Events
Apr 8, 3 PM - May 28, 7 AM
Sharpen your AI skills and enter the sweepstakes to win a free Certification exam
Register now!This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Microsoft Security Copilot in the Microsoft Defender portal enables security teams to quickly identify malicious and suspicious files through AI-powered file analysis capabilities.
If you're new to Security Copilot, you should familiarize yourself with it by reading the following articles:
Security operations teams tracking and resolving attacks need tools and techniques to quickly analyze potentially malicious files. Sophisticated attacks often use files that mimic legitimate or system files to avoid detection. In addition, new-to-the-field security analysts might require time and gain significant experience to use available analysis tools and techniques.
The file analysis capability of Copilot in Defender reduces the barrier to learning file analysis by immediately delivering reliable and complete file investigation results. This capability empowers security analysts from all levels to complete their investigation with a shorter turnaround time. The report includes an overview of the file, details of the file's contents, and a summary of the file's assessment.
The file analysis capability is available in Microsoft Defender for customers who have provisioned access to Security Copilot.
Security Copilot standalone portal users also have the file analysis capability and other Defender XDR capabilities through the Microsoft Defender XDR plugin. Know more about preinstalled plugins in Security Copilot.
The file analysis results generated by Copilot usually contains the following information:
Note
The analysis results vary depending on the contents of the file.
You can access the file analysis capability through the following ways:
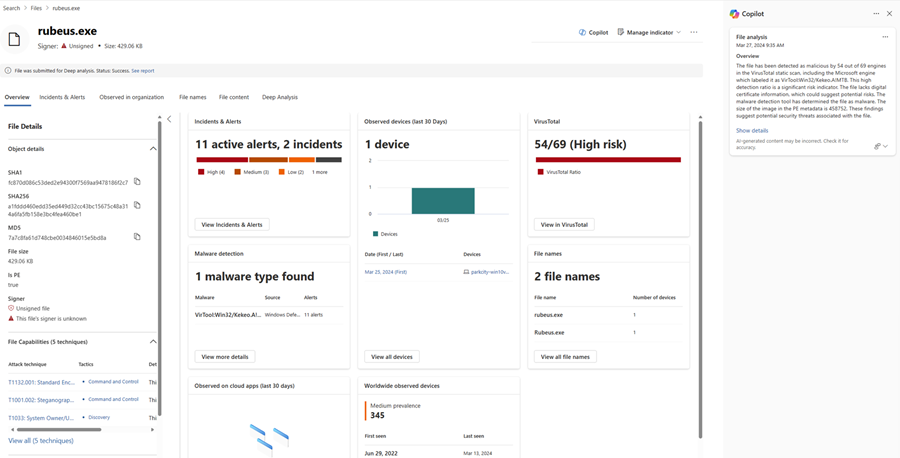 Select Show details (shown above) to display the full results or Hide details (highlighted below) to minimize the results.
Select Show details (shown above) to display the full results or Hide details (highlighted below) to minimize the results.

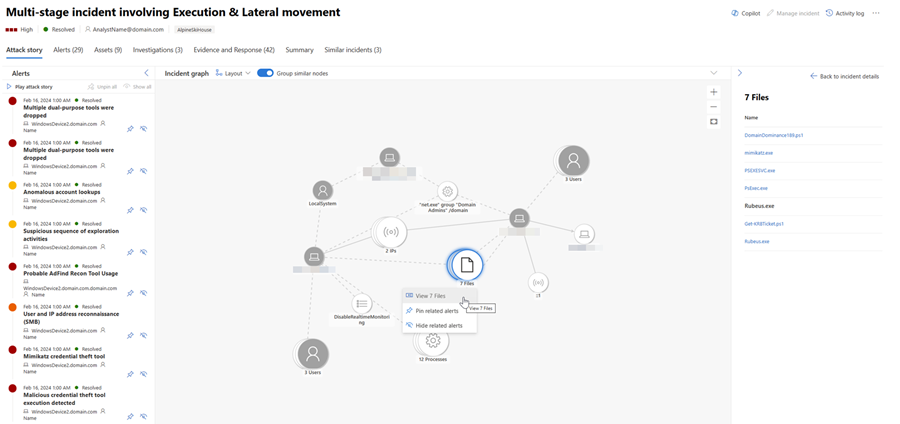 Select a file to investigate, then select Analyze on the side pane to begin analysis. The results are then displayed on the Copilot pane.
Select a file to investigate, then select Analyze on the side pane to begin analysis. The results are then displayed on the Copilot pane.
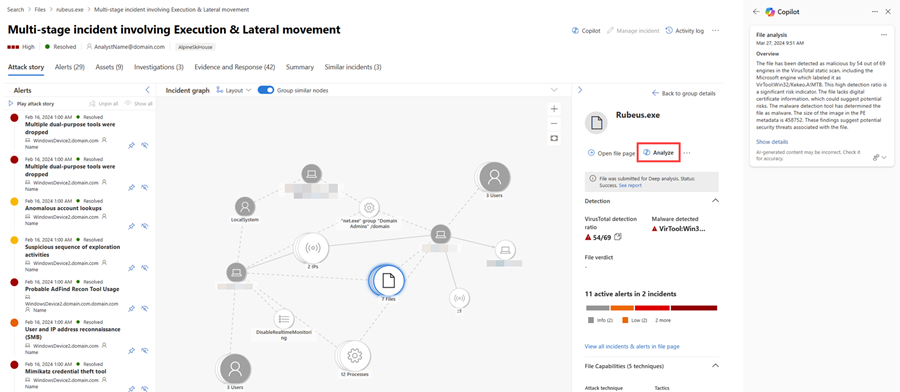
You can copy the results to clipboard, regenerate the results, or open the Security Copilot portal by selecting the More actions ellipsis (...) on top of the file analysis card.
In the Security Copilot standalone portal, you can use the following prompt to generate a device summary:
Tip
When investigating files in the Security Copilot portal, Microsoft recommends including the word Defender in your prompts to ensure that the file analysis capability delivers the results.
Always review the results generated by Copilot in Defender. Your feedback helps improve the quality of the results generated by Copilot. Select the feedback icon  at the bottom of the Copilot pane to provide feedback.
at the bottom of the Copilot pane to provide feedback.
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender XDR Tech Community.
Events
Apr 8, 3 PM - May 28, 7 AM
Sharpen your AI skills and enter the sweepstakes to win a free Certification exam
Register now!