Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
We’re expanding support in GitHub Advanced Security to include results with URI locations, providing broader coverage from container and dynamic scanning tools.
We’ve also improved how GitHub pull requests connect to Azure Boards work items, making it easier to keep work item states up to date when pull requests are merged.
Check out the release notes for details.
General
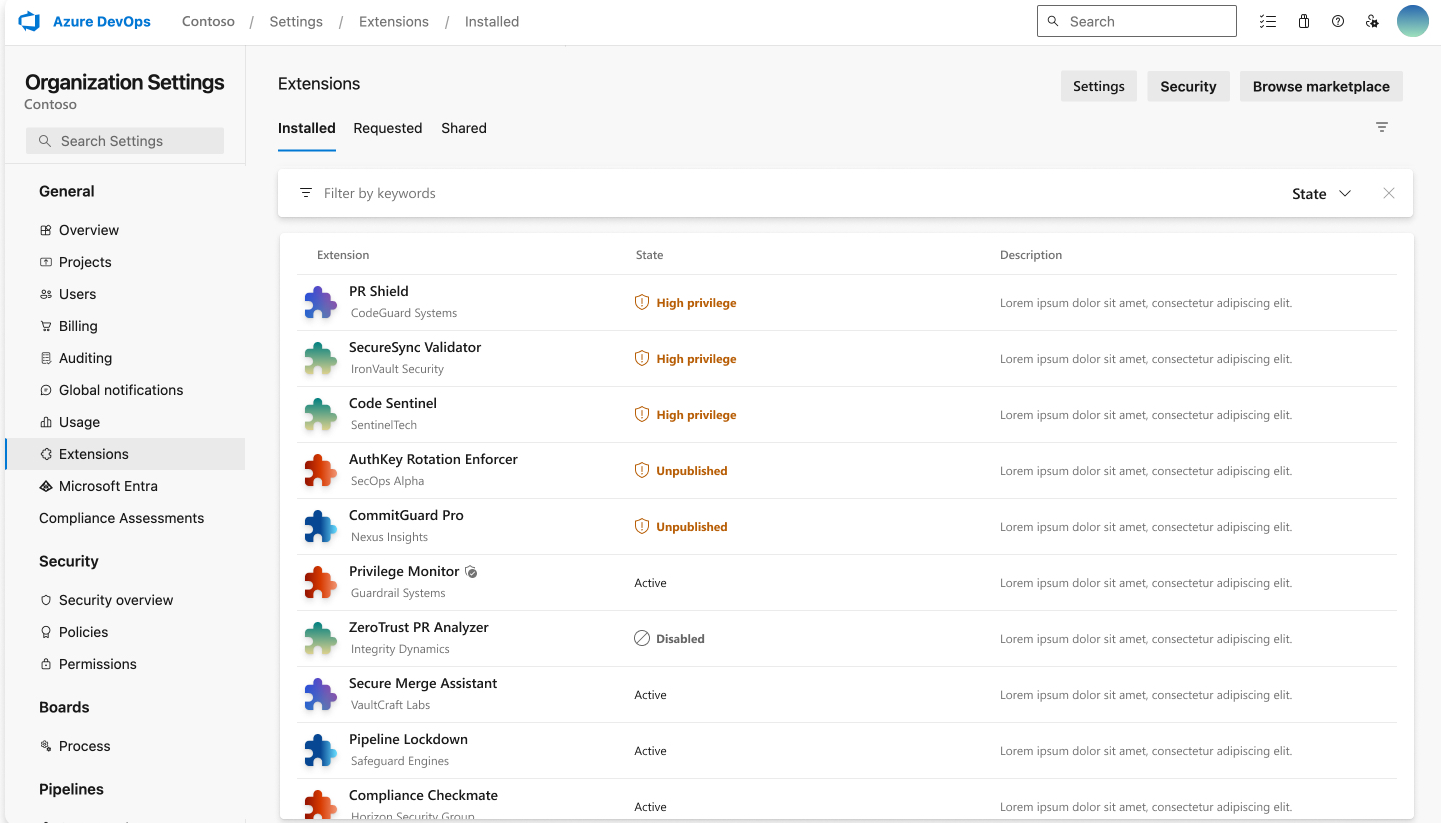
- Manage high privilege scopes, pipeline decorators, and unpublished extensions
- Overlapping Secrets for OAuth apps
GitHub Advanced Security for Azure DevOps
Azure Boards:
General
Manage high privilege scopes, pipeline decorators, and unpublished extensions
Azure DevOps extensions improve product functionality and workflows, but those with high privilege scopes may pose various risks.
We've added a new feature that flags these scopes on each organization's admin page and the Visual Studio Marketplace installation page, helping administrators make informed decisions. Unpublished extensions and pipeline decorators are also flagged for administrator awareness and appropriate actions.
For more information, visit documentation page.
Overlapping Secrets for OAuth apps
Azure DevOps has introduced Overlapping Secrets for OAuth apps—a new feature available on both UI and API designed to streamline secret rotation and reduce downtime.
With overlapping secrets, developers can generate a new secret while the old one remains valid, ensuring uninterrupted access during secret rotations. With this update, we also reduce the default secret validity period to 60 days. As Azure DevOps OAuth apps approach deprecation in 2026, this update provides a critical security improvement for teams still relying on them. Try it today to simplify your secret management and improve resilience. Learn more in our blog post.
GitHub Advanced Security for Azure DevOps
Advanced Security now accepts results with URI locations
Previously, Advanced Security rejected SARIF files that contained results with URIs listed as the alert location. This typically affected container scanning tools and dynamic application scanning tools. Advanced Security can now conditionally accept and display findings from these tools.
To enable this feature, set the pipeline variable advancedsecurity.publish.allowmissingpartialfingerprints.
trigger: none
variables:
advancedsecurity.publish.allowmissingpartialfingerprints: true
jobs:
- job: "AdvancedSecurityPublish"
displayName: "🛡 Publish ZAP SARIF"
steps:
- task: AdvancedSecurity-Publish@1
displayName: Publish to ZAP SARIF to Advanced Security
inputs:
SarifsInputDirectory: $(Build.SourcesDirectory)/sarifs/
Azure Boards
GitHub Integration: State Transition Support
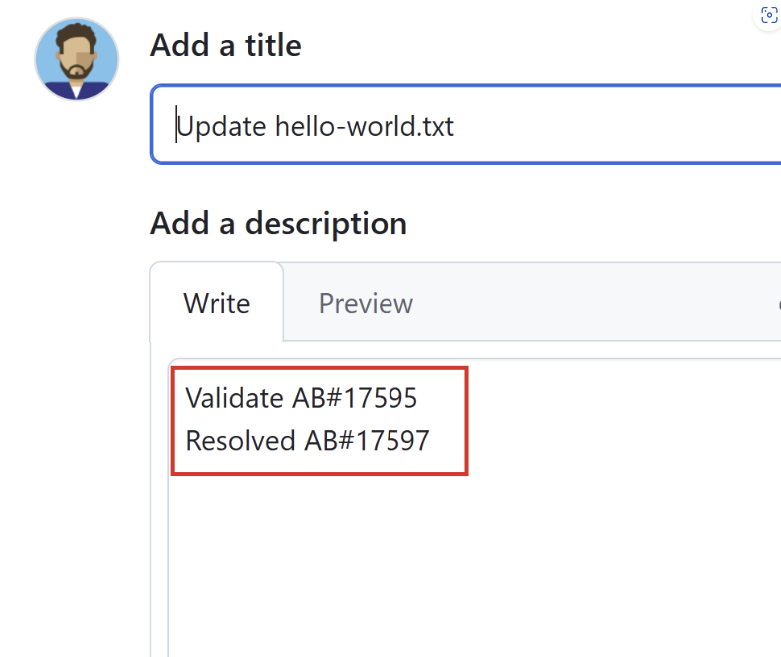
We’ve expanded our support for linking GitHub pull requests to Azure Boards work items! Previously, only the Fixes AB#{ID} keyword was supported. With this update, you can now use {State or Category} AB#{ID} to automatically transition work items to the desired state on merge.
If the GitHub pull request description includes a state name (e.g., Validate AB#1234), the linked work item's state will be updated as a result. If the state name isn’t recognized, we check if it matches a state category (like Resolved). If it does, the work item is transitioned to the first available state within that category.
If no matching state or category is found, the keyword is ignored and the state on the work item won't be updated.
Finally, the Fixes AB#{ID} keyword continues to work as expected, defaulting to the "Closed" state value.
Next steps
Note
These features will roll out over the next two to three weeks.
Head over to Azure DevOps and take a look.
How to provide feedback
We would love to hear what you think about these features. Use the help menu to report a problem or provide a suggestion.
You can also get advice and your questions answered by the community on Stack Overflow.
Thanks,
Dan Hellem