Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Zero Trust is a security model that assumes breach and verifies each request as though it originated from an uncontrolled network. Regardless of where the request came from or what resource it accessed, the Zero Trust model teaches us to "never trust, always verify."
As an IT architect or implementer, you can use the assessment and progress tracking resources in this article to get the following results:
- Assess your infrastructure's readiness for Zero Trust, including discovering which elements are already in place or can be easily strengthened or improved.
- Track the progress of the necessary Zero Trust security improvements in your environment for both business leaders and IT departments.
Progress tracking resources for the adoption framework business scenarios
The Zero Trust adoption framework documentation set helps security and technology teams collaborate with business leaders on Zero Trust by providing the following results:
- Recommended Zero Trust objectives for business leaders across organizations.
- A methodical and phased approach to implementing a Zero Trust architecture.
- A systematic way to track progress on objectives, scoped to business leaders.
- A systematic way to track progress on objectives and their tasks, scoped to IT leads and implementers.
- Curation of the most relevant resources for adoption of Zero Trust:
- PowerPoint slides that are ready to present to business leaders.
- Excel worksheets to assess your current status and to track progress.
- Technical implementation guidance and user infographics.
Adoption guidance for Zero Trust recommends building a Zero Trust strategy and architecture through the following business scenarios:
- Rapidly modernize your security posture
- Secure remote and hybrid work
- Identify and protect sensitive business data
- Prevent or reduce business damage from a breach
- Meet regulatory and compliance requirements
Each business scenario starts with building the business case, and then describes how to advance the required technical work through each lifecycle phase (Define strategy, Plan, Ready, Adopt, and Govern and manage).
For each business scenario, you can use the following progress tracking resources.
At-a-glance blueprint for Zero Trust
Adoption Scenario Plan Phase Grid
Easily understand the security enhancements for each business scenario and the level of effort for the stages and objectives of the Plan phase.
For business scenario project leads, business leaders, and other stakeholders.
Business leader tracker for Zero Trust
Zero Trust adoption tracker
Track your progress through the stages and objectives of the Plan phase.
For business scenario project leads, business leaders, and other stakeholders.
PowerPoint presentation download
Implementer tracker for Zero Trust
Business scenario objectives and tasks
Assign ownership and track your progress through the stages, objectives, and tasks of the Plan phase.
For business scenario project leads, IT leads, and IT implementers.
In-product dashboard for Zero Trust
Zero Trust initiative in the Microsoft Defender portal (might require sign-in with a user account that has Microsoft Defender portal privileges)
Also see Microsoft Security Exposure Management initiatives.
See current status, security metrics, and recommendations for the adoption framework business scenarios.
For business scenario project leads, IT leads, and IT implementers.
Assessment resources
To understand where your organization is on its Zero Trust journey, use these assessment resources.
Microsoft Zero Trust Security Posture Assessment
Evaluate your Zero Trust security posture and maturity level.
For IT department project leads and implementers.
Microsoft Zero Trust Security Posture Assessment
Zero Trust Assessment and strategy workshop
Evaluate your Zero Trust security posture and maturity level.
IT department project leads and implementers can use the Zero Trust Assessment strategy workshop downloadable Excel workbook at https://aka.ms/ztworkshop to track progress.
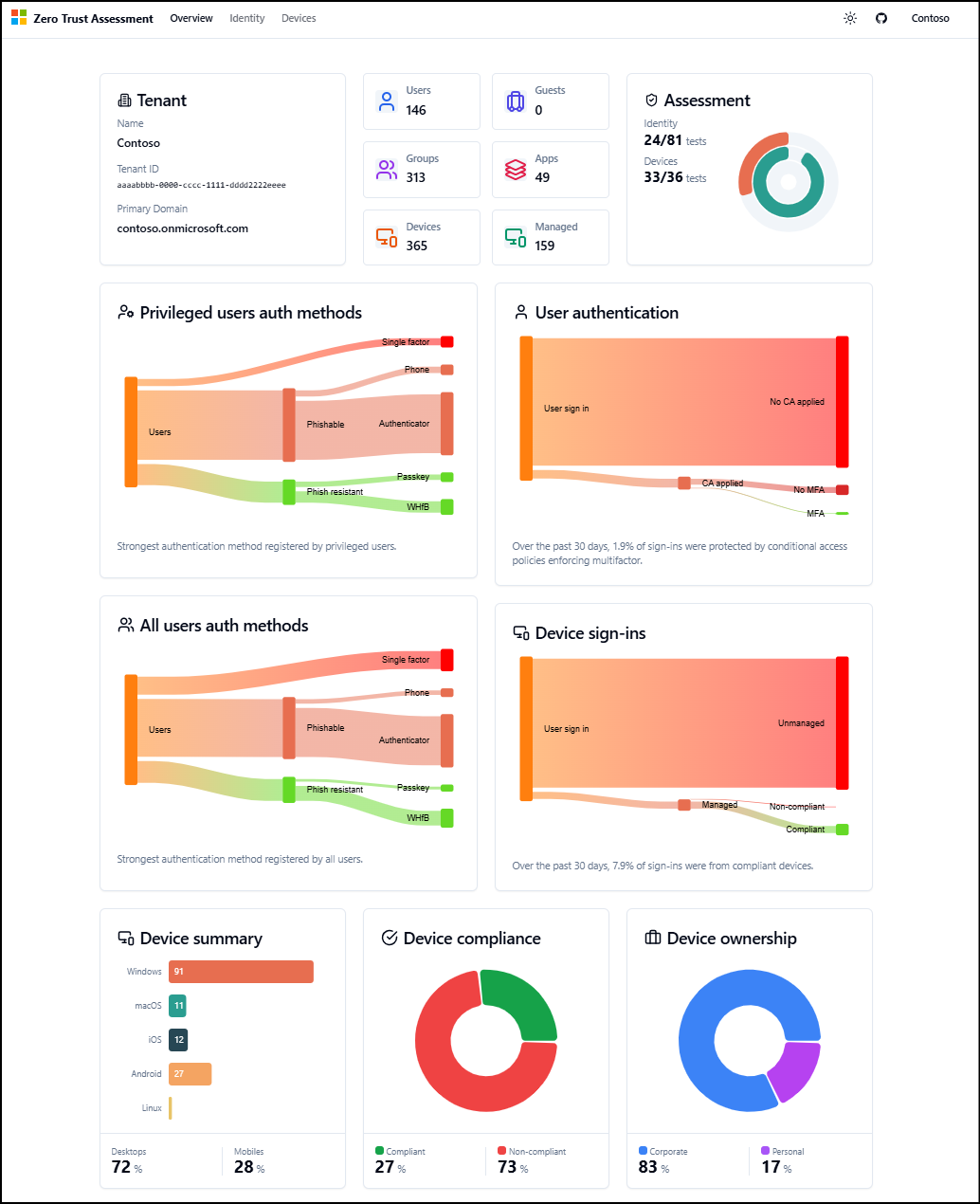
Learn how to automate the process of checking your tenant's configuration against Microsoft's best practices with the Zero Trust Assessment.
Recommended training
| Training | Introduction to Zero Trust |
|---|---|
| Use this module to understand the Zero Trust approach and how it strengthens the security infrastructure within your organization. |
| Training | Introduction to Zero Trust and best practice frameworks |
|---|---|
| Use this module to learn about best practices that cybersecurity architects use and some key best practice frameworks for Microsoft cybersecurity capabilities. You also learn about the concept of Zero Trust, and how to get started with Zero Trust in your organization. |
Other Zero Trust resources
Use other Zero Trust content based on a documentation set or the roles in your organization.
Documentation set
Follow this table for the best Zero Trust documentation set for your needs.
| Documentation set | Helps you... | Roles |
|---|---|---|
| Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. | Security architects, IT teams, and project managers |
| Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. | IT teams and security staff |
| Zero Trust for small businesses | Apply Zero Trust principles to small business customers. | Customers and partners working with Microsoft 365 for business |
| Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. | Security architects and IT implementers |
| Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance | Apply Zero Trust protections to your Microsoft 365 organization. | IT teams and security staff |
| Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. | IT teams and security staff |
| Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. | IT teams and security staff |
| Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. | Partner developers, IT teams, and security staff |
| Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. | Application developers |
Your role
Follow this table for the best documentation sets for your role in your organization.
| Role | Documentation set | Helps you... |
|---|---|---|
| Security architect IT project manager IT implementer |
Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. |
| Member of an IT or security team | Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. |
| Customer or partner for Microsoft 365 for business | Zero Trust for small businesses | Apply Zero Trust principles to small business customers. |
| Security architect IT implementer |
Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. |
| Member of an IT or security team for Microsoft 365 | Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance for Microsoft 365 | Apply Zero Trust protections to your Microsoft 365 organization. |
| Member of an IT or security team for Microsoft Copilots | Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. |
| Member of an IT or security team for Azure services | Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. |
| Partner developer or member of an IT or security team | Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. |
| Application developer | Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. |