Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
As organizations grow and their identity environments become more complex, it's important to control who has access to which resources. Microsoft Defender for Identity scoping lets you focus monitoring on specific Active Directory domains or organizational units. This helps improve efficiency by reducing noise from nonessential data and focusing on critical assets. You can also limit visibility to specific entities, so access matches each person's responsibilities. Scoped access is implemented by creating a custom role using Microsoft Defender XDR Unified RBAC. During the role configuration process, you define which users or Entra ID groups have access to specific Active Directory domains or Organizational units.
Prerequisites
Before you begin, make sure you meet the following requirements:
Check that Microsoft Defender for Identity sensor installed.
Confirm the Identity workload for URBAC is activated.
Ensure you have the Global Administrator or Security Administrator role in Microsoft Entra ID to create and manage custom roles.
Make sure Authorization permissions are configured through URBAC to manage roles without Global Administrator or Security Administrator privileges.
Configure scoping rules
To enable identity scoping, follow these steps:
Navigate to Permissions > Microsoft Defender XDR > Roles.
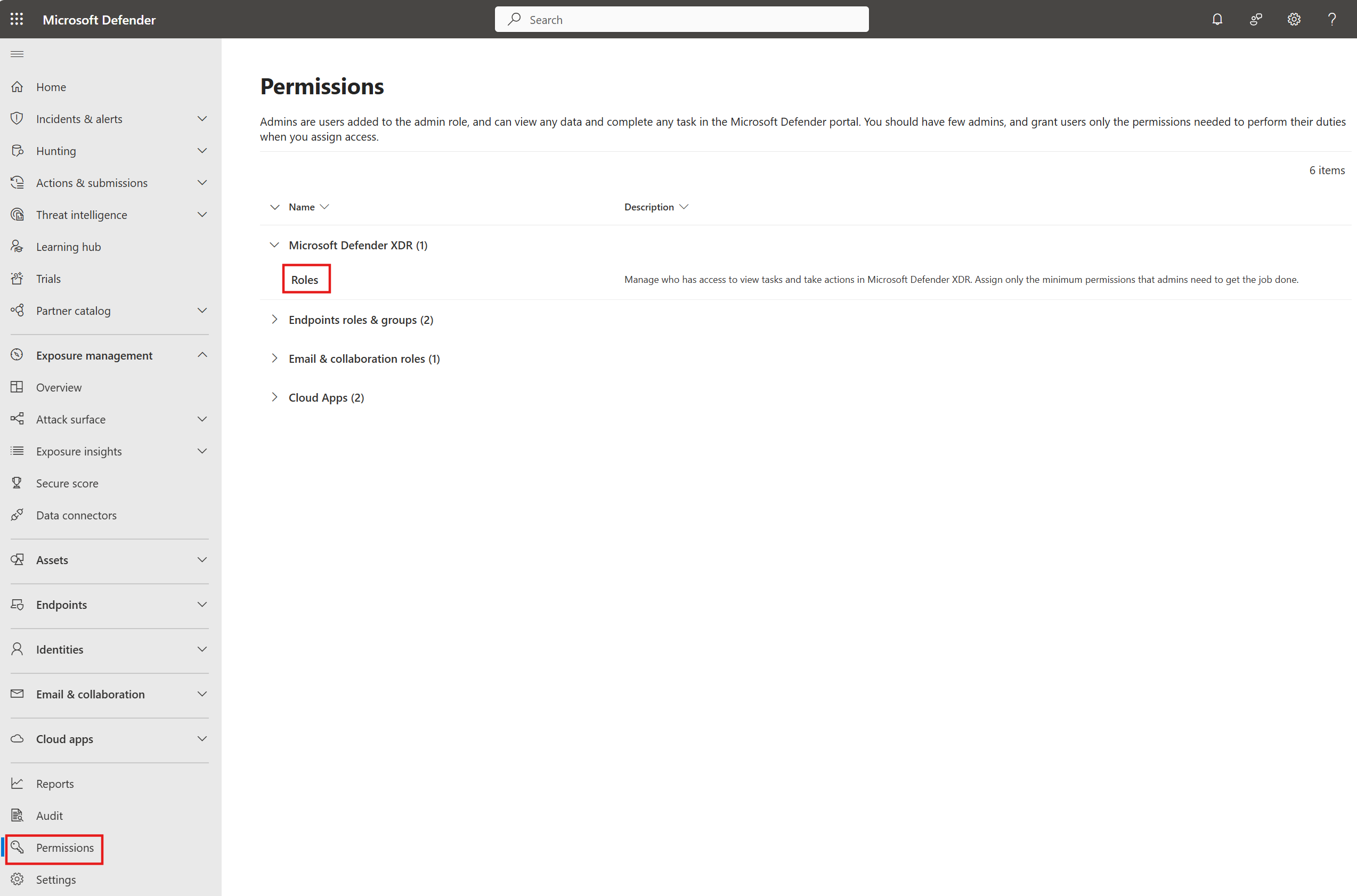
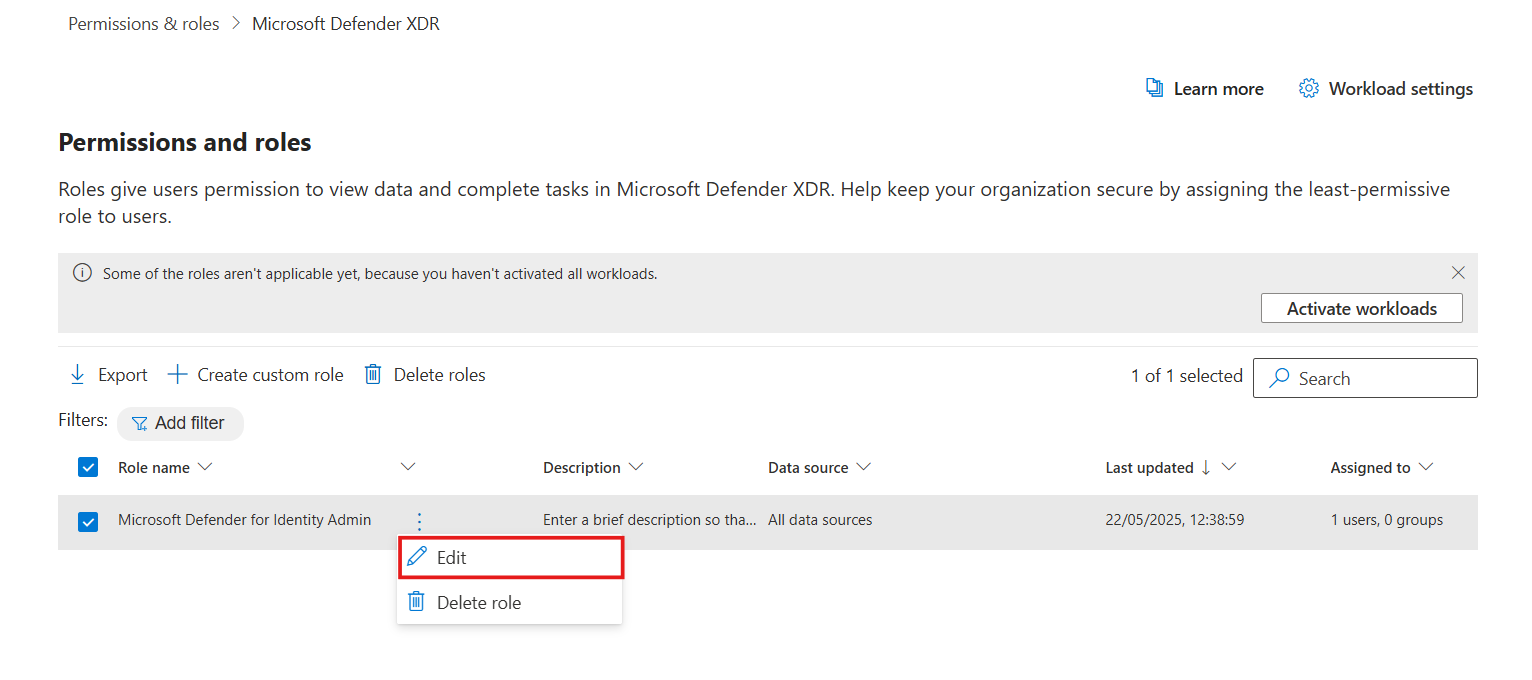
Select + Create custom role and follow the instructions in Create custom roles with Microsoft Defender XDR Unified RBAC.

You can edit the role at any time. Select the role from the list of custom roles and choose Edit.
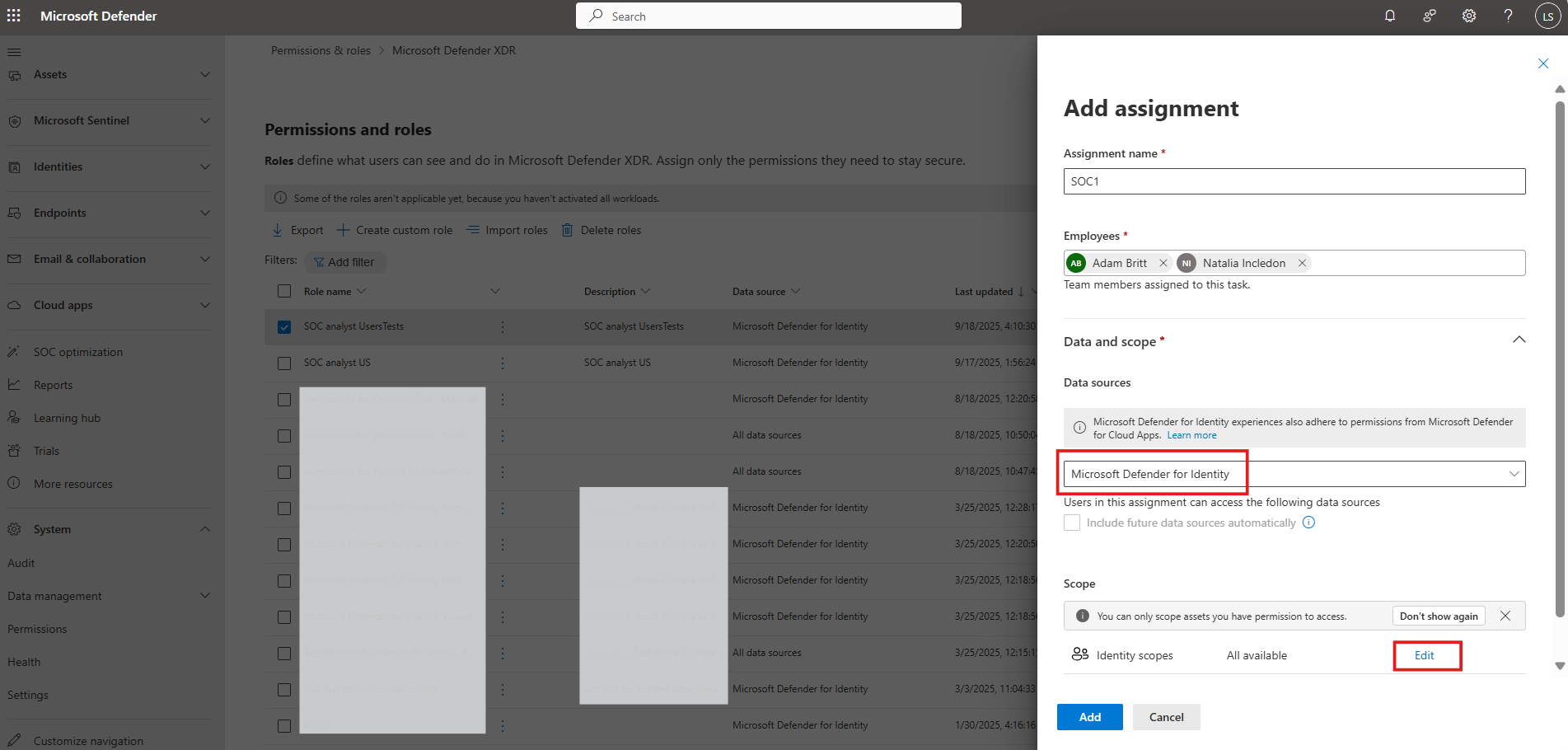
Select Add assignments and add the Assignment name.
- Under Assign users and groups, enter the usernames or Microsoft Entra ID groups you want to assign to the role.
- Select Microsoft Defender for Identity as the data source.
- Under Scope, select the user groups (AD domains or OU's) that will be scoped to the assignment. For an optimal experience, use the filter or search box.
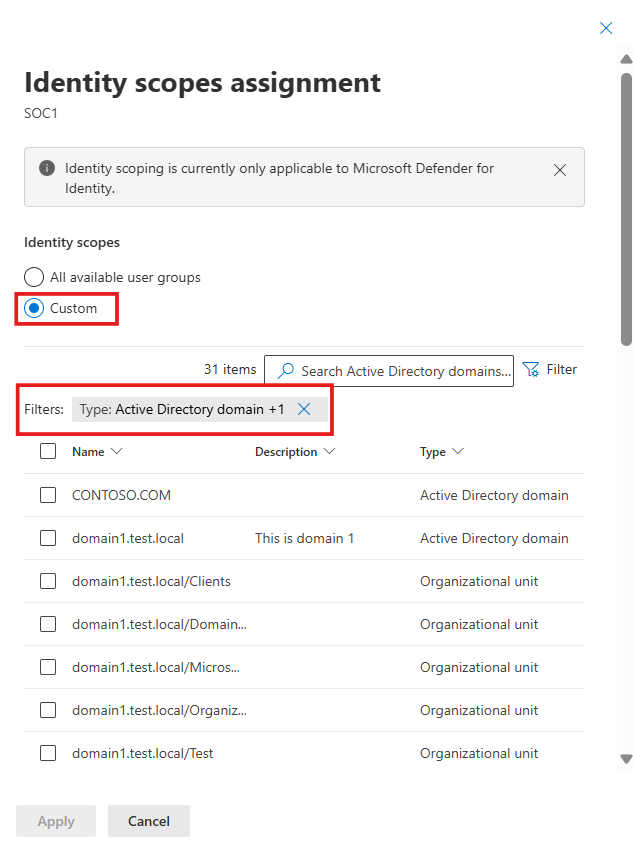
Select Apply and Add.
Known limitations
The following table lists the current limitations and supported scenarios for scoped access in Microsoft Defender for Identity.
Note
Custom roles apply only to new alerts and activities. Alerts and activities triggered before a custom role was created aren't retroactively tagged or filtered.
Microsoft Entra ID IP alerts aren't included within scoped MDI detections.
| Defender for Identity experience | Scoping by OU's | Scoping by AD domain |
|---|---|---|
| MDI alerts and incidents | Available | Available |
| Hunting tables: AlertEvidence+Info, IdentityInfo, IdentityDirectoryEvents, IdentityLogonEvents, IdentityQueryEvents | Available | Available |
| User page and user global search | Available | Available |
| MDI alerts based on XDR detection platform (detection source is XDR and service source is MDI) | Available | Available |
| Health issues | Unavailable | Available |
| Identities inventory and service accounts discovery page | Available | Available |
| Identities settings: manual tagging | Available | Available |
| Identities settings: sensors page, health issues notifications | Unavailable | Available |
| Defender XDR Incident email notifications | Available | Unavailable |
| ISPMs and exposure management | Unavailable | Unavailable |
| Download scheduled reports and Graph API | Unavailable | Unavailable |
| Device and group global search and entity page | Available | Available |
| Alert tuning and critical asset management | Unavailable | Unavailable |
Related articles
- Microsoft Defender for Identity role groups
- Microsoft Defender XDR Unified role-based access control (RBAC)
- Create custom roles with Microsoft Defender XDR Unified RBAC
- Import roles to Microsoft Defender XDR Unified role-based access control (RBAC)
- Activate Microsoft Defender XDR Unified role-based access control (RBAC)