При создании конфиденциальных клиентских приложений управление учетными данными является критически важным. В этой статье объясняется, как добавить клиентские сертификаты, федеративные учетные данные или клиентские секреты в регистрацию приложения в Microsoft Entra. Эти учетные данные позволяют приложению безопасно проходить проверку подлинности и получать доступ к веб-API без взаимодействия с пользователем.
Предпосылки
Быстрый старт: Регистрация приложения в Microsoft Entra ID.
Добавление учетных данных в приложение
При создании учетных данных для конфиденциального клиентского приложения:
Корпорация Майкрософт рекомендует использовать сертификат вместо секрета клиента перед перемещением приложения в рабочую среду. Дополнительные сведения об использовании сертификата см. в инструкциях учетные данные сертификата аутентификации приложения платформы идентификации Майкрософт.
В целях тестирования можно создать самозаверяющий сертификат и настроить приложения для проверки подлинности с его помощью. Однако в производственной среденеобходимо приобрести сертификат, подписанный известным центром сертификации, а затем использовать Azure Key Vault для управления доступом к сертификату и сроком действия.
Дополнительные сведения об уязвимостях секрета клиента см. в разделе "Как отказаться от аутентификации на основе секретов".
Иногда называется открытым ключом, поэтому сертификат является рекомендуемым типом учетных данных, так как они считаются более безопасными, чем секреты клиента.
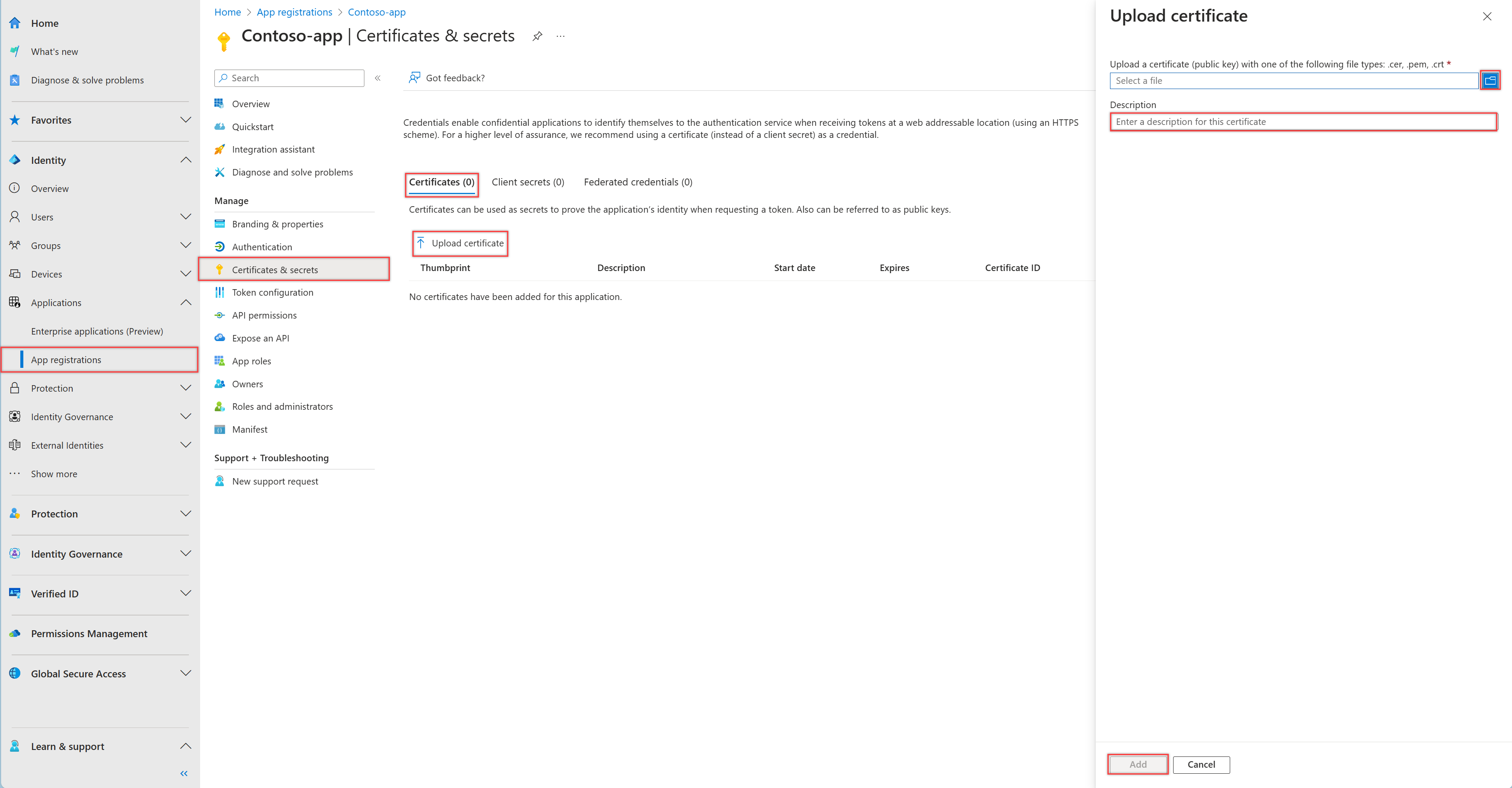
В Центре администрирования Microsoft Entra в Регистрация приложений выберите свое приложение.
Выберите Сертификаты и секреты>Сертификаты>Загрузить сертификат.
Выберите отправляемый файл. Он должен быть одного из следующих типов файлов: CER, PEM, CRT.
Нажмите кнопку "Добавить".
Запишите отпечаток сертификата для использования в коде клиентского приложения.
Иногда называется паролем приложения, секрет клиента — это строковое значение, которое приложение может использовать вместо сертификата для идентификации себя.
Секреты клиентов являются менее безопасными, чем сертификаты или федеративные учетные данные, поэтому не следует использовать в рабочих средах. Хотя они могут быть удобными для разработки локальных приложений, необходимо использовать сертификаты или федеративные учетные данные для любых приложений, работающих в рабочей среде, чтобы обеспечить более высокую безопасность.
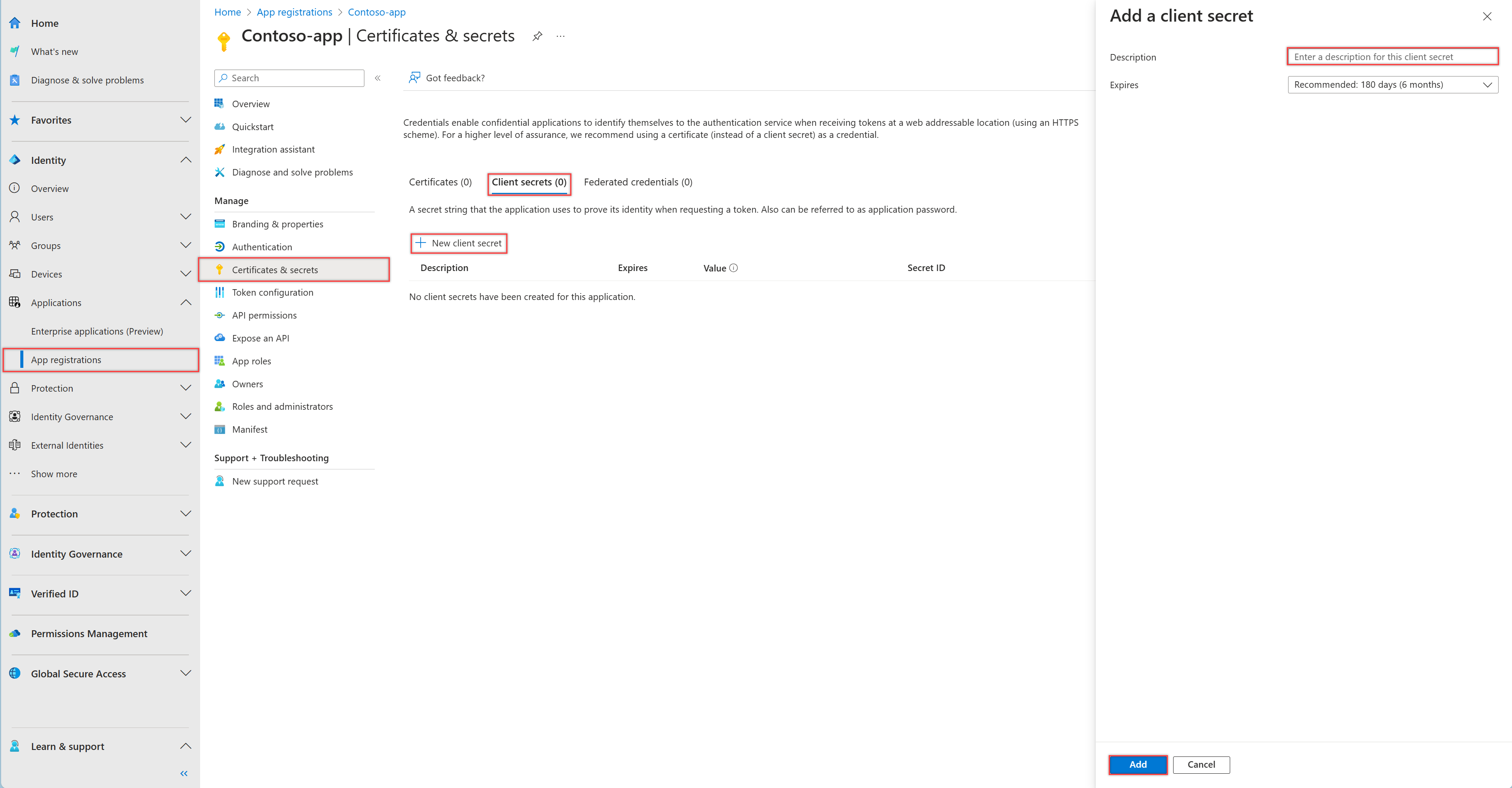
В Центре администрирования Microsoft Entra в Регистрация приложений выберите свое приложение.
Выберите Сертификаты и секреты>Секреты клиента>Создать секрет клиента.
Добавьте описание секрета клиента.
Выберите срок истечения действия секрета или укажите пользовательский срок его существования.
- Срок жизни секрета клиента ограничен двумя годами (24 месяцами) или меньше. Вы не можете указать настраиваемое время существования дольше 24 месяцев.
- Корпорация Майкрософт рекомендует задать значение срока действия менее 12 месяцев.
Нажмите кнопку "Добавить".
Запишите значение секрета клиента для использования в коде клиентского приложения. Это значение секрета больше нигде не отображается после закрытия страницы.
Замечание
Если вы используете подключение службы Azure DevOps, которое автоматически создает сервисный принципал, необходимо обновить секрет клиента через сайт портала Azure DevOps вместо обновления секрета клиента напрямую. См. этот документ о том, как обновить секрет клиента на сайте портала Azure DevOps: устранение неполадок с подключениями к службе Azure Resource Manager.
Федеративные учетные данные идентичности — это тип учетных данных, которые позволяют рабочим нагрузкам, таким как GitHub Actions, Kubernetes, или тем, которые выполняются на вычислительных платформах за пределами Azure, получать доступ к защищенным ресурсам Microsoft Entra без необходимости управлять секретами, используя федерацию идентичности рабочей нагрузки.
Чтобы добавить федеративные учетные данные, выполните следующие действия.
В Центре администрирования Microsoft Entra в Регистрация приложений выберите свое приложение.
Выберите Сертификаты и секреты>Федеративные учетные данные>Добавить учетные данные.
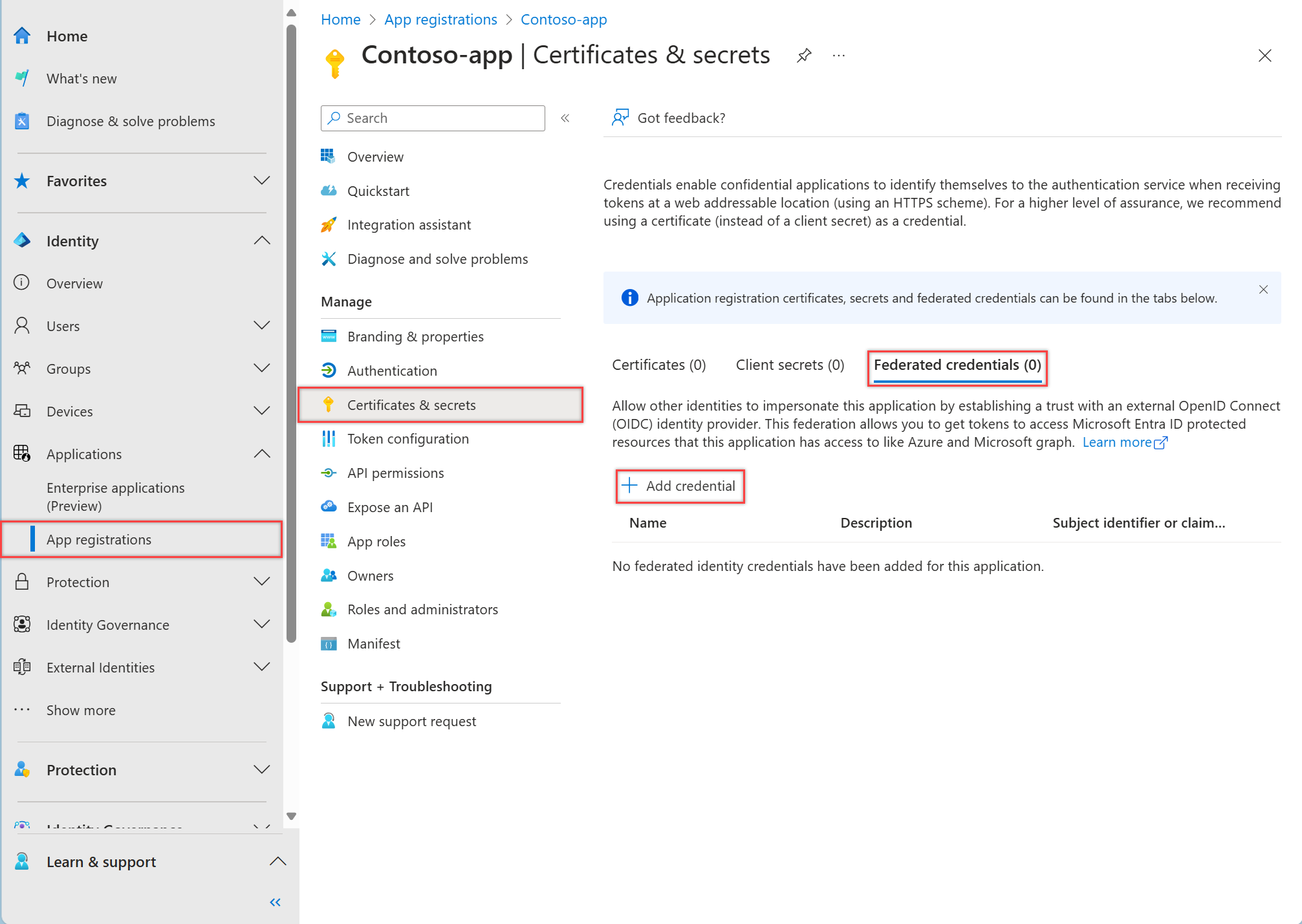
В раскрывающемся списке сценария федеративных учетных данных выберите один из поддерживаемых сценариев и следуйте соответствующим инструкциям, чтобы завершить настройку.
-
Управляемые клиентом ключи для шифрования данных в клиенте с помощью Azure Key Vault в другом клиенте.
-
Развёртывание ресурсов Azure с помощью действий GitHub для настройки рабочего процесса GitHub, чтобы получить токены для вашего приложения и развернуть ресурсы на Azure.
-
Доступ Kubernetes к ресурсам Azure для настройки учетной записи службы Kubernetes с целью получения токенов для вашего приложения и доступа к ресурсам Azure.
-
Другой издатель должен настроить приложение для доверия управляемой учетной записи или учетной записи, управляемой внешним поставщиком OpenID Connect, чтобы получить токены для вашего приложения и получить доступ к ресурсам Azure.
Дополнительные сведения о том, как получить маркер доступа с федеративными учетными данными, см. в платформе удостоверений Майкрософт и потоке учетных данных клиента OAuth 2.0.
Связанный контент


