Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Use Privileged Identity Management (PIM) to manage, control, and monitor access within your Microsoft Entra organization. With PIM you can provide as-needed and just-in-time access to Azure resources, Microsoft Entra resources, and other Microsoft online services like Microsoft 365 or Microsoft Intune.
This article describes how to enable Privileged Identity Management (PIM) and get started using it.
Prerequisites
To use Privileged Identity Management, you must have a Microsoft Entra ID P2 or Microsoft Entra ID Governance license. For more information on licensing, see Microsoft Entra ID Governance licensing fundamentals.
Activation of role assignments
When a Microsoft Entra tenant has a Microsoft Entra ID P2 or Microsoft Entra ID Governance license, users with active role assignments can do the following:
- Open the Roles and administrators page in Microsoft Entra ID and select a role;
- Open the Privileged Identity Management page;
- Make calls to PIM using the Microsoft Entra roles API.
Microsoft Entra enables PIM for the tenant in the following ways:
- Starting immediately, you can create eligible or time-bound assignments for Microsoft Entra roles;
- Global Administrators or Privileged Role Administrators may start receiving other emails, such as the PIM weekly digest;
- The PIM service principal name (MS–PIM) may get mentioned in audit log events related to role assignment management.
These behaviors are expected and shouldn't affect your workflows.
Prepare PIM for Microsoft Entra roles
Here are the tasks we recommend for you to prepare Privileged Identity Management to manage Microsoft Entra roles:
- Configure Microsoft Entra role settings
- Give eligible assignments
- Allow eligible users to activate their Microsoft Entra role just-in-time
Prepare PIM for Azure roles
Here are the tasks we recommend for you to prepare Privileged Identity Management to manage Azure roles for a subscription:
- Discover Azure resources
- Configure Azure role settings
- Give eligible assignments
- Allow eligible users to activate their Azure roles just-in-time
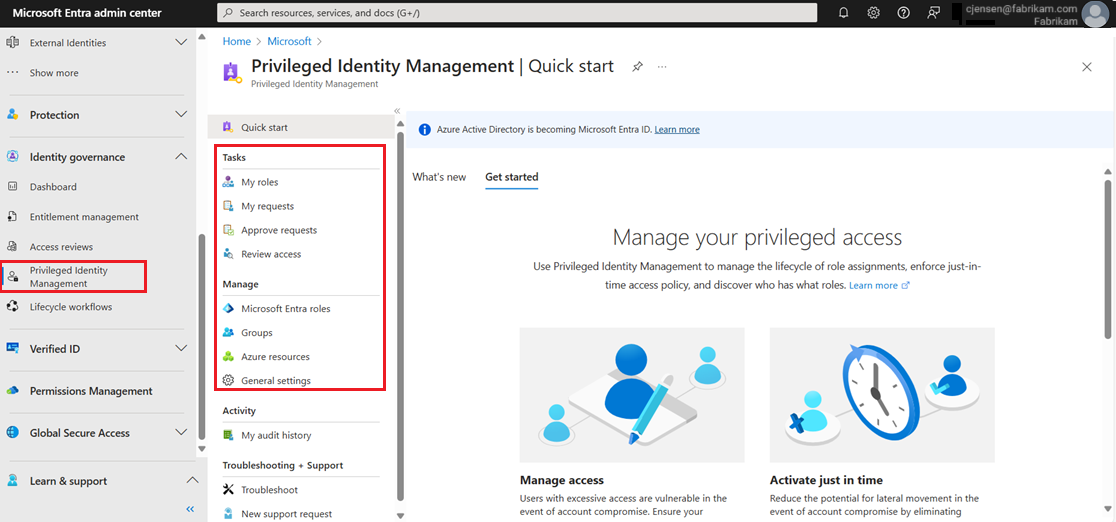
Navigate to your tasks
Once Privileged Identity Management is set up, you can learn your way around.
| Task + Manage | Description |
|---|---|
| My roles | Displays a list of eligible and active roles assigned to you. My roles is where you can activate any assigned eligible roles. |
| My requests | Displays your pending requests to activate eligible role assignments. |
| Approve requests | Displays a list of requests to activate eligible roles by users in your directory that you can approve. |
| Review access | Lists active access reviews you are assigned to complete, whether you're reviewing access for yourself or someone else. |
| Microsoft Entra roles | Displays a dashboard and settings for Privileged Role Administrators to manage Microsoft Entra role assignments. This dashboard is disabled for anyone who isn't a Privileged Role Administrator. These users have access to a special dashboard titled My view. The My view dashboard only displays information about the user accessing the dashboard, not the entire organization. |
| Groups | Manage just-in-time membership in the group or just-in-time ownership of the group. Groups can be used to provide access to Microsoft Entra roles, Azure roles, and various other scenarios. To manage a Microsoft Entra group in PIM, you must bring it under management in PIM. |
| Azure resources | Displays a dashboard and settings for Privileged Role Administrators to manage Azure resource role assignments. This dashboard is disabled for anyone who isn't a Privileged Role Administrator. These users have access to a special dashboard titled My view. The My view dashboard only displays information about the user accessing the dashboard, not the entire organization. |
| General settings | Select applications that are allowed to make app-only calls to Microsoft Graph API for PIM. |