Microsoft 365 Copilot admin guide for E5 licenses
When preparing your organization for Microsoft 365 Copilot or you're ready to start using Copilot, there are features in your E5 license that can help get your data ready.
When users enter a prompt, Copilot can respond with data that the user has permission to access. Overshared and outdated data can lead to inaccurate results from Copilot.
This article provides guidance for IT admins with Microsoft 365 E5 and SharePoint Advanced Management (SAM) licenses. With the features included in these licenses, you:
- Use SharePoint Advanced Management (SAM) to help prevent oversharing, declutter data sources, and monitor SharePoint site changes.
- Use Microsoft Purview to enable sensitivity labels, identify and protect sensitive data, restrict endpoints, and delete the content you don't need.
To learn more, watch Oversharing Control at Enterprise Scale (opens YouTube's website).
When you use the features described in this article, your organization is better prepared for Copilot, including getting more accurate results from Copilot.
This article applies to:
- Microsoft 365 Copilot
- Microsoft SharePoint Premium - SharePoint Advanced Management (SAM)
- Microsoft Purview
Note
If you have an E3 license, then see Microsoft 365 Copilot admin guide for E3 licenses. For a comparison of the features in the licenses, see Compare Microsoft Copilot features in E3 and E5 licenses.
Before you begin
Microsoft recommends you also follow the steps in Microsoft 365 Copilot - best practices with SharePoint. It helps you optimize your search in SharePoint, update sharing settings in SharePoint & OneDrive, and check permissions & site access on your SharePoint sites.
The following licenses are required to use the features in this article:
Microsoft 365 E5 or Office 365 E5
- Microsoft Purview - Included with your E5 license
For a list of the features and services you get with your license, see Microsoft 365, Office 365, Enterprise Mobility + Security, and Windows 11 Subscriptions.
Microsoft SharePoint Premium - SharePoint Advanced Management
There are some features in SharePoint Advanced Management (SAM) that are included with your Microsoft 365 Copilot license. To get the full version of SAM and use all the features described in this article, you need the Microsoft SharePoint Premium - SharePoint Advanced Management license.
-
Depending on your subscription plan, you might be able purchase Microsoft 365 Copilot licenses through the Microsoft 365 admin center (Billing > Purchase services), Microsoft partners, or your Microsoft account team.
Microsoft 365 Copilot licenses are available as an add-on to other licensing plans. To learn more, see Understand licensing for Microsoft 365 Copilot.
This article uses the following admin centers. These admin centers require a specific role to complete the tasks in the article.
SharePoint admin center: Sign in as the SharePoint administrator.
Microsoft Purview portal: There are different roles, depending on the task you need to complete. To learn more, see:
Step 1 - Use SharePoint Advanced Management (SAM) features
There are features in SharePoint Advanced Management (SAM) that can help you get ready for Copilot.
✅ Copilot goals with SAM:
- Declutter data sources by finding and removing inactive SharePoint sites.
- Identify SharePoint sites with overshared or sensitive content.
- Use policy to restrict access to SharePoint sites that are business critical or have sensitive content.
- Monitor site changes.
This section walks you through different SAM features that can help you get your organization and your data ready for Copilot.
To learn more about SAM + Copilot, see Get ready for Copilot with SharePoint Advanced Management.
Ensure all sites have valid owners
✅ Run a Site Ownership policy that finds any sites that don't have at least two owners
A Site ownership policy automatically detects sites that don't have at least two owners and can help find potential owners. Set up the policy in simulation mode to identify owners based on your desired criteria. Then, upgrade the policy to Active mode to enable notifications to site owner candidates.
You need site owners to help confirm the site is still active, perform Site access review, update content permissions, and control access when needed.
- Sign in to the SharePoint admin center as a SharePoint administrator.
- Expand Policies > select Site lifecycle management.
- Select Create a policy, enter your parameters, and finish your policy.
- When the policy runs, the report shows the number of sites that are noncompliant. You can also download the report.
To learn more about this policy and report, see Site ownership policy.
Find and cleanup inactive sites
✅ Create a site lifecycle management policy that finds inactive sites
A site lifecycle management policy automatically detects inactive sites and sends a notification email to the site owners. When you use the email, the site owners can confirm that the site is still active.
Copilot can show data from these inactive sites in user prompts, which can lead to inaccurate and cluttered Copilot results.
The policy also creates a report that you can download and review. The report shows the inactive sites, the last activity date, and the email notification status.
- Sign in to the SharePoint admin center as a SharePoint administrator.
- Expand Policies > select Site lifecycle management.
- Select Create a policy, enter your parameters, and finish your policy.
- When the policy runs and finds inactive sites, the policy automatically emails the site owners. The site owners should confirm if the site is still active.
- If the site owners confirm the sites aren't needed, then put inactive sites in read-only mode with SAM, or move the sites to Microsoft 365 Archive with SAM.
To learn more about this policy and report, see site lifecycle management policy.
Best practices for managing inactive SharePoint sites
- Use the policy execution report to keep track on site owner action status in response to the notifications.
- Select the Get AI insights button to get AI insights generated for the report to help you identify issues with the sites and possible actions to address these issues.
- Give the site owners a timeline to complete these tasks. If they don't complete the task within the timeframe, you can move the sites to Microsoft 365 Archive using SAM Inactive Sites - Archive capability so that you can reactive them later if needed.
This action helps reduce outdated content that clutters Copilot's data source, which improves the accuracy of Copilot responses.
Tip
Sites moved to Microsoft 365 Archive are no longer accessible by anyone in the organization outside of Microsoft Purview or admin search. Copilot won't include content from these sites when responding to user prompts.
Identify sites with overshared or sensitive content
✅ Run Data access governance (DAG) reports in the SharePoint admin center
The DAG reports give more detailed information about site sharing links, sensitivity labels, and the Everyone except external users (EEEU) permissions on your SharePoint sites. Use these reports to find overshared sites.
Overshared sites are sites that are shared with more people than needed. Copilot can show data from these sites in responses.
Sign in to the SharePoint admin center as a SharePoint administrator.
Select Reports > Data access governance. Your report options:
Report Description Task Sharing links Shows the sites that have sharing links, including links shared with Anyone, shared with People in your organization, and shared with Specific people outside of your work or school. Review these sites.
Make sure the sites are shared with only the users or groups that need access. Remove sharing for unneeded users and groups.Sensitivity labels applied to files Shows sites with Office files that have sensitivity labels. Review these sites.
Make sure the correct labels are applied. Update the labels as needed. To learn more, see Identify and label sensitive data (in this article).Shared with Everyone except external users(EEEU)Shows the sites that are shared with everyone in your organization except external users. Review these sites.
Determine if EEEU permissions are appropriate. Many sites with EEEU are overshared. Remove the EEEU permission and assign to the users or groups as needed.Oversharing Baseline Report for Sites, OneDrives and Files Scans all sites in your tenant, and lists sites that share content with more than a specified number of users (you specify the number). Sort, filter or download the report, and identify the sites with potentially overshared content.
You can run any of these reports individually or run all of them together. To learn more about these reports, see Data access governance (DAG) reports.
Best practices for managing the DAG reports
Run these reports weekly, especially in the beginning stages of adopting Copilot. As you become more familiar with the reports and the data, you can adjust the frequency.
If you have an admin team, create an admin task to run these reports and review the data.
Your organization is paying for the license to run these reports and use the data to make decisions. Make sure you're getting the most out of it.
Select Get AI insights to generate a report that helps you identify issues with the sites and possible actions to address these issues.
Control access to overshared SharePoint sites
✅ Initiate Site access reviews for site owners
In a Data access governance (DAG) report, you can select sites with oversharing risks. Then, initiate site access reviews. Site Owners receive notification for each site that requires attention. They can use the Site reviews page to track and manage multiple review requests.
The site owner reviews access in two main areas: SharePoint groups and individual items. They can determine if broad sharing is appropriate, or if a site is overshared and requires remediation.
If the site owner determines that the content is overshared, they can use the Access Review dashboard to update permissions.
✅ Use restricted access control policy (RAC) in the SharePoint admin center
A restricted access control policy restricts access to a site with overshared content. It can restrict access to SharePoint sites and content to users in a specific group. Users not in the group can't access the site or its content, even if they previously had permissions or a shared link.
When users in the group have permissions to the content, then that content can show in Copilot results. Users not in the group don't see this info in their Copilot results. You can set up restricted access control for individual sites or OneDrive.
✅ Use restricted content discoverability policy (RCD) in the SharePoint admin center
A restricted content discoverability policy (RCD) doesn't change the site access. Instead, it changes the site's content discoverability. When you apply RCD to a site, the site's content isn't discoverable by Copilot or organization-wide search results for all users.
The SharePoint Admin can set restricted content discoverability on individual sites.
Best practices for control access to overshared SharePoint sites
If your organization has a Zero Trust mindset, then you can apply restricted access control (RAC) to all sites. Then, adjust the permissions as needed. If you have many sites, this action can help you quickly secure your sites. But, it can cause disruptions to users.
If you use RAC or RCD, make sure you communicate the changes and the reasons for the changes.
Tip
For business-critical sites, you can also:
- When you create new sites, configure a RAC or RCD policy as part of your custom site provisioning process. This step proactively avoids oversharing.
- Consider blocking downloads from selected sites using a block download policy. For example, block the download of Teams meeting recordings and transcripts.
- Apply encryption with "extract rights" enforced on business-critical office documents. To learn more, see Microsoft Purview data security and compliance protections for generative AI apps.
Monitor changes
✅ Run the change history report in the SharePoint admin center
The change history report tracks and monitor changes, including what changed, when the change happened, and who initiated the change. The intent is to identify recent changes that could lead to oversharing, which impacts Copilot results.
Use this report to review the changes made to your SharePoint sites and organization settings.
Sign in to the SharePoint admin center as a SharePoint administrator.
Expand Reports > select Change history > New report.
Your report options:
Report Description Task Site settings report Shows the site property changes and actions ran by Site Administrators and SharePoint Administrators. Review the changes and actions. Make sure the actions meet your security requirements. Organization settings report Shows changes made to organization settings, like when a site is created and if external sharing is enabled. Review the changes and actions. Make sure the changes meet your security requirements.
Best practices for managing the change history reports
Run these reports weekly, especially in the beginning stages of adopting Copilot. As you become more familiar with the reports and the data, you can adjust the frequency.
If you have an admin team, create an admin task to run these reports and review the data.
Your organization is paying for the license to run these reports and use the data to make decisions. Make sure you're getting the most out of it.
Create a report for the site level changes and the organization level changes. The site level reports show changes made to the site properties and actions. The organization level reports show changes made to the organization settings.
Review the sharing settings and access control settings. Make sure the changes align with your security requirements. If they don't align, then work with the site owners to correct the settings.
Apply restricted access control (RAC) to sites that appear to be overshared. Inform the site owners of the changes and why.
If your organization has a Zero Trust mindset, then you can apply RAC to all sites. Then, adjust the permissions as needed. If you have many sites, this action can help you quickly secure your sites. But, it can also cause disruptions to users. Make sure you communicate the changes and the reasons for the changes.
Step 2 - Restrict SharePoint Search (RSS)
✅ Copilot goal: Disable RSS
As you get ready for Copilot, you review and configure the correct permissions on your SharePoint sites. You might have enabled Restricted SharePoint Search (RSS).
RSS is a temporary solution that gives you time to review and configure the correct permissions on your SharePoint sites. You add the reviewed & corrected sites to an allowed list.
If your SharePoint site permissions are set correctly, then disable RSS.
When disabled, SharePoint search accesses all your SharePoint sites. When users enter prompts, Copilot can show data from all your sites, which shows more relevant and complete information in the response.
The goal is to disable RSS and allow SharePoint search to access all your sites. This action gives Copilot more data to work with, which can improve the accuracy of the responses.
OR
If you enabled RSS, then add more sites to the allowed list. You can add up to 100 sites to the allowed list. Copilot can show data from the allowed list sites in user prompts.
Remember, your goal is to review & configure the correct permissions on your SharePoint sites, and disable RSS.
To learn more, see:
- Restricted SharePoint Search
- Curate the allowed list for Restricted SharePoint Search
- Blog - Introducing Restricted SharePoint Search to help you get started with Microsoft 365 Copilot
Disable RSS and remove sites from the allowed list
- Use the
Set-SPOTenantRestrictedSearchModePowerShell cmdlet to disable RSS. - Use the
Remove-SPOTenantRestrictedSearchAllowedSitePowerShell cmdlet to remove sites from the allowed list.
To learn more about these cmdlets, see Use PowerShell Scripts for Restricted SharePoint Search.
Add sites to the RSS allowed list
Get a list of the sites that you want to add to the allowed list.
Option 1 - Use the Sharing links report
- Sign in to the SharePoint admin center as a SharePoint administrator.
- Select Reports > Data access governance > Sharing links > View reports.
- Select one of the reports, like "Anyone" links. This report shows a list of sites with the highest number of Anyone links created. These links let anyone access files and folders without signing in. These sites are candidates to allow in tenant/org wide search.
Option 2 - Use the sort and filter options for Active sites
Sign in to the SharePoint admin center as a SharePoint administrator.
Select Sites > Active sites.
Use the sort and filter options to find the most active site, including page views. These sites are candidates to allow in a tenant/organization wide search.
Use the
Add-SPOTenantRestrictedSearchAllowedListPowerShell cmdlet to add the sites to the allowed list.To learn more about this cmdlet, see Use PowerShell Scripts for Restricted SharePoint Search.
Step 3 - Use Microsoft Purview features
There are features in Microsoft Purview that can help you get ready for Copilot.
✅ Copilot goals with Purview:
- Identify and label sensitive data in Microsoft 365.
- Detect and protect sensitive information from unauthorized sharing or leakage.
- Delete the content you don't need.
- Detect sensitive data and noncompliant content in Copilot prompts and responses.
- Review and analyze Copilot prompts and responses.
To learn more about how Microsoft Purview can help you to govern, protect, and manage your data, see Learn about Microsoft Purview.
Identify and label sensitive data
✅ Create and apply sensitivity labels to protect your data
Sensitivity labels are a way to identify and classify the sensitivity of your organization's data, adding an extra layer of protection to your data.
When sensitivity labels are applied to items, like documents and emails, the labels add the protection directly to this data. As a result, that protection persists, wherever the data is stored. When sensitivity labels are applied to containers, like SharePoint sites and groups, the labels add protection indirectly by controlling access to the container where the data is stored. For example, privacy settings, external user access, and access from unmanaged devices.
The sensitivity labels can also affect Copilot results, including:
The label settings include protection actions, like access to sites, customizable headers and footers, and encryption.
If the label applies encryption, Copilot checks the usage rights for the user. For Copilot to return data from that item, the user must be granted permissions to copy from it.
A prompt session with Copilot (called Business Chat) can reference data from different types of items. Sensitivity labels are shown in the returned results. The latest response displays the sensitivity label with the highest priority.
If Copilot creates new content from labeled items, the sensitivity label from the source item is automatically inherited.
This section walks you through the steps to create and use the default sensitivity labels from Microsoft Purview. If you need to use your own label names and configurations, create the labels manually or edit the default labels. If you already created your own sensitivity labels, you can't create the default labels.
To learn more about sensitivity labels, see:
- Get started with sensitivity labels
- Default labels and policies to protect your data
- Common scenarios for sensitivity labels
- Microsoft Purview strengthens information protection for Copilot
1. Create the default sensitivity labels
Sign into the Microsoft Purview portal as an admin in one of the groups listed at Sensitivity labels - permissions.
Select Solutions > DSPM for AI > Overview.
In the Recommendations section, select Information Protection Policy for Sensitivity Labels. This step creates the default labels and their policies.
To see or edit the default labels, or to create your own labels, select Information protection > Sensitivity labels. You might have to select Refresh.
When you have the default sensitivity labels:
- The labels help protect your data and can affect Copilot results.
- Your users can start manually applying published labels to their files and emails.
- Admins can start creating policies and configuring features that automatically apply labels to files and emails.
2. Enable and configure sensitivity labels for containers
The default sensitivity labels don't include settings for groups and sites, which let you apply a sensitivity label to a SharePoint or Teams site, or Microsoft Loop workspace. Items in the container don't inherit the sensitivity label. Instead, the label settings can restrict access to the container. This restriction provides an extra layer of security when you use Copilot. If a user can't access the site or workspace, Copilot can't access it on behalf of that user.
For example, you can set the privacy setting to Private, which restricts site access to only approved members in your organization. When the label is applied to the site, it replaces any previous setting and locks it for as long as the label is applied. This feature is a more secure setting than letting anybody access the site and allowing users to change the setting. When only approved members can access the data, it helps prevent oversharing of data that Copilot might access.
To configure any label settings for groups and sites, you must enable this capability for your tenant and then synchronize your labels. This configuration is a one-time configuration. To learn more, see How to enable sensitivity labels for containers and synchronize labels.
You can then edit your sensitivity labels, or create new sensitivity labels specifically for groups and sites:
For the sensitivity label scope, select Groups & sites. Remember, you must have already run the PowerShell commands. If you didn't, you can't select this scope.
Select the groupings of settings to configure. Some of the settings have backend dependencies before they can be enforced, like Conditional Access that must be already configured. The privacy setting, which is included in Privacy and external user access settings, doesn't have any backend dependencies.
Configure the settings you want to use and save your changes.
For more information, including details of all the available label settings that you can configure for groups and sites, see Use sensitivity labels to protect content in Microsoft Teams, Microsoft 365 groups, and SharePoint sites.
3. Publish your labels and educate your users
If you're using the default sensitivity labels, the labels are automatically published to all users, even if you edit the labels.
If you created your own sensitivity labels, you must add your labels to a publishing policy. When they're published, users can manually apply the labels in their Office apps. For labels that include the Groups & sites scope, users can apply these labels to new and existing sites, teams, and Loop workspaces. The publishing policies also have settings that you need to consider, like a default label and requiring users to label their data.
To learn more, see Publish sensitivity labels by creating a label policy.
Educate your users and provide guidance for when they should apply each sensitivity label.
In addition to manually applying labels, the default label policy includes applying the General \ All Employees (unrestricted) label as the default label for items. This label offers a base layer of protection. But, users should change the label if needed, especially for more sensitive content that requires encryption.
To help you with this step, see End-user documentation for sensitivity labels.
Monitor your labels. Select Information protection > Reports. You can see the usage of your labels.
4. Enable sensitivity labels for files in SharePoint and OneDrive
This step is a one-time configuration that is required to enable sensitivity labels for SharePoint and OneDrive. It's also required for Microsoft 365 Copilot to access encrypted files stored in these locations.
As with all tenant-level configuration changes for SharePoint and OneDrive, it takes about 15 minutes for the change to take effect. Then users can select sensitivity labels in Office on the web and you can create policies that automatically label files in these locations.
You have two options:
Option 1: Select Information Protection > Sensitivity labels. If you see the following message, select Turn on now:
Option 2: Use the
[Set-SPOTenant](/powershell/module/sharepoint-online/set-spotenant)Windows PowerShell cmdlet.
To learn more about this configuration, see Enable sensitivity labels for files in SharePoint and OneDrive.
Tip
Although not related to Copilot, now is a good time to enable co-authoring for encrypted files, if it's not already enabled. This setting ensures the best user experience for collaboration and might be required for other labeling scenarios.
5. Set default sensitivity labels for your SharePoint document libraries
The default labeling policy is configured to apply the default sensitivity label of General \ All Employees (unrestricted) for unlabeled files, emails, and meetings. You might want to override that setting with location-based labeling for SharePoint document libraries. This labeling method applies a default label to a document library.
You have two automatic labeling options for files in the same document library:
| Library option | When to use this option |
|---|---|
| Option 1 - Default sensitivity label that can apply admin-defined permissions (the Assign permissions now encryption option), or no encryption. | Recommended for new document libraries and when they store files that usually have the same level of known sensitivity. For exceptions, you want users to be able to select an alternative label that doesn't apply encryption. All new files that don't have a sensitivity label and uploaded to the library will be labeled with this library default label. |
| Option 2 - Protects files that are downloaded and extends SharePoint permissions to the downloaded file copy. To configure this setting for the library, the sensitivity label must be configured with user-defined permissions (the Let users assign permissions encryption option). Currently in preview, this configuration requires PowerShell commands at the tenant-level and then the site level before you can select a sensitivity label. |
Recommended for new and existing document libraries when you want to centralize permissions and continue to protect files when they're downloaded. This option is suitable when you haven't inspected the file contents for sensitivity. This option is also suitable when you can't configure the user and group permissions for the label that defines who gets access to the content. In this scenario, the business owners should control access by using SharePoint permissions and access management capabilities. However, this label configuration provides more protection because the downloaded copy of the file is permissioned the same as its source copy in real time. |
Both options provide a baseline level of protection that's specific to the document library, doesn't require content inspection, and doesn't rely on action from end users.
The SharePoint site admin can select a default label for the document library.
In your SharePoint site, select Documents > Settings icon > Library settings > More library settings.
In Default sensitivity labels (Apply label to items in this list or library):
a. For a standard default sensitivity label, from the drop-down box, select a sensitivity label that's suitable for most of the files in the library. It can be a sensitivity label that is configured for admin-defined permissions, such as Confidential \ All Employees. Or, a sensitivity label that doesn't apply encryption, such as Public. Don't select Extend protection on download, copy, or move.
b. For a default sensitivity label that extends protection to files that are downloaded, copied, or moved, select Extend protection on download, copy, or move. Then from the drop-down box, select a sensitivity label that is configured for user-defined permissions, such as Confidential \ Trusted People.
Note
The Extend protection on download, copy, or move checkbox isn't displayed until the prerequisite PowerShell commands are complete.
Save your changes.
To learn more, including how to run the PowerShell commands for the checkbox, details about the labeling outcomes for each configuration, and any limitations:
- Configure a default sensitivity label for a SharePoint document library
- Configure SharePoint with a sensitivity label to extend permissions to downloaded documents
6. Automatically apply sensitivity labels to files and emails
You can automatically apply labels to files in SharePoint sites, OneDrive accounts, Exchange emails, and Office files. Automatic labeling helps to identify a higher priority label for more sensitive information that might need a more restrictive setting than a default label.
- For the specific steps and information that you need to know, including learning about simulation mode for autolabeling policies, see Apply a sensitivity label to content automatically.
Client-side autolabeling vs. service-side autolabeling
- When you autolabel documents and emails in use by Word, Excel, PowerPoint, and Outlook, it's using client-side autolabeling. Users see the label automatically applied in their Office apps, or you can recommend the appropriate label to the user.
- When you autolabel documents stored in all SharePoint or OneDrive sites, and all emails sent using Exchange Online, it's using service-side autolabeling. There isn't any user interaction. You can label at scale for files at rest in OneDrive and SharePoint, and all emails that are sent and received.
If you created the default sensitivity labels and policies, they include both client-side autolabeling and service-side autolabeling to detect credit card numbers and personal data. These default settings make it easy for you to test the autolabeling functionality.
You can edit or create your own autolabeling settings to help identify your organization data that needs a specific sensitivity label to apply protection actions, like encryption.
Detect sensitive information and protect it from unauthorized sharing or leakage
✅ Use data loss prevention (DLP) policies to help protect against unintentional sharing
Microsoft Purview Data Loss Prevention (DLP) helps organizations protect sensitive information by helping guard against unauthorized sharing or leakage. The intent is to dynamically protect sensitive information, like financial data, social security numbers, and health records, from being overshared.
You can create DLP policies to protect sensitive information in the following locations:
- Microsoft 365 services, like Teams, Exchange, SharePoint, and OneDrive accounts
- Office applications, like Word, Excel, and PowerPoint
- Windows 10, Windows 11, and macOS (three latest released versions) endpoints
- Non-Microsoft cloud apps
- On-premises file shares and on-premises SharePoint
- Fabric and Power BI
When DLP policies find this data, it can act and help prevent the data from showing up in Microsoft 365 Copilot results. It can also help prevent items that have specific sensitivity labels applied from being summarized by Copilot.
To learn more, see:
- Create and Deploy data loss prevention policies
- Learn about the Microsoft 365 Copilot policy location
With DLP policies, you can use trainable classifiers, sensitive information types, sensitivity labels, and retention labels to identify sensitive information across your organization.
This section introduces you to the DLP policy creation process. DLP policies are a powerful tool. Make sure you:
- Understand the data you're protecting and the goals you want to achieve.
- Take time to design a policy before you implement it. You want to avoid any unintended issues. It's not recommended to create a policy, and then only tune the policy by trial-and-error.
- Work through Data loss prevention - Before you begin before you start designing a policy. This step helps you understand the concepts and the tools you use to create and manage DLP policies.
1. Open the Microsoft Purview portal
- Sign into the Microsoft Purview portal as one of the admins listed at Create and deploy DLP policies - Permissions.
- Select Solutions > Data Loss Prevention.
2. Create DLP policies
For Exchange Online, SharePoint Online, and OneDrive, you can use DLP to identify, monitor, and automatically protect sensitive information across emails and files, including files stored in Microsoft Teams file repositories.
- For the steps, see Design a DLP policy and Create and Deploy data loss prevention policies.
3. Create a DLP policy for Teams
By default, Purview includes some policies for Teams that you can enable. These policies are a quick way to get started with protecting information in Teams.
These policies can detect when sensitive info, like bank account numbers or passport numbers, are shared in Teams messages. Then, you can create policy tips to educate users or add actions that control sharing.
In Data Loss Prevention, select Overview.
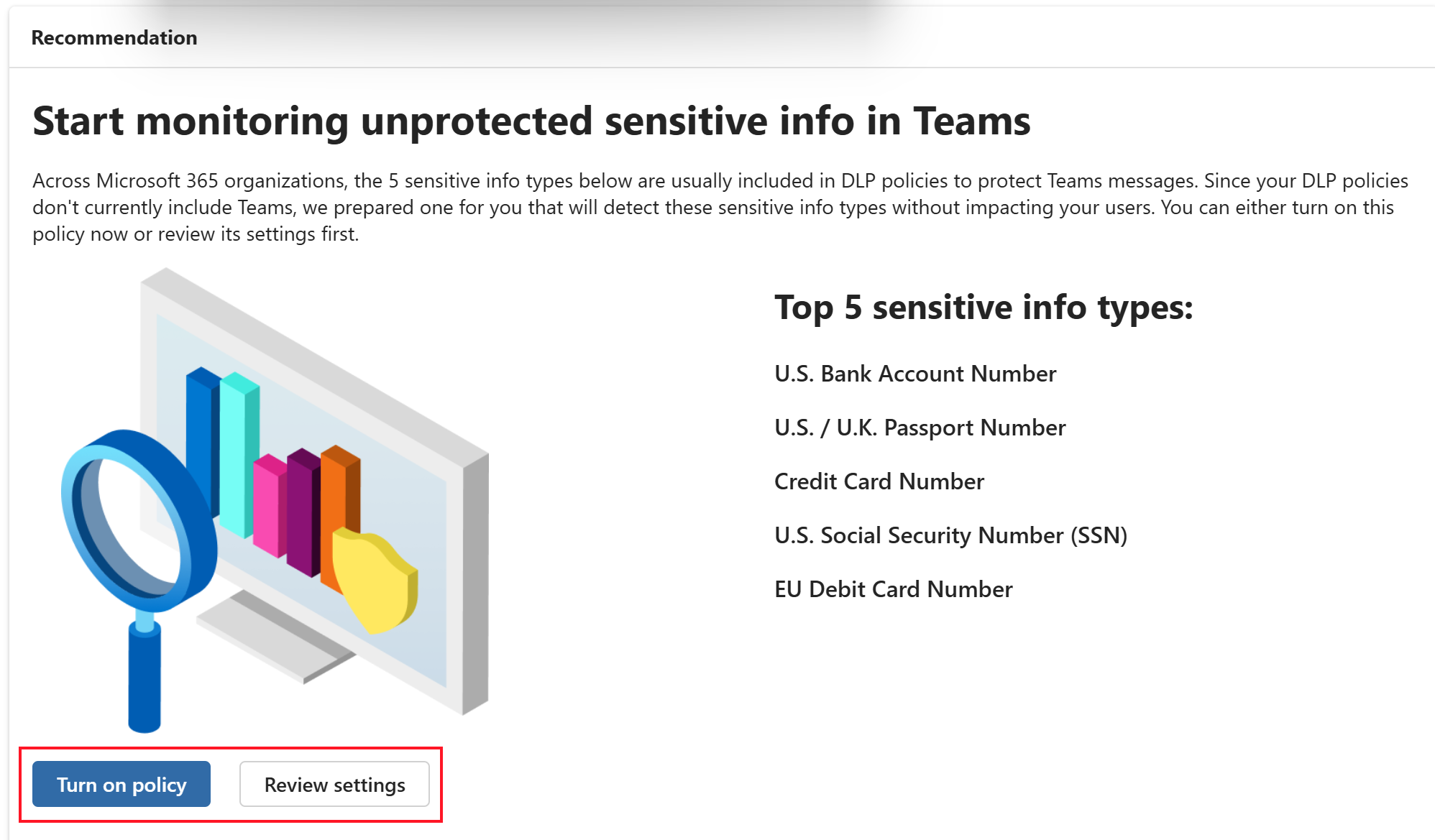
Scroll down to see the following policies:
- Start monitoring unprotected sensitive info in Teams
- Automatically configure Teams DLP policies to protect files shared in team messages
You can turn on these policies and also review the settings in the policy:
For more information on using DLP policies to protect information in Teams, see:
- Learn about the default data loss prevention policy for Microsoft Teams
- Data Loss Prevention and Microsoft Teams
4. Create an endpoint DLP policy for your Windows and macOS devices
Endpoint data loss prevention (Endpoint DLP) extends DLP monitoring and protection capabilities to sensitive items that are physically stored on Windows 10/11 and macOS (the three latest released major versions) devices.
DLP can monitor and take protective actions on user activities, like:
- Copy to USB removable device
- Copy to a network share
- Upload to a restricted cloud service domain or access from an unallowed browser
These activities are only some of the activities that DLP can monitor and protect. For a full list, see Learn about Endpoint Data Loss Prevention.
For more information on the prerequisites and steps to create an endpoint DLP policy, see:
- Get started with endpoint data loss prevention
- Onboard Windows devices into Microsoft 365 overview
- Onboard macOS devices into Microsoft 365 overview.
Note
If you use a mobile device managment (MDM) service to manage and help protect you devices, like Microsoft Intune, then keep using your MDM provider. The endpoint DLP policies focus on data loss prevention with your Microsoft 365 data. MDM focuses on device management. You use them simulatenously.
5. Create Adaptive Protection
Adaptive Protection integrates information from Insider Risk Management with DLP. When insider risk identifies a user that's engaging in risky behavior, the user is dynamically assigned an insider risk level, like Elevated.
Adaptive Protection can automatically create DLP policies that help protect the organization against the risky behavior associated with the insider risk level. As the insider risk level changes for users, the DLP policies applied to users can also adjust.
Turn on Adaptive Protection:
Sign into the Microsoft Purview portal as one of the admins listed at Adaptive Protection - Permissions.
Select Solutions > Insider Risk Management > Adaptive Protection.
In Dashboard, select Quick setup.
Adaptive Protection - Quick Setup is the easiest and fastest way to get started with Adaptive Protection. It automatically creates and dynamically assigns the insider risk policies, DLP policies, and a Conditional Access policy.
When the risk level is met, the policies automatically adjust to match the new risk level.
You can also create a custom policy instead of using the quick setup. If you create a custom policy, then you must also create the DLP and Conditional Access policies.
To learn more, see Adaptive Protection policies.
6. Test and monitor your policies
For DLP policies, you can:
Test your policies using simulation mode. Simulation mode allows you to see the effect of an individual policy without enforcing the policy. Use it to find the items that match your policy.
Monitor your policies with alerts and built-in reports, including risky user activities outside of DLP policies.
To learn more, see:
When you enable Adaptive Protection and your policies are configured, you can get policy metrics, users with an assigned risk level, and the policies currently in-scope for the user.
To learn more, see:
Delete the content you don't need
✅ Use data lifecycle management for automatic data retention or deletion
Data lifecycle management uses retention policies and optionally, retention labels. They're typically used to retain content for compliance reasons and can also automatically delete stale information.
For example, your organization might have regulatory requirements that require you to keep content for a certain period of time. Or, you might have content that you want to delete because it's old, outdated, or no longer needed.
If you have stale data in your organization, create and use retention policies. These policies help Copilot return more accurate information from your documents and emails.
Retention policies can also retain Copilot prompts and responses for compliance requirements, even if users delete their Copilot activity. To learn more, see Learn about retention for Copilot & AI apps.
Settings in a retention policy apply at the container level, like a SharePoint site or an Exchange mailbox. These settings are automatically inherited by the data in that container. If you need exceptions for individual emails or documents, use retention labels. For example, you have a retention policy to delete data in OneDrive if the data is older than one year. But, users can apply retention labels to keep specific documents from automatic deletion.
To create retention policies, sign into the Microsoft Purview portal as a Compliance Administrator.
To learn more about the permissions, see Data Lifecycle Management - Permissions.
Select Solutions > Data Lifecycle Management > Policies > Retention policies.
Select New retention policy and follow the instructions. For more specific information, see Create and configure retention policies.
If needed, create and apply retention labels.
You can use either Data Lifecycle Management or Records Management to create the labels. Records management includes more configuration options, like a disposition review process. A disposition review is helpful if you need manual confirmation before items are automatically deleted.
Use Data Lifecycle Management for retention policies that manage automatic retention and deletion for Microsoft 365 workloads & Microsoft 365 Copilot interactions, and retention labels for any exceptions.
- From Data Lifecycle Management, select Retention labels > Create a label.
Follow the configuration instructions and if you need more help, see How to create retention labels for data lifecycle management.
After you create the retention labels, you can then apply the labels to documents and emails:
If you applied retention labels, monitor them to see how they're being used.
Sign into the Microsoft Purview portal as one of the admins listed at:
Use Content explorer to get information on the items using retention labels.
There are a few ways to open Content Explorer:
- Data Loss Prevention > Explorers
- Records Management > Explorers
- Information protection > Explorers
Use activity explorer to get a historical view of activities on your content that has retention labels. There are different filters you can use.
There are a few ways to open activity explorer:
- Data Lifecycle Management > Explorers
- Records Management > Explorers
- Data Loss Prevention > Explorers
- Information protection > Explorers
To learn more, see:
- Learn about retention policies and retention labels
- Common settings for retention policies and retention label policies
Detect sensitive data and noncompliant content in Copilot interactions
✅ Create Communication Compliance policies to monitor interactions with Microsoft 365 Copilot
Communication Compliance can detect, capture, and act on potentially inappropriate messages in your organization. The inappropriate content includes sensitive or confidential information, harassing or threatening language, and sharing of adult content.
Communication Compliance comes with some predefined policies that help you get started. We recommend you use these predefined templates. You can also create your own custom policies.
These policies monitor and evaluate prompts and responses with Copilot.
Sign into the Microsoft Purview portal as one of the admins listed at Communication Compliance - Permissions.
Select Solutions > Communication Compliance > Overview.
If there are some required steps listed, then complete them. To learn more about these steps, see Set up and create communication compliance policy.
For the predefined policies, select Create policy > Detect Microsoft 365 Copilot interactions:
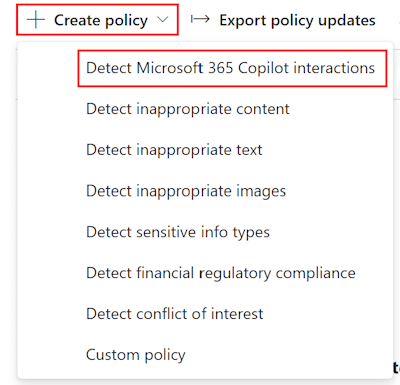
This Copilot policy helps you get started. There are also other predefined templates you can use. At any time, you can also create your own custom policies.
To learn more, see:
Monitor your policies. Regularly review the policy reports and audit logs to see any policy matches & resolved items, including activity by users.
To learn more, see Use communication compliance reports and audits.
To learn more, see:
- Learn about communication compliance
- Get started with communication compliance
- Create Communication Compliance policies
Review and analyze Copilot prompts and responses
✅ Use Data Security Posture Management (DSPM) for AI or eDiscovery to analyze Copilot user prompts and responses
When users enter a prompt and get a response from Copilot, you can view and search these interactions. Specifically, these features help you:
- Find sensitive information or inappropriate content included in Copilot activities.
- Respond to a data spillage incident when confidential or malicious information is released through Copilot-related activity.
- With eDiscovery, you can remove sensitive information or inappropriate content included in Copilot activities.
There are two ways to review and analyze Copilot prompts and responses - Data Security Posture Management for AI and eDiscovery.
Data Security Posture Management (DSPM) for AI (previously called AI Hub) is a central location in the Microsoft Purview portal that proactively monitors AI use. It includes eDiscovery and you can use it to analyze and review Copilot prompts and responses.
- Sign into the Microsoft Purview portal as an admin in one of the groups listed at Data Security Posture Management for AI - Permissions.
- Select Solutions > DSPM for AI > Activity explorer.
- Select an existing activity in the list. For example, if there's a Sensitive info types activity, select it.
- Select View related AI interaction activity. In Interaction details, you can see the app, and the prompt & response. You can also export an activity.
To learn more, see:
Technical and deployment resources available to you
Organizations with a minimum number of Copilot licenses are eligible for a Microsoft co-investment in deployment and adoption through eligible Microsoft Partners.
To learn more, see Microsoft 365 Copilot Partner Directory.
Eligible customers can request technical and deployment assistance from Microsoft FastTrack. FastTrack provides guidance and resources to help you plan, deploy, and adopt Microsoft 365.
To learn more, see FastTrack for Microsoft 365.
