Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
MITRE ATT&CK is a publicly accessible knowledge base of tactics and techniques that are commonly used by attackers, and is created and maintained by observing real-world observations. Many organizations use the MITRE ATT&CK knowledge base to develop specific threat models and methodologies that are used to verify security status in their environments.
Microsoft Sentinel analyzes ingested data, not only to detect threats and help you investigate, but also to visualize the nature and coverage of your organization's security status.
This article describes how to use the MITRE page in Microsoft Sentinel to view the analytics rules (detections) already active in your workspace, and the detections available for you to configure, to understand your organization's security coverage, based on the tactics and techniques from the MITRE ATT&CK® framework.
Important
The MITRE page in Microsoft Sentinel is currently in PREVIEW. The Azure Preview Supplemental Terms include legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Prerequisites
Before you can view the MITRE coverage for your organization in Microsoft Sentinel, ensure you have the following prerequisites:
- An active Microsoft Sentinel instance.
- Necessary permissions to view content in Microsoft Sentinel. For more information, see Roles and permissions in Microsoft Sentinel.
- Data connectors configured to ingest relevant security data into Microsoft Sentinel. For more information, see Microsoft Sentinel data connectors.
- Active scheduled query rules and near real-time (NRT) rules set up in Microsoft Sentinel. For more information, see Threat detection in Microsoft Sentinel.
- Familiarity with the MITRE ATT&CK framework and its tactics and techniques.
MITRE ATT&CK framework version
Microsoft Sentinel is currently aligned to The MITRE ATT&CK framework, version 16.
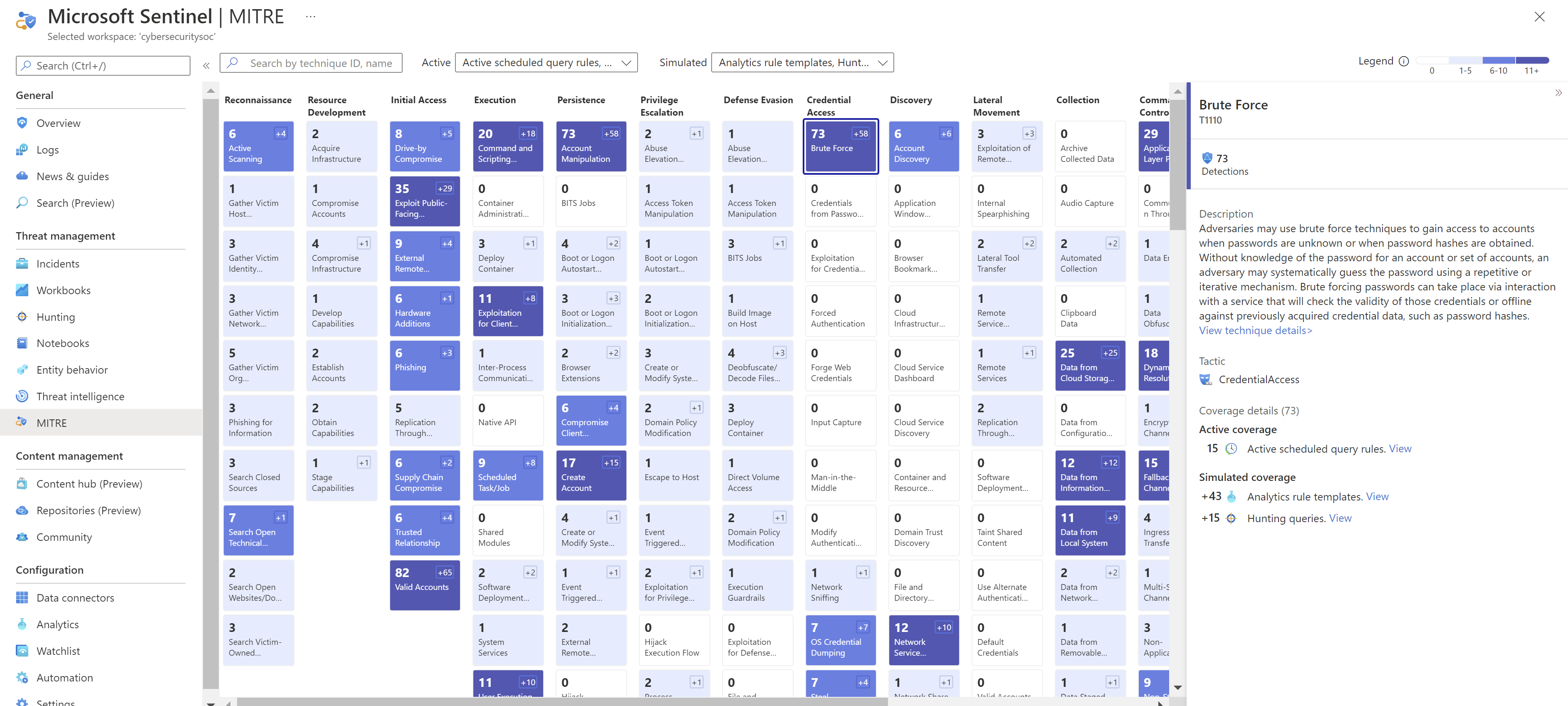
View current MITRE coverage
By default, both currently active scheduled query and near real-time (NRT) rules are indicated in the coverage matrix.
Do one of the following, depending on the portal you're using:
In the Defender portal, select Microsoft Sentinel > Threat management > MITRE ATT&CK.
To filter the page by a specific threat scenario, toggle the View MITRE by threat scenario option on, and then select a threat scenario from the drop-down menu. The page is updated accordingly. For example:

Use any of the following methods:
Use the legend to understand how many detections are currently active in your workspace for specific technique.
Use the search bar to search for a specific technique in the matrix, using the technique name or ID, to view your organization's security status for the selected technique.
Select a specific technique in the matrix to view more details in the details pane. There, use the links to jump to any of the following locations:
In the Description area, select View full technique details ... for more information about the selected technique in the MITRE ATT&CK framework knowledge base.
Scroll down in the pane and select links to any of the active items to jump to the relevant area in Microsoft Sentinel.
For example, select Hunting queries to jump to the Hunting page. There, you see a filtered list of the hunting queries that are associated with the selected technique, and available for you to configure in your workspace.
On the Defender portal, the details pane also shows recommended coverage details, including the ratio of active detections and security services (products) out of all recommended detections and services for the selected technique.
Simulate possible coverage with available detections
In the MITRE coverage matrix, simulated coverage refers to detections that are available, but not currently configured in your Microsoft Sentinel workspace. View your simulated coverage to understand your organization's possible security status, were you to configure all detections available to you.
In Microsoft Sentinel, under Threat management, select MITRE ATTA&CK (Preview), and then select items in the Simulated rules menu to simulate your organization's possible security status.
From there, use the page's elements as you would otherwise to view the simulated coverage for a specific technique.
Use the MITRE ATT&CK framework in analytics rules and incidents
Having a scheduled rule with MITRE techniques applied running regularly in your Microsoft Sentinel workspace enhances the security status shown for your organization in the MITRE coverage matrix.
Analytics rules:
- When configuring analytics rules, select specific MITRE techniques to apply to your rule.
- When searching for analytics rules, filter the rules displayed by technique to find your rules quicker.
For more information, see Detect threats out-of-the-box and Create custom analytics rules to detect threats.
Incidents:
When incidents are created for alerts that are surfaced by rules with MITRE techniques configured, the techniques are also added to the incidents.
For more information, see Investigate incidents with Microsoft Sentinel. If Microsoft Sentinel is onboarded to the Defender portal, then investigate incidents in the Microsoft Defender portal instead.
Threat hunting:
- When you're creating a new hunting query, select the specific tactics and techniques to apply to your query.
- When searching for active hunting queries, filter the queries displayed by tactics by selecting an item from the list above the grid. Select a query to see tactic and technique details in the details pane on the side
- When you're creating bookmarks, either use the technique mapping inherited from the hunting query, or create your own mapping.
For more information, see Hunt for threats with Microsoft Sentinel and Keep track of data during hunting with Microsoft Sentinel.
Related content
For more information, see: