Troubleshoot Windows Admin Center
This article describes how to diagnose and resolve issues in Windows Admin Center. If you're having an issue with a specific tool, check to see if you're experiencing a known issue.
Installer fails with message: The Module 'Microsoft.PowerShell.LocalAccounts' could not be loaded.
This failure can happen if your default PowerShell module path has been modified or removed. To resolve the issue, make sure that %SystemRoot%\system32\WindowsPowerShell\v1.0\Modules is the first item in your PSModulePath environment variable. You can achieve this with the following line of PowerShell:
[Environment]::SetEnvironmentVariable("PSModulePath","%SystemRoot%\system32\WindowsPowerShell\v1.0\Modules;" + ([Environment]::GetEnvironmentVariable("PSModulePath","User")),"User")
I get a This site/page can't be reached error in my web browser
If you've installed Windows Admin Center as an App on Windows 10
- Check to make sure Windows Admin Center is running. Look for the Windows Admin Center icon
 in the System tray or Windows Admin Center Desktop / SmeDesktop.exe in Task Manager. If not, launch Windows Admin Center from the Start menu.
in the System tray or Windows Admin Center Desktop / SmeDesktop.exe in Task Manager. If not, launch Windows Admin Center from the Start menu.
Note
After rebooting, you must launch Windows Admin Center from the Start menu.
Make sure you're using either Microsoft Edge or Google Chrome as your web browser.
Did you select the correct certificate on first launch?
- Try opening your browser in a private session - if that works, you'll need to clear your cache.
Did you recently upgrade Windows 10 to a new build or version?
- This may have cleared your trusted hosts settings. Follow these instructions to update your trusted hosts settings.
If you've installed Windows Admin Center as a Gateway on Windows Server
Check the Windows version of the client and server.
Make sure you are using either Microsoft Edge or Google Chrome as your web browser.
On the server, open Task Manager > Services and make sure ServerManagementGateway / Windows Admin Center is running.
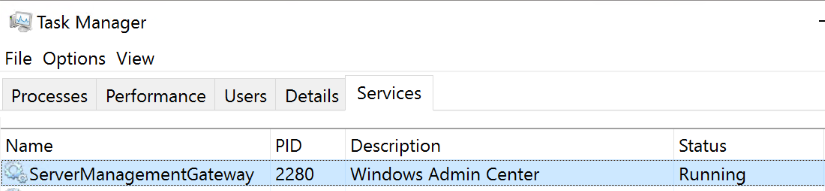
Test the network connection to the Gateway (replace <values> with the information from your deployment)
Test-NetConnection -Port <port> -ComputerName <gateway> -InformationLevel Detailed
If you have installed Windows Admin Center in an Azure Windows Server VM
- Check the Windows version.
- Did you add an inbound port rule for HTTPS?
- Learn more about installing Windows Admin Center in an Azure VM.
Check the Windows version
To check the Windows version:
Open the run dialog (Windows Key + R) and launch
winver.Check the version in the About Windows window.
If you're using Windows 10 version 1703 or earlier, Windows Admin Center isn't supported on your version of Microsoft Edge. Either upgrade to a recent version of Windows 10 or use Google Chrome.
If you're using an insider preview version of Windows 10 or Server with a build version between 17134 and 17637, Windows had a bug that caused Windows Admin Center to fail. Use a current supported version of Windows to fix this issue.
Make sure the Windows Remote Management (WinRM) service is running on both the gateway machine and managed node
Open the run dialog with WindowsKey + R.
Type
services.mscand press Enter.In the window that opens, look for Windows Remote Management (WinRM), make sure it is running and set to automatically start.
If you're getting WinRM error messages while managing servers in Windows Admin Center
WinRM doesn't allow credential delegation by default. To allow delegation, the computer needs to have Credential Security Support Provider (CredSSP) enabled temporarily.
If you're receiving WinRM error messages, try using the verification steps in the Manual troubleshooting section of Troubleshoot CredSSP to resolve them.
Did you upgrade your server from 2016 to 2019?
This may have cleared your trusted hosts settings. Follow these instructions to update your trusted hosts settings.
I get the message: "Can't connect securely to this page. This might be because the site uses outdated or unsafe TLS security settings."
Your machine is restricted to HTTP/2 connections. Windows Admin Center uses integrated Windows authentication, which is not supported in HTTP/2. Add the following two registry values under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Http\Parameters key on the machine running the browser to remove the HTTP/2 restriction:
EnableHttp2Cleartext=dword:00000000
EnableHttp2Tls=dword:00000000
I'm having trouble with the Remote Desktop, Events, and PowerShell tools.
These three tools require the web socket protocol, which is commonly blocked by proxy servers and firewalls. If you're using Google Chrome, there's a known issue with web sockets and NTLM authentication.
I can connect to some servers, but not others
Log on to the gateway machine locally and try to
Enter-PSSession <machine name>in PowerShell, replacing <machine name> with the name of the Machine you're trying to manage in Windows Admin Center.If your environment uses a workgroup instead of a domain, see using Windows Admin Center in a workgroup.
Using local administrator accounts: If you're using a local user account that isn't the built-in administrator account, you need to enable the policy on the target machine by running the following command in PowerShell or at a command prompt as Administrator on the target machine:
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1
I get this message: "You are not authorized to view this page. If you recently updated Windows Admin Center, you may need to restart your browser, and then refresh the page."
Make sure to select the Windows Admin Center Client certificate when prompted on the first launch, and not any other certificate. If you select any other certificate, you'll get this error message. To resolve this error, restart your browser and refresh the page, and select the Windows Admin Center Client certificate. If you continue to get the same error, try clearing the browser cache or switching to another browser. If none of these troubleshooting steps resolve the issue, you may need to uninstall and reinstall Windows Admin Center, and then restart it.
Using Windows Admin Center in a workgroup
What account are you using?
Make sure the credentials you're using are a member of the target server's local administrators group. In some cases, WinRM also requires membership in the Remote Management Users group. If you're using a local user account that is not the built-in administrator account, you will need to enable the policy on the target machine by running the following command in PowerShell or at a Command Prompt as Administrator on the target machine:
REG ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1
Are you connecting to a workgroup machine on a different subnet?
To connect to a workgroup machine that isn't on the same subnet as the gateway, make sure the firewall port for WinRM (TCP 5985) allows inbound traffic on the target machine. You can run the following command in PowerShell or at a Command Prompt as Administrator on the target machine to create this firewall rule:
Windows Server
Set-NetFirewallRule -Name WINRM-HTTP-In-TCP-PUBLIC -RemoteAddress AnyWindows 10
Set-NetFirewallRule -Name WINRM-HTTP-In-TCP -RemoteAddress Any
Configure TrustedHosts
When installing Windows Admin Center, you're given the option to let Windows Admin Center manage the gateway's TrustedHosts setting. This is required in a workgroup environment, or when using local administrator credentials in a domain. If you choose to forego this setting, you must configure TrustedHosts manually.
To modify TrustedHosts using PowerShell commands:
Open an Administrator PowerShell session.
View your current TrustedHosts setting:
Get-Item WSMan:\localhost\Client\TrustedHostsWarning
If the current setting of your TrustedHosts is not empty, the commands below will overwrite your setting. We recommend that you save the current setting to a text file with the following command so you can restore it if needed:
Get-Item WSMan:localhost\Client\TrustedHosts | Out-File C:\OldTrustedHosts.txtSet TrustedHosts to the NetBIOS, IP, or FQDN of the machines you intend to manage:
Set-Item WSMan:localhost\Client\TrustedHosts -Value '192.168.1.1,server01.contoso.com,server02'Tip
For an easy way to set all TrustedHosts at once, you can use a wildcard.
Set-Item WSMan:\localhost\Client\TrustedHosts -Value '*'When you are done testing, you can issue the following command from an elevated PowerShell session to clear your TrustedHosts setting:
Clear-Item WSMan:localhost\Client\TrustedHostsIf you had previously exported your settings, open the file, copy the values, and use this command:
Set-Item WSMan:localhost\Client\TrustedHosts -Value '<paste values from text file>'
I previously had Windows Admin Center installed, and now nothing else can use the same TCP/IP port
Manually run these two commands in an elevated command prompt:
netsh http delete sslcert ipport=0.0.0.0:443
netsh http delete urlacl url=https://+:443/
Azure features don't work properly in Microsoft Edge
Microsoft Edge has known issues related to security zones that affect Azure login in Windows Admin Center.
If you are having trouble using Azure features when using Microsoft Edge, perform these steps to add the required URLs:
Search for Internet Options in the Windows Start menu.
Go to the Security tab.
Under the Trusted sites option, click on the Sites button and add the following URLs in the dialog box that opens:
- Your gateway URL
https://login.microsoftonline.comhttps://login.live.com
Click Close and then click OK.
Update the Pop-up Blocker settings in Microsoft Edge:
Browse to edge://settings/content/popups?search=pop-up.
Under the Allow section, add the following URLs:
- Your gateway URL
https://login.microsoftonline.comhttps://login.live.com
Have an issue with an Azure-related feature?
Send us an email at [email protected] with the following information:
- General issue information from the questions listed below.
- Describe your issue and the steps you took to reproduce the issue.
- Did you previously register your gateway to Azure using the New-AadApp.ps1 downloadable script and then upgrade to version 1807? Or did you register your gateway to Azure using the UI from gateway Settings > Azure?
- Is your Azure account associated with multiple directories/tenants? If yes, when registering the Microsoft Entra application to Windows Admin Center, was the directory you used your default directory in Azure?
- Does your Azure account have access to multiple subscriptions?
- Does the subscription you were using have billing attached?
- Were you logged in to multiple Azure accounts when you encountered the issue?
- Does your Azure account require multi-factor authentication?
- Is the machine you're trying to manage an Azure VM?
- Is Windows Admin Center installed on an Azure VM?
Collect HAR files
An HTTP Archive Format (HAR) file is a log of a web browser's interaction with a site. This information is crucial for troubleshooting and debugging.
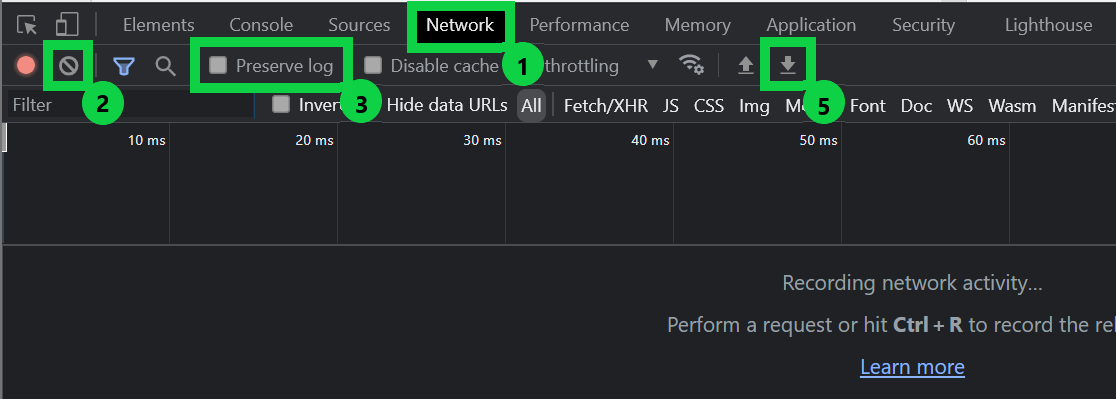
To collect a HAR file in Microsoft Edge or Google Chrome, follow these steps:
Press F12 to open Developer Tools window, and then click the Network tab.
Select the Clear icon to clean up network log.
Click to select the Preserve Log check box.
Reproduce the issue.
After reproducing the issue, click on Export HAR.
Specify where to save the log and click Save.
Warning
Before sharing your HAR files with Microsoft, ensure that you remove or obfuscate any sensitive information, like passwords.
Provide feedback on issues
Go to Event Viewer > Application and Services > Microsoft-ServerManagementExperience and look for any errors or warnings.
File a bug on GitHub that describes your issue.
Include any errors or warning you find in the event log, and the following information:
- Platform where Windows Admin Center is installed (Windows 10 or Windows Server):
- If installed on Server, what is the Windows version of the machine running the browser to access Windows Admin Center:
- Are you using the self-signed certificate created by the installer?
- If you're using your own certificate, does the subject name match the machine?
- If you're using your own certificate, does it specify an alternate subject name?
- Did you install with the default port setting?
- If not, which port did you specify?
- Is the machine where Windows Admin Center is installed joined to a domain?
- Windows version where Windows Admin Center is installed:
- Is the machine that you're trying to manage joined to a domain?
- Windows version of the machine that you're trying to manage:
- What browser are you using?
- If you're using Google Chrome, what is the version? (Help > About Google Chrome)