Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Role mentioned: SOC TI analyst analyzing suspicious scripts
Scenario
During an incident, security analysts are typically tasked with investigating alerts and gathering pertinent information that's associated with the incident. They conduct root cause analyses and correlate information from a range of sources to determine the potential impact to the organization.
Depending on the scenario, analysts may need to analyze logs, examine malware, reverse engineer files or scripts, and investigate URLs that were observed.
An essential component of an investigation involves understanding what remediation steps to take and effectively conveying significant discoveries to keep stakeholders informed about the current state of the incident.
In this example, Security Copilot is used to perform a comprehensive incident investigation by gathering contextual information from alerts, analyzing a suspicious script, and generating an assessment accompanied by a set of remediation steps.
Steps
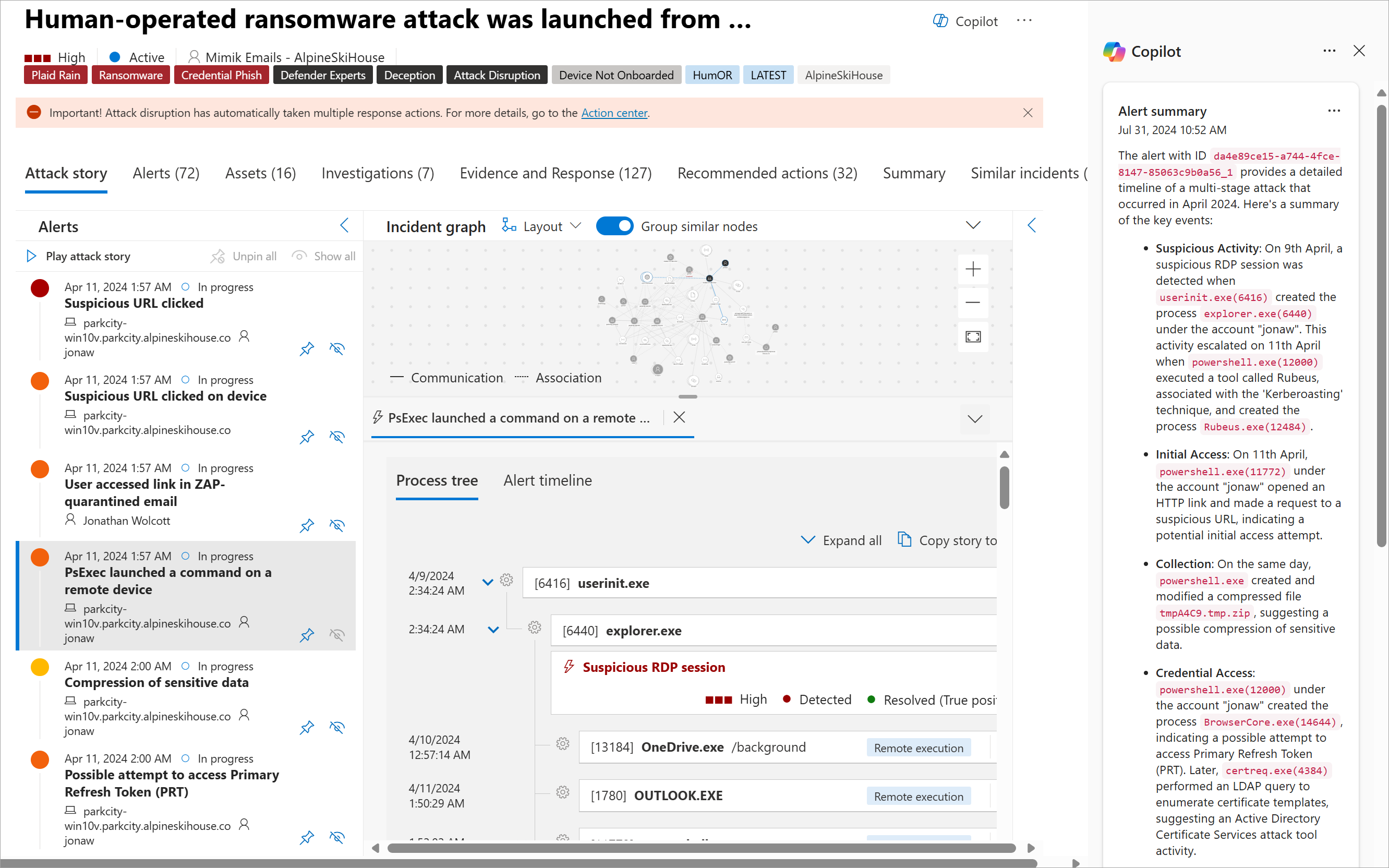
Start investigating in Microsoft Defender XDR.
Security Copilot is integrated in Microsoft Defender XDR. From an incident page, select the Copilot button to get a summary of an incident and get details such as the time and date of when an attack started, the entity or asset that started the attack, and assets involved in the attack.
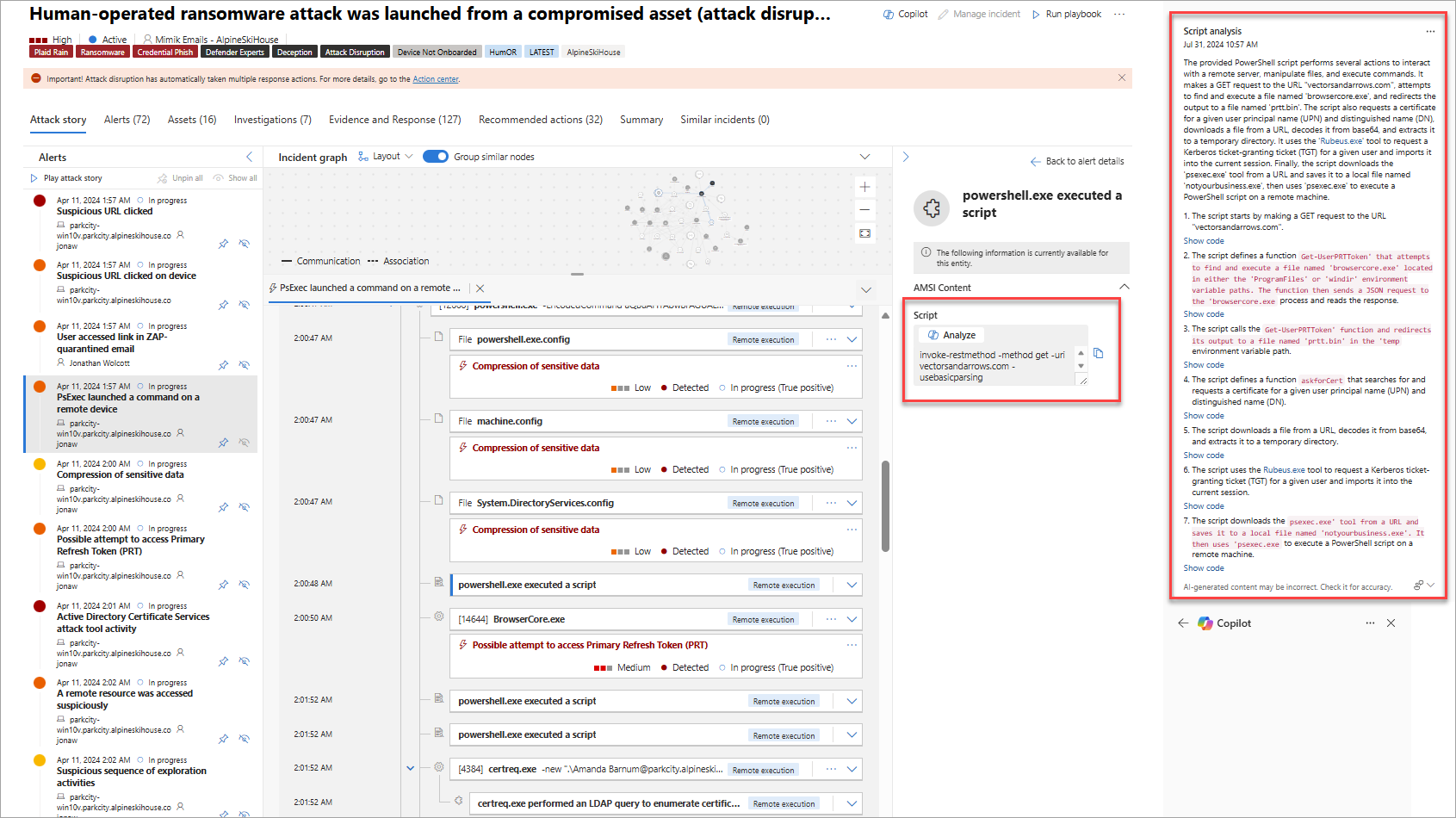
Analyze the suspicious script.
Microsoft Defender XDR flags when a suspicious script executes. Use Security Copilot to explain what the suspicious script is doing.
Note
Script analysis functions are continuously in development. Analysis of scripts in languages other than PowerShell, batch, and bash are being evaluated.
With a click of a button, a description is displayed along with an overall summary of the script.
Extend the investigation in Security Copilot using natural language prompts and more plugins.
Continue your investigation in the standalone experience of Security Copilot by selecting Open in Security Copilot.
The standalone experience allows you to extend the investigation by using natural language prompts.
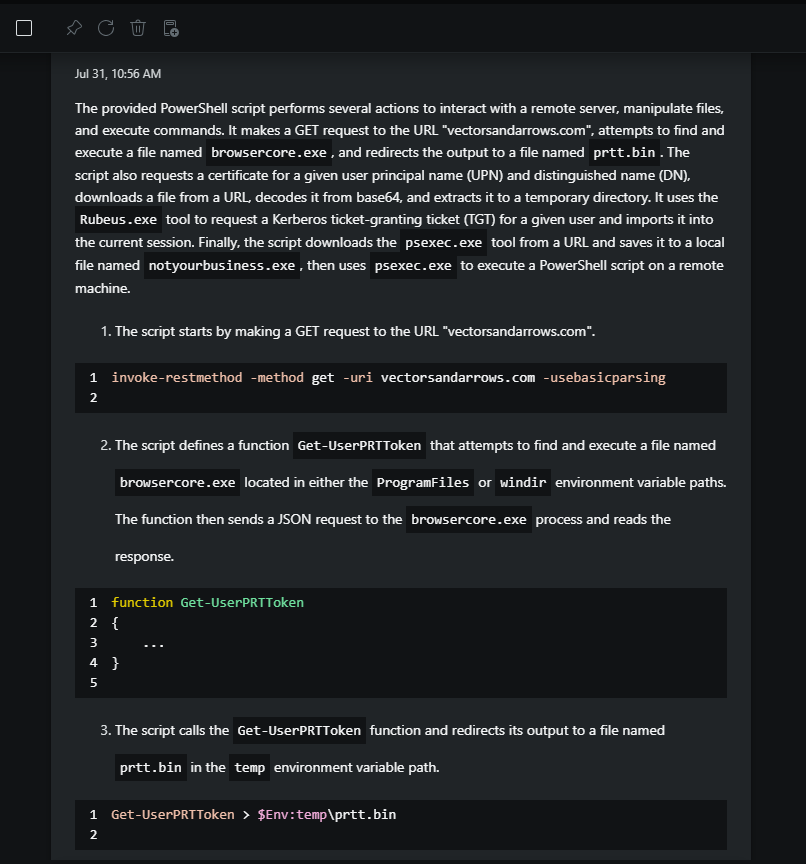
To gain a more comprehensive understanding of the incident, use Security Copilot to gather more information about the suspicious activity seen in the command line script.
Prompt used:
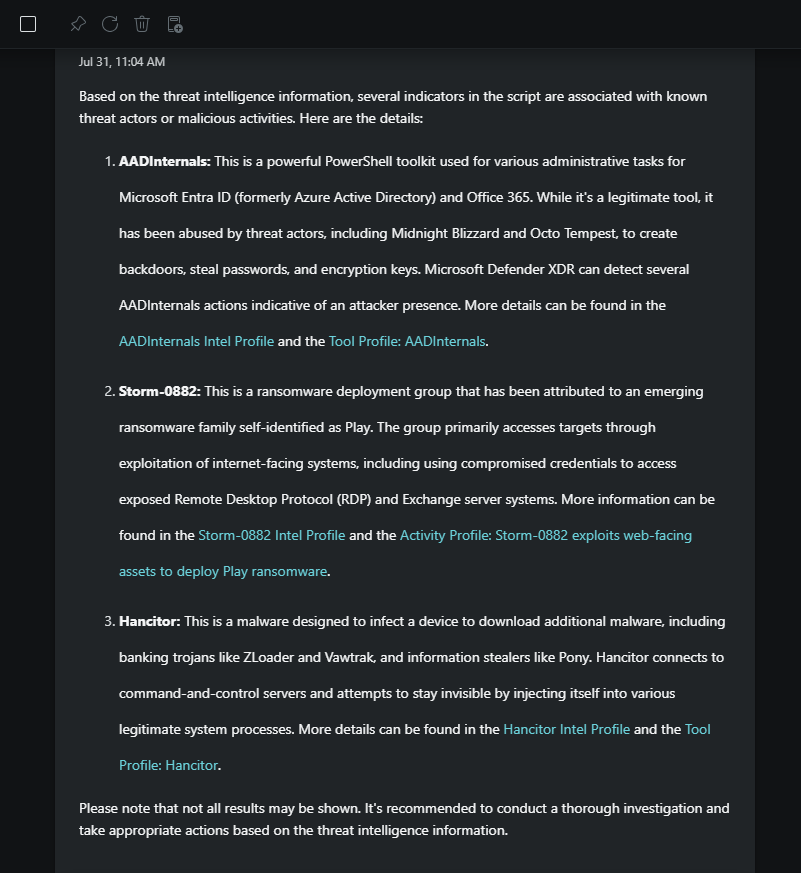
What can you tell me about the reputation of the indicators in the script? Are they malicious? If so, why?
Response:
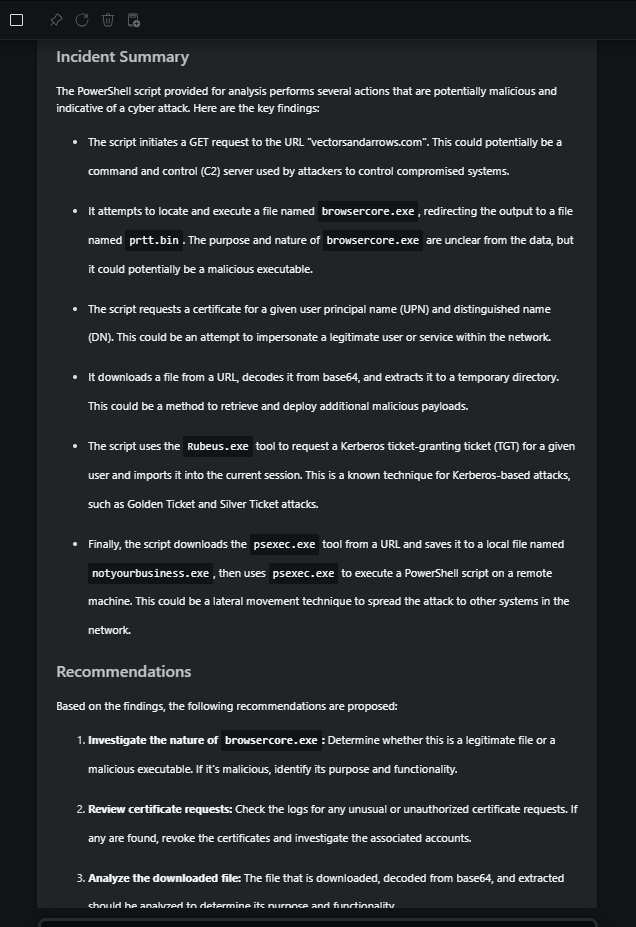
The response indicates that the several indicators in the script are associated with known threat actors. You can pin this response as a critical piece of information that can be used later.
Use Security Copilot to provide an assessment of the incident with supporting evidence and a set of recommendations.
Prompt used:
Summarize the findings from the investigation and conclude with a set of recommendations.
Response:
Tip
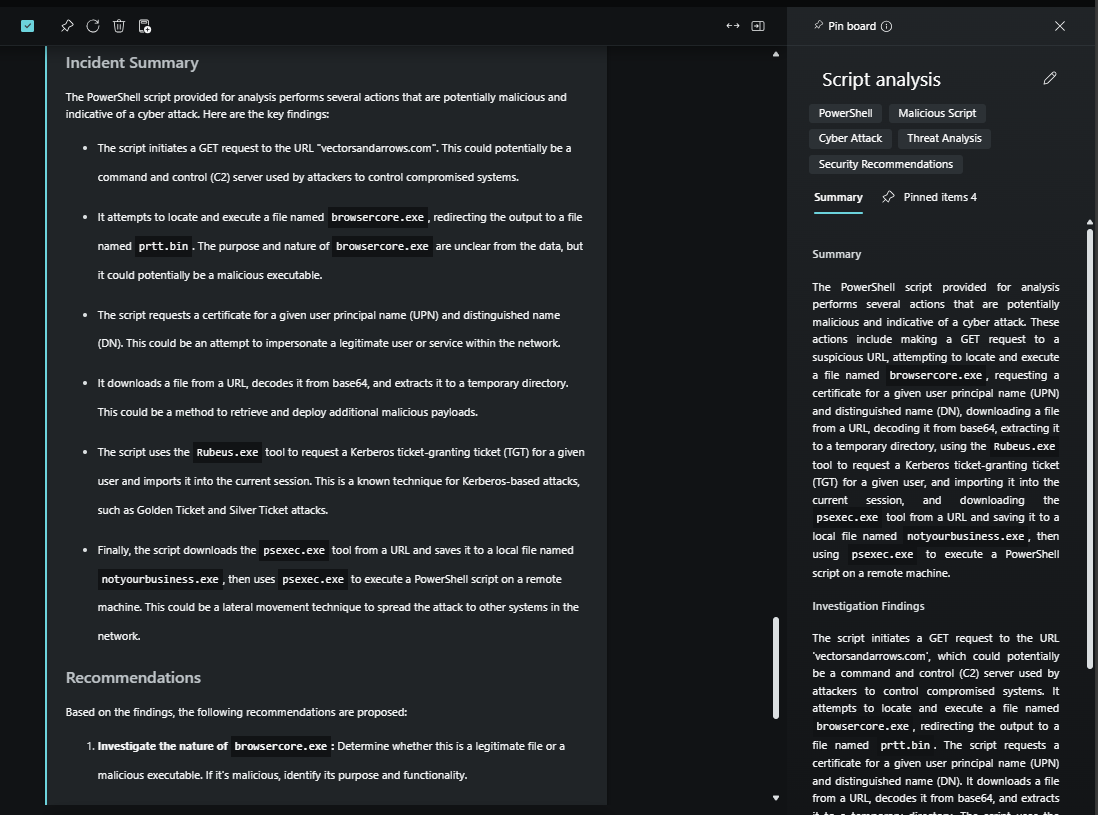
You can export the response for future reference. You also have the option of sharing the entire session with other analysts. Other team members who are reviewing the incident can leverage the pin board to get a complete summary of the investigation steps, which saves them valuable time.
Conclusion
In this use case, Security Copilot helped conduct a thorough investigation of an incident. Using natural language, analysts are able to get an explanation of what the suspicious script is doing and verify the indicators in the script are associated with known threat actors.
In addition, Security Copilot generated an assessment through a summary report and provided a set of recommendations to contain the incident, which can also be used to improve skills.