Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Monday, March 30, 2020 5:30 AM
Hello, This is my first time setting up a RADIUS server through Network Policy Server on server 2019 standard. I am trying to setup a radius server connected to a home router. I would like non-domain joined computers and phones to be able to connect to the radius server with a user credential from active directory. How can I achieve this? Microsoft says I need to install the certificate to the non-domain clients. If this is so, how come I can connect to my college enterprise wifi without having a certificate? Can this be achieved through Network Policy Server. If so, How can I Achieve this setup?
All replies (3)
Tuesday, March 31, 2020 8:03 AM
Hi ,
For non-domain joined computers, we need to manually import CA root certificate into "Trusted Root Certification Authorities".
You need to import the trusted root certificate in the clients and store it in the following location:
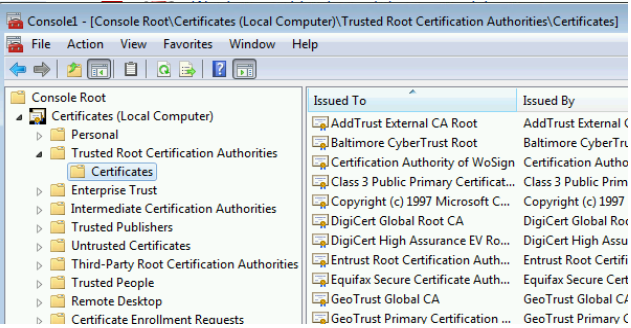
The trusted root certificate may help authenticate the server certificate.
You may find the trusted root certificate on NPS server's "Trusted Root certification Authorities" store or on the CA server.
For your reference:
Best Regards,
Candy
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Thursday, April 2, 2020 10:03 AM
Hi,
Just want to confirm the current situations.
Please feel free to let us know if you need further assistance.
Best Regards,
Candy
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Saturday, April 4, 2020 3:27 AM
I believe I am getting close. When I connect to the router it says, "Can't connect because the sign-in requirements for your device and the network aren't compatible". What did I do wrong? Here are pictures. Also the event log from the server.
Event Log:
Log Name: Security
Source: Microsoft-Windows-Security-Auditing
Date: 4/3/2020 5:40:26 PM
Event ID: 6273
Task Category: Network Policy Server
Level: Information
Keywords: Audit Failure
User: N/A
Computer: RADIUS-01
Description:
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID: RADIUS-01\TEST
Account Name: TEST
Account Domain: RADIUS-01
Fully Qualified Account Name: RADIUS-01\TEST
Client Machine:
Security ID: NULL SID
Account Name: -
Fully Qualified Account Name: -
Called Station Identifier: 20-0C-C8-3E-19-E2:ICECREAMMAN
Calling Station Identifier: 00-E0-2D-C3-05-22
NAS:
NAS IPv4 Address: 192.168.1.1
NAS IPv6 Address: -
NAS Identifier: -
NAS Port-Type: Wireless - IEEE 802.11
NAS Port: 0
RADIUS Client:
Client Friendly Name: WIFI
Client IP Address: 192.168.1.1
Authentication Details:
Connection Request Policy Name: Secure Wireless Connections
Network Policy Name: Secure Wireless Connections
Authentication Provider: Windows
Authentication Server: RADIUS-01
Authentication Type: EAP
EAP Type: -
Account Session Identifier: -
Logging Results: Accounting information was written to the local log file.
Reason Code: 22
Reason: The client could not be authenticated because the Extensible Authentication Protocol (EAP) Type cannot be processed by the server.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event%22%3E;
<System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-a5ba-3e3b0328c30d}" />
<EventID>6273</EventID>
<Version>2</Version>
<Level>0</Level>
<Task>12552</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2020-04-04T00:40:26.136684600Z" />
<EventRecordID>5528</EventRecordID>
<Correlation ActivityID="{a450f1c6-0a16-0002-14f2-50a4160ad601}" />
<Execution ProcessID="640" ThreadID="1168" />
<Channel>Security</Channel>
<Computer>RADIUS-01</Computer>
<Security />
</System>
<EventData>
<Data Name="SubjectUserSid">S-1-5-21-1028871360-930351885-1722487834-1001</Data>
<Data Name="SubjectUserName">TEST</Data>
<Data Name="SubjectDomainName">RADIUS-01</Data>
<Data Name="FullyQualifiedSubjectUserName">RADIUS-01\TEST</Data>
<Data Name="SubjectMachineSID">S-1-0-0</Data>
<Data Name="SubjectMachineName">-</Data>
<Data Name="FullyQualifiedSubjectMachineName">-</Data>
<Data Name="CalledStationID">20-0C-C8-3E-19-E2:ICECREAMMAN</Data>
<Data Name="CallingStationID">00-E0-2D-C3-05-22</Data>
<Data Name="NASIPv4Address">192.168.1.1</Data>
<Data Name="NASIPv6Address">-</Data>
<Data Name="NASIdentifier">-</Data>
<Data Name="NASPortType">Wireless - IEEE 802.11</Data>
<Data Name="NASPort">0</Data>
<Data Name="ClientName">WIFI</Data>
<Data Name="ClientIPAddress">192.168.1.1</Data>
<Data Name="ProxyPolicyName">Secure Wireless Connections</Data>
<Data Name="NetworkPolicyName">Secure Wireless Connections</Data>
<Data Name="AuthenticationProvider">Windows</Data>
<Data Name="AuthenticationServer">RADIUS-01</Data>
<Data Name="AuthenticationType">EAP</Data>
<Data Name="EAPType">-</Data>
<Data Name="AccountSessionIdentifier">-</Data>
<Data Name="ReasonCode">22</Data>
<Data Name="Reason">The client could not be authenticated because the Extensible Authentication Protocol (EAP) Type cannot be processed by the server.</Data>
<Data Name="LoggingResult">Accounting information was written to the local log file.</Data>
</EventData>
</Event>