Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure Container Apps operate in the context of an environment, which runs its own virtual network. As you create an environment, there are a few key considerations that inform the networking capabilities of your container apps:
Environment selection
Container Apps has two different environment types, which share many of the same networking characteristics with some key differences.
| Environment type | Supported plan types | Description |
|---|---|---|
| Workload profiles (default) | Consumption, Dedicated | Supports user defined routes (UDR), egress through NAT Gateway, and creating private endpoints on the container app environment. The minimum required subnet size is /27. |
| Consumption only (legacy) | Consumption | Doesn't support user defined routes (UDR), egress through NAT Gateway, peering through a remote gateway, or other custom egress. The minimum required subnet size is /23. |
For more information see Environment types.
Virtual network type
By default, Container Apps are integrated with the Azure network, which is publicly accessible over the internet and only able to communicate with internet accessible endpoints. You also have the option to provide an existing VNet as you create your environment instead. Once you create an environment with either the default Azure network or an existing VNet, the network type can't be changed.
Use an existing VNet when you need Azure networking features like:
- Network Security Groups
- Application Gateway integration
- Azure Firewall integration
- Control over outbound traffic from your container app
- Access to resources behind private endpoints in your virtual network
If you use an existing VNet, you need to provide a subnet that is dedicated exclusively to the Container App environment you deploy. This subnet isn't available to other services. For more information see Virtual network configuration.
Accessibility level
You can configure whether your container app allows public ingress or ingress only from within your VNet at the environment level.
| Accessibility level | Description |
|---|---|
| External | Allows your container app to accept public requests. External environments are deployed with a virtual IP on an external, public facing IP address. |
| Internal | Internal environments have no public endpoints and are deployed with a virtual IP (VIP) mapped to an internal IP address. The internal endpoint is an Azure internal load balancer (ILB) and IP addresses are issued from the existing VNet's list of private IP addresses. |
Public network access
The public network access setting determines whether your container apps environment is accessible from the public Internet. Whether you can change this setting after creating your environment depends on the environment's virtual IP configuration. The following table shows valid values for public network access, depending on your environment's virtual IP configuration.
| Virtual IP | Supported public network access | Description |
|---|---|---|
| External | Enabled, Disabled |
The container apps environment was created with an Internet-accessible endpoint. The public network access setting determines whether traffic is accepted through the public endpoint or only through private endpoints, and the public network access setting can be changed after creating the environment. |
| Internal | Disabled |
The container apps environment was created without an Internet-accessible endpoint. The public network access setting can't be changed to accept traffic from the Internet. |
In order to create private endpoints on your Azure Container App environment, public network access must be set to Disabled.
Azure networking policies are supported with the public network access flag.
Ingress configuration
Under the ingress section, you can configure the following settings:
Ingress: You can enable or disable ingress for your container app.
Ingress traffic: You can accept traffic to your container app from anywhere, or you can limit it to traffic from within the same Container Apps environment.
Traffic split rules: You can define traffic splitting rules between different revisions of your application. For more information, see Traffic splitting.
For more information about different networking scenarios, see Ingress in Azure Container Apps.
Inbound features
| Feature | Learn how to |
|---|---|
| Ingress Configure ingress |
Control the routing of external and internal traffic to your container app. |
| Premium ingress | Configure advanced ingress settings such as workload profile support for ingress and idle timeout. |
| IP restrictions | Restrict inbound traffic to your container app by IP address. |
| Client certificate authentication | Configure client certificate authentication (also known as mutual TLS or mTLS) for your container app. |
| Traffic splitting Blue/Green deployment |
Split incoming traffic between active revisions of your container app. |
| Session affinity | Route all requests from a client to the same replica of your container app. |
| Cross origin resource sharing (CORS) | Enable CORS for your container app, which allows requests made through the browser to a domain that doesn't match the page's origin. |
| Path-based routing | Use rules to route requests to different container apps in your environment, depending on the path of each request. |
| Virtual networks | Configure the VNet for your container app environment. |
| DNS | Configure DNS for your container app environment's VNet. |
| Private endpoint | Use a private endpoint to securely access your Azure Container App without exposing it to the public Internet. |
| Integrate with Azure Front Door | Connect directly from Azure Front Door to your Azure Container Apps using a private link instead of the public internet. |
Outbound features
| Feature | Learn how to |
|---|---|
| Using Azure Firewall | Use Azure Firewall to control outbound traffic from your container app. |
| Virtual networks | Configure the VNet for your container app environment. |
| Securing a existing VNet with an NSG | Secure your container app environment's VNet with a Network Security Group (NSG). |
| NAT gateway integration | Use NAT Gateway to simplify outbound internet connectivity in your virtual network in a workload profiles environment. |
Tutorials
| Tutorial | Learn how to |
|---|---|
| Use a virtual network | Use a virtual network. |
| Configure WAF Application Gateway | Configure a WAF application gateway. |
| Enable User Defined Routes (UDR) | Enable user defined routes (UDR). |
| Use Mutual Transport Layer Security (mTLS) | Build an mTLS application in Azure Container Apps. |
| Use a private endpoint | Use a private endpoint to securely access your Azure Container App without exposing it to the public Internet. |
| Integrate with Azure Front Door | Connect directly from Azure Front Door to your Azure Container Apps using a private link instead of the public internet. |
Environment security
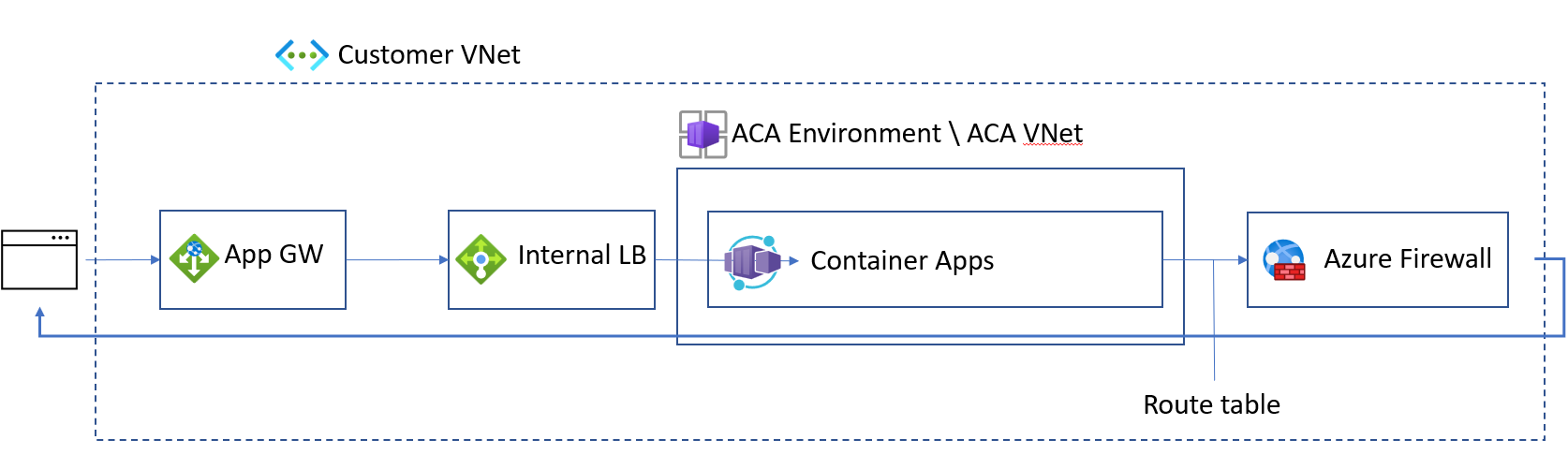
You can fully secure your ingress and egress networking traffic workload profiles environment by taking the following actions:
Create your internal container app environment in a workload profiles environment. For steps, refer to Manage workload profiles with the Azure CLI.
Integrate your Container Apps with an Application Gateway.
Configure UDR to route all traffic through Azure Firewall.
HTTP edge proxy behavior
Azure Container Apps uses an edge HTTP proxy that terminates Transport Layer Security (TLS) and routes requests to each application.
HTTP applications scale based on the number of HTTP requests and connections. Envoy routes internal traffic inside clusters.
Downstream connections support HTTP1.1 and HTTP2 and Envoy automatically detects and upgrades connections if the client connection requires an upgrade.
Upstream connections are defined by setting the transport property on the ingress object.
Portal dependencies
For every app in Azure Container Apps, there are two URLs.
The Container Apps runtime initially generates a fully qualified domain name (FQDN) used to access your app. See the Application Url in the Overview window of your container app in the Azure portal for the FQDN of your container app.
A second URL is also generated for you. This location grants access to the log streaming service and the console. If necessary, you may need to add https://azurecontainerapps.dev/ to the allowlist of your firewall or proxy.
Ports and IP addresses
The following ports are exposed for inbound connections.
| Protocol | Port(s) |
|---|---|
| HTTP/HTTPS | 80, 443 |
IP addresses are broken down into the following types:
| Type | Description |
|---|---|
| Public inbound IP address | Used for application traffic in an external deployment, and management traffic in both internal and external deployments. |
| Outbound public IP | Used as the "from" IP for outbound connections that leave the virtual network. These connections aren't routed down a VPN. Outbound IPs may change over time. Using a NAT gateway or other proxy for outbound traffic from a Container Apps environment is only supported in a workload profiles environment. |
| Internal load balancer IP address | This address only exists in an internal environment. |