Quickstart: Create an Azure DNS Private Resolver using Bicep
This quickstart describes how to use Bicep to create Azure DNS Private Resolver.
Bicep is a domain-specific language (DSL) that uses declarative syntax to deploy Azure resources. It provides concise syntax, reliable type safety, and support for code reuse. Bicep offers the best authoring experience for your infrastructure-as-code solutions in Azure.
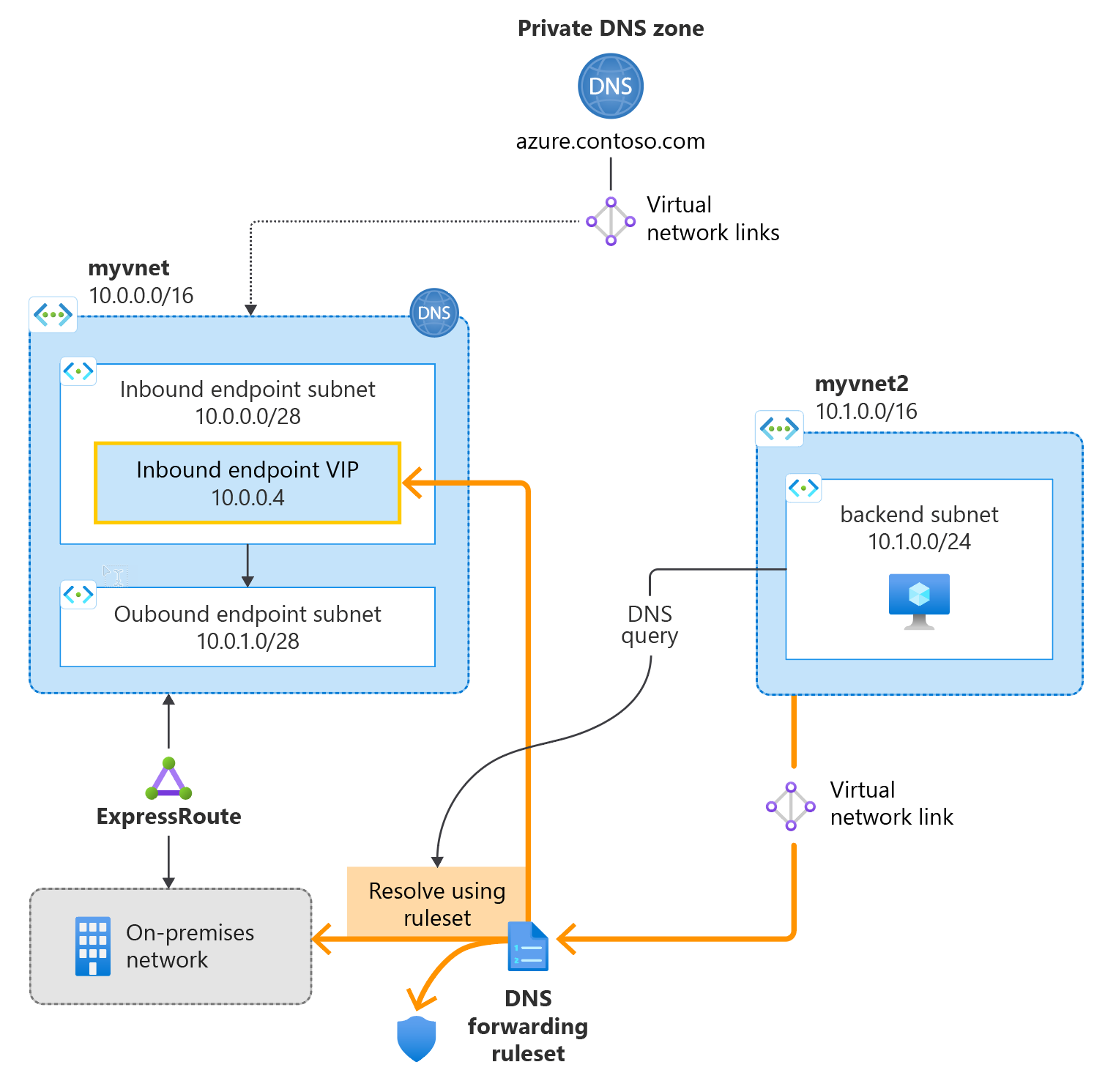
The following figure summarizes the general setup used. Subnet address ranges used in templates are slightly different than those shown in the figure.
Prerequisites
If you don't have an Azure subscription, create a free account before you begin.
Review the Bicep file
The Bicep file used in this quickstart is from Azure Quickstart Templates.
This Bicep file is configured to create a:
- Virtual network
- DNS resolver
- Inbound & outbound endpoints
- Forwarding Rules & rulesets.
@description('name of the new virtual network where DNS resolver will be created')
param resolverVNETName string = 'dnsresolverVNET'
@description('the IP address space for the resolver virtual network')
param resolverVNETAddressSpace string = '10.7.0.0/24'
@description('name of the dns private resolver')
param dnsResolverName string = 'dnsResolver'
@description('the location for resolver VNET and dns private resolver - Azure DNS Private Resolver available in specific region, refer the documenation to select the supported region for this deployment. For more information https://docs.microsoft.com/azure/dns/dns-private-resolver-overview#regional-availability')
@allowed([
'australiaeast'
'uksouth'
'northeurope'
'southcentralus'
'westus3'
'eastus'
'northcentralus'
'westcentralus'
'eastus2'
'westeurope'
'centralus'
'canadacentral'
'brazilsouth'
'francecentral'
'swedencentral'
'switzerlandnorth'
'eastasia'
'southeastasia'
'japaneast'
'koreacentral'
'southafricanorth'
'centralindia'
'westus'
'canadaeast'
'qatarcentral'
'uaenorth'
'australiasoutheast'
'polandcentral'
])
param location string
@description('name of the subnet that will be used for private resolver inbound endpoint')
param inboundSubnet string = 'snet-inbound'
@description('the inbound endpoint subnet address space')
param inboundAddressPrefix string = '10.7.0.0/28'
@description('name of the subnet that will be used for private resolver outbound endpoint')
param outboundSubnet string = 'snet-outbound'
@description('the outbound endpoint subnet address space')
param outboundAddressPrefix string = '10.7.0.16/28'
@description('name of the vnet link that links outbound endpoint with forwarding rule set')
param resolvervnetlink string = 'vnetlink'
@description('name of the forwarding ruleset')
param forwardingRulesetName string = 'forwardingRule'
@description('name of the forwarding rule name')
param forwardingRuleName string = 'contosocom'
@description('the target domain name for the forwarding ruleset')
param DomainName string = 'contoso.com.'
@description('the list of target DNS servers ip address and the port number for conditional forwarding')
param targetDNS array = [
{
ipaddress: '10.0.0.4'
port: 53
}
{
ipaddress: '10.0.0.5'
port: 53
}
]
resource resolver 'Microsoft.Network/dnsResolvers@2022-07-01' = {
name: dnsResolverName
location: location
properties: {
virtualNetwork: {
id: resolverVnet.id
}
}
}
resource inEndpoint 'Microsoft.Network/dnsResolvers/inboundEndpoints@2022-07-01' = {
parent: resolver
name: inboundSubnet
location: location
properties: {
ipConfigurations: [
{
privateIpAllocationMethod: 'Dynamic'
subnet: {
id: '${resolverVnet.id}/subnets/${inboundSubnet}'
}
}
]
}
}
resource outEndpoint 'Microsoft.Network/dnsResolvers/outboundEndpoints@2022-07-01' = {
parent: resolver
name: outboundSubnet
location: location
properties: {
subnet: {
id: '${resolverVnet.id}/subnets/${outboundSubnet}'
}
}
}
resource fwruleSet 'Microsoft.Network/dnsForwardingRulesets@2022-07-01' = {
name: forwardingRulesetName
location: location
properties: {
dnsResolverOutboundEndpoints: [
{
id: outEndpoint.id
}
]
}
}
resource resolverLink 'Microsoft.Network/dnsForwardingRulesets/virtualNetworkLinks@2022-07-01' = {
parent: fwruleSet
name: resolvervnetlink
properties: {
virtualNetwork: {
id: resolverVnet.id
}
}
}
resource fwRules 'Microsoft.Network/dnsForwardingRulesets/forwardingRules@2022-07-01' = {
parent: fwruleSet
name: forwardingRuleName
properties: {
domainName: DomainName
targetDnsServers: targetDNS
}
}
resource resolverVnet 'Microsoft.Network/virtualNetworks@2022-01-01' = {
name: resolverVNETName
location: location
properties: {
addressSpace: {
addressPrefixes: [
resolverVNETAddressSpace
]
}
enableDdosProtection: false
enableVmProtection: false
subnets: [
{
name: inboundSubnet
properties: {
addressPrefix: inboundAddressPrefix
delegations: [
{
name: 'Microsoft.Network.dnsResolvers'
properties: {
serviceName: 'Microsoft.Network/dnsResolvers'
}
}
]
}
}
{
name: outboundSubnet
properties: {
addressPrefix: outboundAddressPrefix
delegations: [
{
name: 'Microsoft.Network.dnsResolvers'
properties: {
serviceName: 'Microsoft.Network/dnsResolvers'
}
}
]
}
}
]
}
}
Seven resources are defined in this template:
- Microsoft.Network/virtualnetworks
- Microsoft.Network/dnsResolvers
- Microsoft.Network/dnsResolvers/inboundEndpoints
- Microsoft.Network/dnsResolvers/outboundEndpoints
- Microsoft.Network/dnsForwardingRulesets
- Microsoft.Network/dnsForwardingRulesets/forwardingRules
- Microsoft.Network/dnsForwardingRulesets/virtualNetworkLinks
Deploy the Bicep file
- Save the Bicep file as main.bicep to your local computer.
- Deploy the Bicep file using either Azure CLI or Azure PowerShell
az group create --name exampleRG --location eastus
az deployment group create --resource-group exampleRG --template-file main.bicep
When the deployment finishes, you should see a message indicating the deployment succeeded.
Validate the deployment
Use the Azure portal, Azure CLI, or Azure PowerShell to list the deployed resources in the resource group.
#Show the DNS resolver
az dns-resolver show --name "sampleDnsResolver" --resource-group "sampleResourceGroup"
#List the inbound endpoint
az dns-resolver inbound-endpoint list --dns-resolver-name "sampleDnsResolver" --resource-group "sampleResourceGroup"
#List the outbound endpoint
az dns-resolver outbound-endpoint list --dns-resolver-name "sampleDnsResolver" --resource-group "sampleResourceGroup"
Clean up resources
When no longer needed, use the Azure portal, Azure CLI, or Azure PowerShell to delete the resources in the following order.
Delete the DNS resolver
#Delete the inbound endpoint
az dns-resolver inbound-endpoint delete --dns-resolver-name "sampleDnsResolver" --name "sampleInboundEndpoint" --resource-group "exampleRG"
#Delete the virtual network link
az dns-resolver vnet-link delete --ruleset-name "sampleDnsForwardingRuleset" --resource- group "exampleRG" --name "sampleVirtualNetworkLink"
#Delete DNS forwarding ruleset
az dns-resolver forwarding-ruleset delete --name "samplednsForwardingRulesetName" --resource-group "exampleRG"
#Delete the outbound endpoint
az dns-resolver outbound-endpoint delete --dns-resolver-name "sampleDnsResolver" --name "sampleOutboundEndpoint" --resource-group "exampleRG"
#Delete the DNS resolver
az dns-resolver delete --name "sampleDnsResolver" --resource-group "exampleRG"
Next steps
In this quickstart, you created a virtual network and DNS private resolver. Now configure name resolution for Azure and on-premises domains.