest.
- A home tenant is where the user's account resides and authenticates against.
In Microsoft Entra ID, in external collaboration settings set guest user access to "(most inclusive)". For more info about Microsoft Entra B2B checkout: What is guest user access in Microsoft Entra B2B?
Use the following PowerShell cmdlet to enable guests to make Power Apps.
$requestBody = Get-TenantSettings $requestBody.powerPlatform.powerApps.enableGuestsToMake = $True Set-TenantSettings $requestBodyAssign the Environment Maker security role to the B2B guest users that you want to be able to create apps and Microsoft list custom forms using Power Apps.
Tip
In addition, you can also review all other guests of this security role (especially in the default environment), and remove users that aren't expected to have this privilege.
After the B2B guest users are given the required permissions to create and edit apps, they can now create Power Apps and Microsoft List custom forms using Power Apps.
B2B guests can follow these steps to sign in the preferred Microsoft Entra tenant to build apps.
Optional: Assign a security role that allows B2B guest users to perform solution import and export.
Known limitations
- To sign in to make.powerapps.com via Azure B2B, a user is required to sign in to a Microsoft Entra tenant. Microsoft Accounts (for example [email protected], [email protected], [email protected]) can't directly sign in to https://make.powerapps.com.
- If the Azure B2B maker is expected to build an app that uses Dataverse or build apps in a solution, they need a license with Dataverse use rights assigned to them in the resource tenant.
- B2B makers are currently not supported across sovereign cloud boundaries. For example, a B2B guest from a commercial tenant can't make apps in a GCC tenant. The same is applicable for GCC to GCC High, commercial to China cloud, and so on.
Related content
Microsoft Entra B2B Collaboration is Generally Available!
Microsoft Entra B2B collaboration code and PowerShell samples
Microsoft Entra B2B collaboration frequently-asked questions (FAQ)
Microsoft Entra B2B Collaboration
Microsoft Entra B2B: New updates make cross-business collab easy
Microsoft Entra cross-tenant access overview
Restrict cross-tenant inbound and outbound access
Share a canvas app with guest users