What is Microsoft's unified security operations platform?
Microsoft's unified security operations platform provides a single platform for end-to-end security operations (SecOps). It integrates security information and event management (SIEM), security orchestration, automation, and response (SOAR), extended detection and response (XDR), posture and exposure management, cloud security, threat intelligence, and generative AI solutions.
To cover all those capabilities, Microsoft's unified SecOps platform combines services like Microsoft Defender XDR, Microsoft Sentinel, Microsoft Security Exposure Management, and Microsoft Security Copilot in the Microsoft Defender portal. Integrate more Microsoft Defender services to add security and provide integrated protection against sophisticated attacks. The Defender portal provides a single location to monitor, detect, investigate, remediate, and respond against pre- and post-breach cybersecurity risks and threats.
Protect assets
Protect a wide range of assets by integrating Defender XDR, Microsoft Sentinel, and other Defender services in Microsoft's unified SecOps platform.
Microsoft Defender XDR services include the following asset protection capabilities:
| Capability | Security product |
|---|---|
| Identify, detect, and investigate Microsoft Entra ID threats. | Microsoft Defender for Identity |
| Protect against threats posed by email messages, URL links, and Office 365 collaboration tools. | Microsoft Defender for Office 365 |
| Monitor and protect endpoint devices. Monitor, detect, and investigate device breaches, and automatically respond to security threats. | Microsoft Defender for Endpoint |
| Identify and protect operational technology (OT) and IT resources by extending Defender XDR protection to OT environments. | Microsoft Defender for IoT |
| Identify assets and software inventory, and assess device posture to find security vulnerabilities. | Microsoft Defender Vulnerability Management |
| Protect and control access to SaaS cloud apps. | Microsoft Defender for Cloud Apps |
Asset protection for services not licensed with Microsoft Defender XDR includes the following capabilities:
| Capability | Security product |
|---|---|
| Monitor and protect non-Microsoft and on-premises devices, services, and solutions. | Microsoft Sentinel |
| Discover and assess assets, and remediate risk to reduce attack surfaces. | Microsoft Security Exposure Management |
| Improve multicloud and on-premises security posture, and protect cloud workloads against threats. | Microsoft Defender for Cloud |
Simplify security management
Combine Microsoft security services like Defender XDR, Microsoft Sentinel, and more for end-to-end pre- and post-breach protection of endpoints, identities, cloud apps and workloads, and email across your organization.
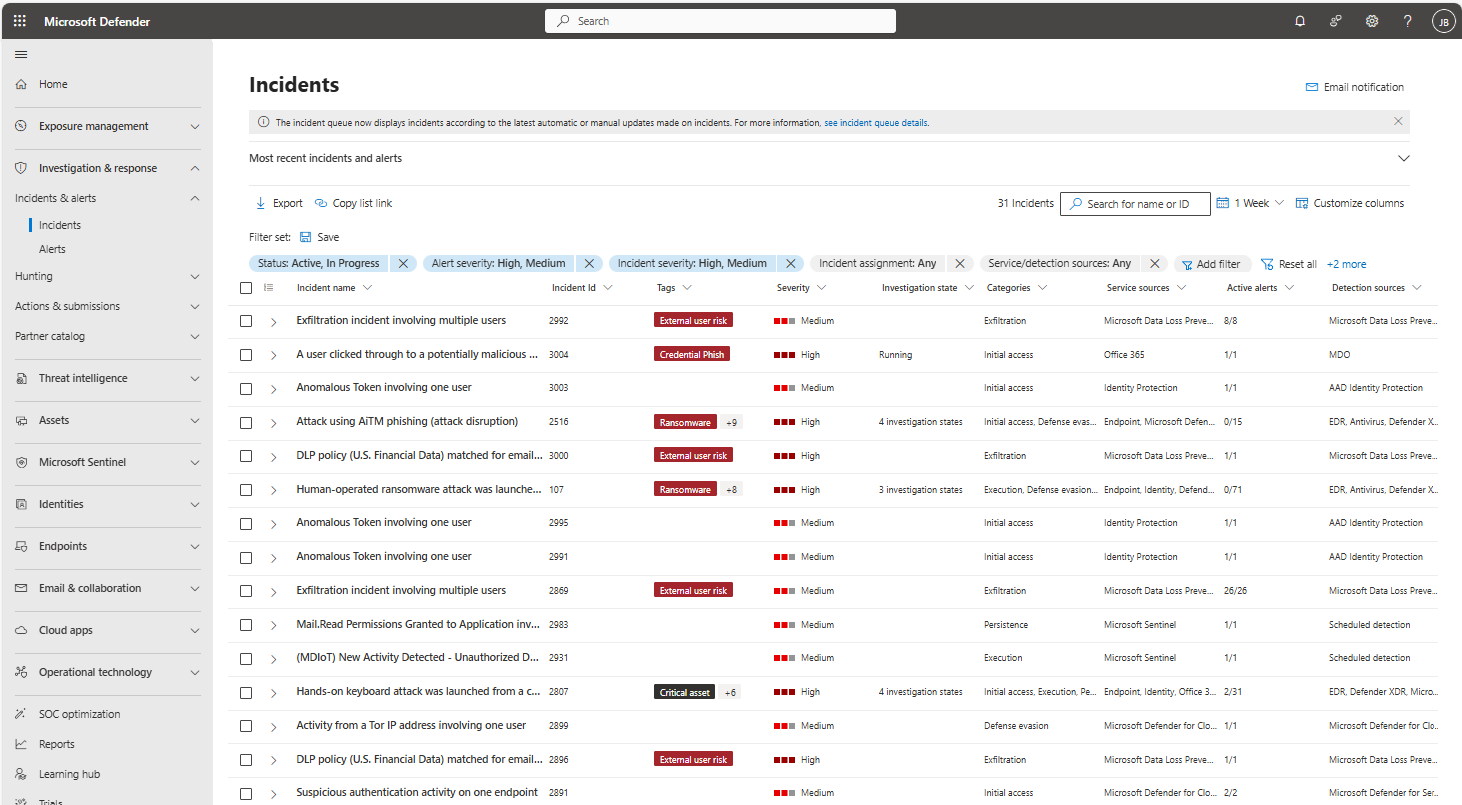
The Defender portal provides a single, centralized view of organizational security posture and threat detections and response. It provides a combined incidents queue that groups together information about security risks and breaches.
Free up analyst time as unified security dashboards enable analysts to cross organization silos, prioritize the most critical threats, and hunt effectively for attempted breaches.
The following image shows the unified incident queue in Microsoft's unified SecOps platform, with incidents from multiple service sources.
Reduce security risk and prevent attacks
Consistently reduce security risk and prevent cybersecurity attacks as a part of your organizational risk management framework. Microsoft's unified SecOps platform offers comprehensive exposure management and cloud protection capabilities. With Microsoft Security Exposure Management, and Microsoft Defender for Cloud:
- Continuously discover organizational assets and assess their security posture.
- Protect cloud workloads from code to runtime.
- Aggregate data and threat intelligence to discover security gaps and weaknesses, including analysis of potential attack paths.
- Investigate and query to get insights into security posture.
- Prioritize asset remediation, with the focus on critical resources, to reduce security gaps and attack surfaces.
The following image shows the overview page for exposure management in Microsoft's unified SecOps platform.
Reduce threat detection and response times
Standard cybersecurity metrics focus on the time to detect (TTD) and time to respond (TTR). Time to detect (TTD) measures how long it takes security teams to discover an incident. Time to respond (TTR) measures the amount of time it takes to respond after a threat is detected. The shorter the TTD and TTR, the more effective your detection, and response strategy is.
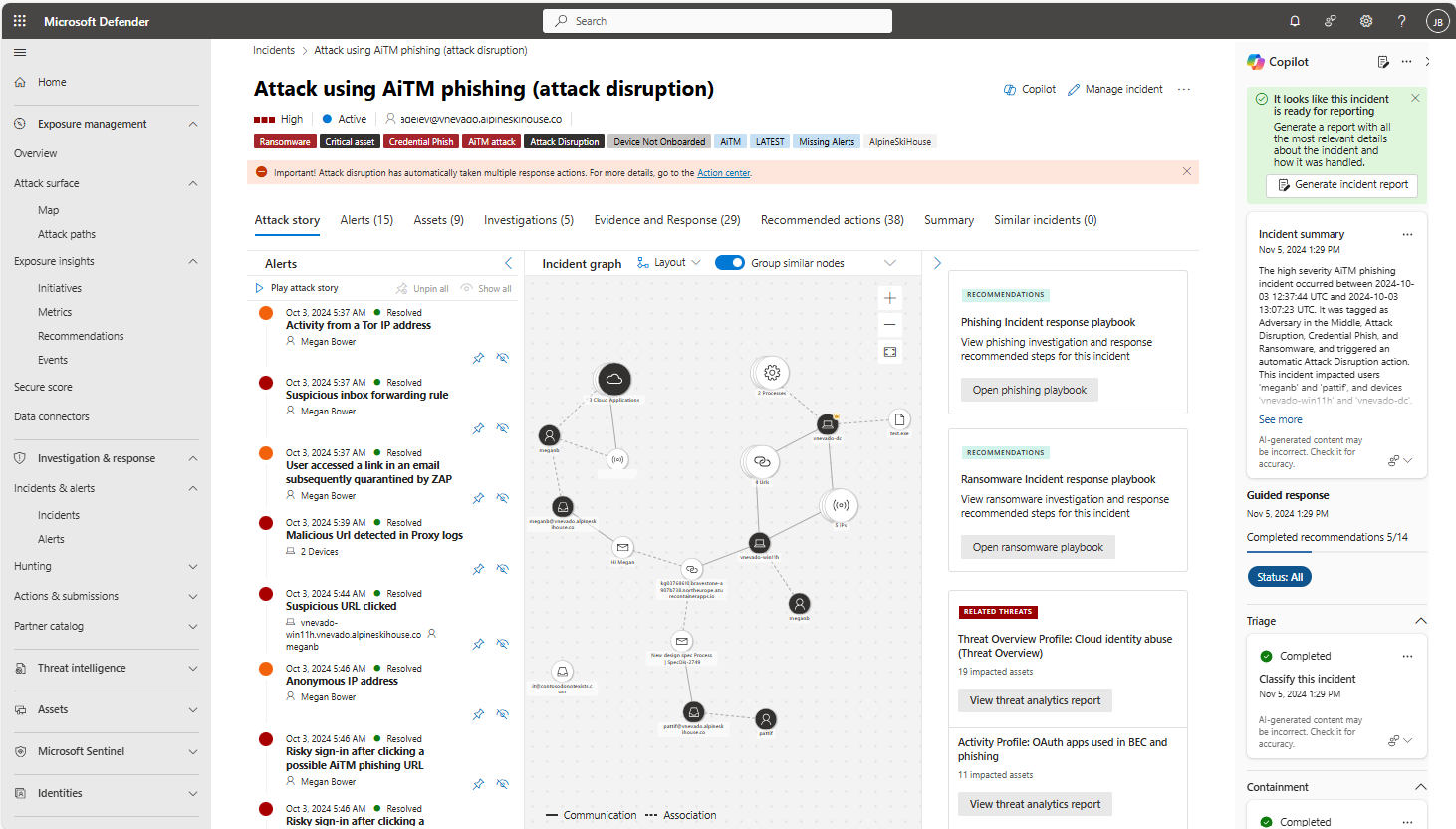
Microsoft's unified SecOps platform correlates millions of signals from Defender products, Microsoft Sentinel, Microsoft security research, and threat intelligence to identify attacks in progress. It initiates automatic attack disruption to automatically contain attacks, limiting lateral movement early and reducing attack impact. Automatic attack disruption helps to reduce costs associated with loss of productivity, provide control to the SecOps team control to investigate and remediate compromised assets.
Automatic attack disruption responds to threats by containing devices and containing or disabling users to mitigate attacks.
The following image shows an example of an incident where automatic attack disruption was triggered.
For more information, see Automatic attack disruption in Microsoft Defender XDR.
Transform SOC productivity with AI
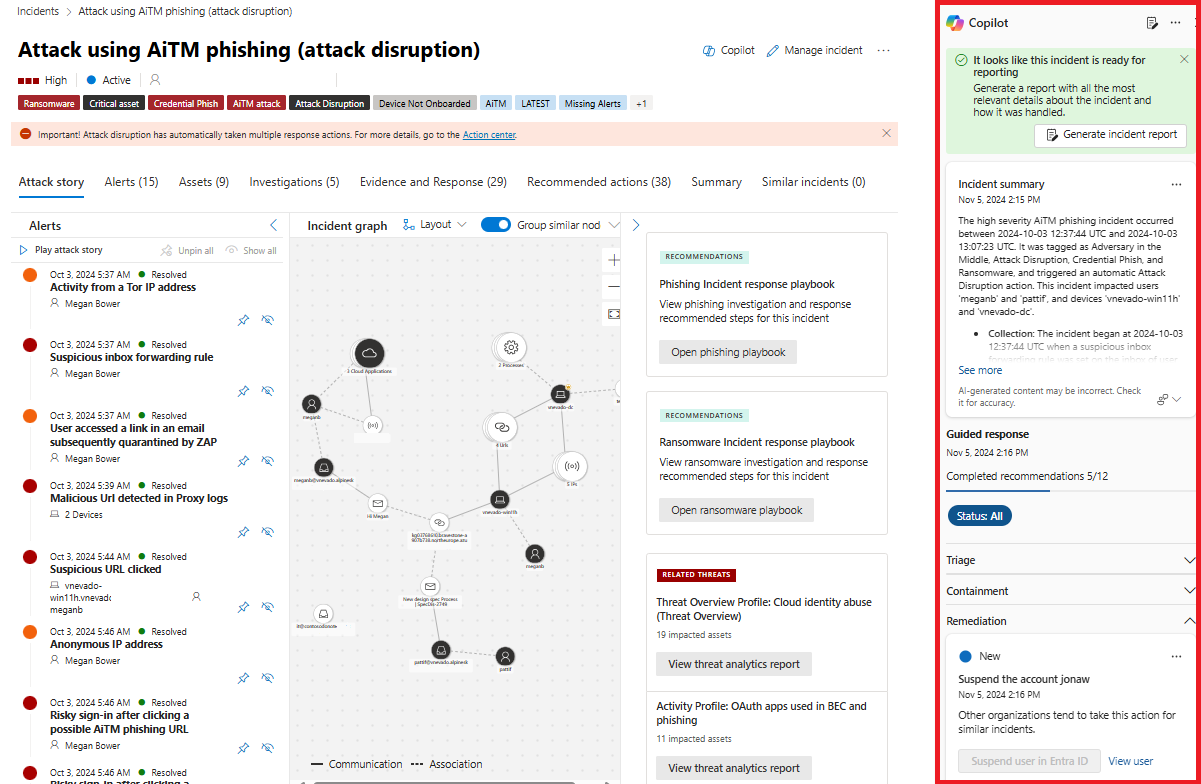
Microsoft Security Copilot brings together the power of AI and human expertise to help your SOC team respond to attacks faster and more effectively. Security Copilot is embedded in the Defender portal to enable security teams to efficiently summarize incidents, analyze scripts and codes, analyze files, summarize device information, use guided responses to resolve incidents, generate KQL queries, and create incident reports. Security Copilot helps you to:
- Reduce exposure and improve posture. Prevent breaches with insights to uncover critical exposure risk, and risk reduction recommendations.
- Prevent and disrupt threats. Identify and prioritize with incident summaries MITRE ATT&CK framework mapping, and automatic alert enrichment.
- Empower analysts:
- Accelerate incident resolution with guided responses, automated remediation, and summary report generation.
- Provide intelligent assistance with tailored prompts based on best practices that analyze malicious scripts and files, and suggest KQL queries.
The following image shows the integration of Microsoft Copilot in an incident page in the Defender portal.
For more information, see Microsoft Copilot in Microsoft Defender.