Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Wednesday, May 27, 2020 3:51 PM
Hi All,
Been through weeks of setting up and re-setting up RRAS service, finally with help on another post got the service up and running on a guest VM. I am running Server 2019 and am splitting my services between multiple guest Hyper-V VMs to set up an instance of always on VPN. I've followed multiple different tutorials for this purpose that have me set up a CA, NPS, and an RRAS instance to authenticate a VPN connection using IKEv2 (not sure if I've got all of that worded correctly... I'm tryin' hard!) and they all create the same end result.
As of now, when I attempt to connect from a client machine to the VPN I get an error that starts out with "The network connection between your computer and the VPN server could not be established because the remote server is not responding...". This message continues to suggest there could be issues with a device between the internet and my RRAS server. I think, however, the problem is with the RRAS service itself. I've set this up according to templates (like the one provided) which I believe rely on IKEv2). I'm thinking based on what I've been reading that these services should listen on ports 500 and 4500. I've set up port forwarding in my router to this machine for those ports. I can confirm port forwarding works in general... I can forward port 53 to my machine running my DNS without issue. But, confirming the error message, ports 500 and 4500 remain "closed". The cause for "closed" status seems to be on the server itself. When I run netstat -a in an elevated command prompt, there are no services listed as listening on those ports... and RRAS is running and set up in the default configuration.
So any thoughts on why I'm not seeing services listening on the correct ports so I can get my VPN up and running? Appreciate any guidance. Thanks!
All replies (7)
Thursday, May 28, 2020 5:53 AM
Hi ,
Thanks for your posting here.
Could you please upload the result of netstat -a? Did you mean port 500 and 4500 is not in use?
If yes ,please check if “IKE and AuthIP IPsec Keying Modules” (short name: “IKEEXT”) service is running.


If not, could you please upload the screenshot? This can help me understand your situation better.
Best Regards,
Candy
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Thursday, May 28, 2020 6:14 PM
Hi Candy,
Thanks for the continued support. IKEEXT is running. I've attached the results of my netstat -a query. When I say nothing is listening, I mean there's no entry at all for anything running on ports 500 or 4500 and similarly, websites that check for open ports show "closed". Any ideas?
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:80 cbdc:0 LISTENING
TCP 0.0.0.0:88 cbdc:0 LISTENING
TCP 0.0.0.0:135 cbdc:0 LISTENING
TCP 0.0.0.0:389 cbdc:0 LISTENING
TCP 0.0.0.0:445 cbdc:0 LISTENING
TCP 0.0.0.0:464 cbdc:0 LISTENING
TCP 0.0.0.0:593 cbdc:0 LISTENING
TCP 0.0.0.0:636 cbdc:0 LISTENING
TCP 0.0.0.0:3268 cbdc:0 LISTENING
TCP 0.0.0.0:3269 cbdc:0 LISTENING
TCP 0.0.0.0:5985 cbdc:0 LISTENING
TCP 0.0.0.0:9389 cbdc:0 LISTENING
TCP 0.0.0.0:47001 cbdc:0 LISTENING
TCP 0.0.0.0:49664 cbdc:0 LISTENING
TCP 0.0.0.0:49665 cbdc:0 LISTENING
TCP 0.0.0.0:49666 cbdc:0 LISTENING
TCP 0.0.0.0:49667 cbdc:0 LISTENING
TCP 0.0.0.0:49669 cbdc:0 LISTENING
TCP 0.0.0.0:49673 cbdc:0 LISTENING
TCP 0.0.0.0:49679 cbdc:0 LISTENING
TCP 0.0.0.0:49680 cbdc:0 LISTENING
TCP 0.0.0.0:49682 cbdc:0 LISTENING
TCP 0.0.0.0:49689 cbdc:0 LISTENING
TCP 0.0.0.0:49695 cbdc:0 LISTENING
TCP 0.0.0.0:49714 cbdc:0 LISTENING
TCP 127.0.0.1:53 cbdc:0 LISTENING
TCP 192.168.1.210:53 cbdc:0 LISTENING
TCP 192.168.1.210:139 cbdc:0 LISTENING
TCP 192.168.1.210:60941 65.52.242.163:https ESTABLISHED
TCP 192.168.1.210:61201 192.168.1.12:8009 ESTABLISHED
TCP 192.168.1.210:61245 192.168.1.13:8009 ESTABLISHED
TCP 192.168.1.210:61370 192.168.1.14:8009 ESTABLISHED
TCP 192.168.1.210:61371 192.168.1.12:42836 ESTABLISHED
TCP 192.168.1.210:61899 192.168.1.11:8009 ESTABLISHED
TCP 192.168.1.210:63047 52.230.222.68:https ESTABLISHED
TCP 192.168.1.210:65149 13.65.40.138:https ESTABLISHED
TCP 192.168.1.210:65518 20.190.128.6:https TIME_WAIT
TCP 192.168.1.210:65526 20.190.128.4:https ESTABLISHED
TCP 192.168.1.215:53 cbdc:0 LISTENING
TCP 192.168.1.215:135 cbdc:65509 ESTABLISHED
TCP 192.168.1.215:139 cbdc:0 LISTENING
TCP 192.168.1.215:49667 cb-localserver:60588 ESTABLISHED
TCP 192.168.1.215:49667 cbdc:65510 ESTABLISHED
TCP 192.168.1.215:65509 cbdc:epmap ESTABLISHED
TCP 192.168.1.215:65510 cbdc:49667 ESTABLISHED
TCP [::]:80 cbdc:0 LISTENING
TCP [::]:88 cbdc:0 LISTENING
TCP [::]:135 cbdc:0 LISTENING
TCP [::]:389 cbdc:0 LISTENING
TCP [::]:445 cbdc:0 LISTENING
TCP [::]:464 cbdc:0 LISTENING
TCP [::]:593 cbdc:0 LISTENING
TCP [::]:636 cbdc:0 LISTENING
TCP [::]:3268 cbdc:0 LISTENING
TCP [::]:3269 cbdc:0 LISTENING
TCP [::]:5985 cbdc:0 LISTENING
TCP [::]:9389 cbdc:0 LISTENING
TCP [::]:47001 cbdc:0 LISTENING
TCP [::]:49664 cbdc:0 LISTENING
TCP [::]:49665 cbdc:0 LISTENING
TCP [::]:49666 cbdc:0 LISTENING
TCP [::]:49667 cbdc:0 LISTENING
TCP [::]:49669 cbdc:0 LISTENING
TCP [::]:49673 cbdc:0 LISTENING
TCP [::]:49679 cbdc:0 LISTENING
TCP [::]:49680 cbdc:0 LISTENING
TCP [::]:49682 cbdc:0 LISTENING
TCP [::]:49689 cbdc:0 LISTENING
TCP [::]:49695 cbdc:0 LISTENING
TCP [::]:49714 cbdc:0 LISTENING
TCP [::1]:53 cbdc:0 LISTENING
TCP [::1]:389 cbdc:49683 ESTABLISHED
TCP [::1]:389 cbdc:49684 ESTABLISHED
TCP [::1]:389 cbdc:62738 ESTABLISHED
TCP [::1]:49683 cbdc:ldap ESTABLISHED
TCP [::1]:49684 cbdc:ldap ESTABLISHED
TCP [::1]:62738 cbdc:ldap ESTABLISHED
TCP [fe80::e4:94f6:d4b8:aa7a%18]:53 cbdc:0 LISTENING
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:53 cbdc:0 LISTENING
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:389 cbdc:62730 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:389 cbdc:62733 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:389 cbdc:62737 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:49667 cbdc:49692 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:49667 cbdc:49718 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:49667 cbdc:52043 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:49692 cbdc:49667 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:49718 cbdc:49667 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:52043 cbdc:49667 ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:62730 cbdc:ldap ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:62733 cbdc:ldap ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:62737 cbdc:ldap ESTABLISHED
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:65514 cbdc:epmap TIME_WAIT
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:65515 cbdc:49667 TIME_WAIT
TCP [fe80::b1f7:2d7f:d1ba:6e1f%5]:65528 cbdc:epmap TIME_WAIT
UDP 0.0.0.0:123 *:*
UDP 0.0.0.0:389 *:*
UDP 0.0.0.0:500 *:*
UDP 0.0.0.0:4500 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5353 *:*
UDP 0.0.0.0:5355 *:*
UDP 0.0.0.0:51085 *:*
UDP 0.0.0.0:51086 *:*
UDP 0.0.0.0:51087 *:*
UDP 0.0.0.0:51088 *:*
UDP 0.0.0.0:51089 *:*
UDP 0.0.0.0:51090 *:*
UDP 0.0.0.0:51091 *:*
UDP 0.0.0.0:51092 *:*
UDP 0.0.0.0:51093 *:*
UDP 0.0.0.0:51094 *:*
UDP 0.0.0.0:51095 *:*
UDP 0.0.0.0:51096 *:*
UDP 0.0.0.0:51097 *:*
UDP 0.0.0.0:51098 *:*
UDP 0.0.0.0:51099 *:*
UDP 0.0.0.0:51100 *:*
UDP 0.0.0.0:51101 *:*
UDP 0.0.0.0:51102 *:*
UDP 0.0.0.0:51103 *:*
UDP 0.0.0.0:51104 *:*
UDP 0.0.0.0:51105 *:*
UDP 0.0.0.0:51106 *:*
UDP 0.0.0.0:51107 *:*
UDP 0.0.0.0:51108 *:*
UDP 0.0.0.0:51109 *:*
UDP 0.0.0.0:51110 *:*
UDP 0.0.0.0:51111 *:*
UDP 0.0.0.0:51112 *:*
UDP 0.0.0.0:51113 *:*
UDP 0.0.0.0:51114 *:*
UDP 0.0.0.0:51115 *:*
UDP 0.0.0.0:51116 *:*
UDP 0.0.0.0:51117 *:*
UDP 0.0.0.0:51118 *:*
There's a ton of other text like this (IPv6?) but I'm over the character limit if I paste it in.
Thanks!
Friday, May 29, 2020 3:05 AM
Hi ,
Please run the following cmd:
netstat -an | find "500"
I did not find something wrong with your ports 500 and 4500.
You could see the testing result in my lab, my IKEv2 connection is fine.

Have you import CA certificate to Trusted Root Certification Authority on client? Then, in your client machine hosts file ,add entry for VPN server (name must be equal to one specified in SSL certificate)
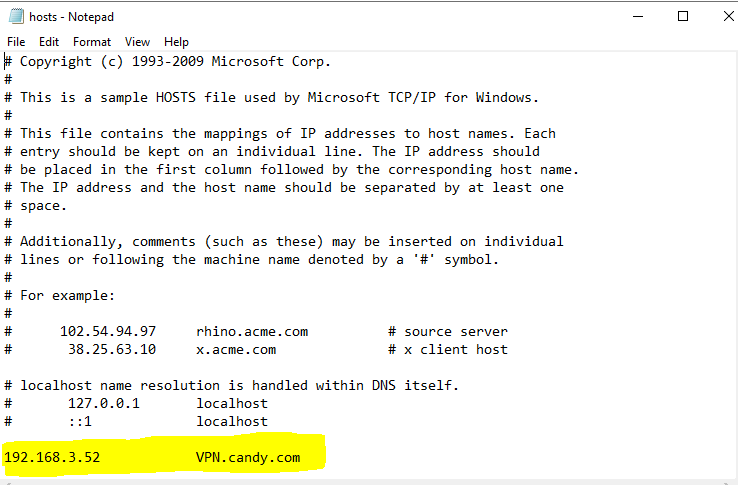
Then in VPN connection, type VPN server name.

For your reference:
Deploying VPN Server on Windows Server 2016
Please Note: Since the web site is not hosted by Microsoft, the link may change without notice. Microsoft does not guarantee the accuracy of this information.
If possible, would you please post the result of running ipconfig/all at the command prompt on the VPN server and VPN client to let us know the machine’s configuration?
Note: since this is a public forum, everyone could view your information, please remove private information that might leak your privacy.
In addition, in order to narrow down the issue, please turn off firewall on both VPN server and VPN client and then check if it works fine.
Best Regards,
Candy
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Monday, June 1, 2020 1:46 AM
Hi ,
Just want to confirm the current situations.
Please feel free to let us know if you need further assistance.
Best Regards,
Candy
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Monday, June 1, 2020 9:59 PM
Hi Candy,
I think the main problem is something to do with the ports not being opened? If I connect to my VPN from within the network (ie. I'm on the corporate network with my server), I can sign into the VPN just fine. When I jump outside the corporate network (say tethered to my mobile phone or on a nearby guest network), the connection stops working and I get the error that says "a network communication between your computer and the VPN server could not be established"
I have port forwarding configured on my router to send traffic coming in to :500 and :4500 to my local IP address with RRAS running. If I go to a site like canyouseeme it gives an error saying it cannot "see" my service. If I add a rule in the same way to port forward DNS requests (port 53) and then go to one of these sites, I get a success message that the port can be seen. The difference, on my netstat output for these two ports is that 500/4500 are showing as 0.0.0.0:500 or 0.0.0.0:4500 whereas 53 will show on the correct local address (eg. 192.168.1.10:53).
So the service doesn't appear to be listening correctly to allow the connection. I have disabled all firewalls and tried this and have tried opening the specific ports in the firewall and checked again with the firewall on and off and still no success. Am I missing something? Thanks for your help!
Tuesday, June 2, 2020 9:38 PM
Hey,
Can you post a screenshot of your RRAS Console > Ports?
Kind Regards
Tuesday, June 9, 2020 5:14 AM
This turned out to be something weird. It seems to actually be an issue with the public network I was using. If I try to connect to the vpn from another home network, it works fine. Apparently, there's an issue with xfinity hotspots and this IKEv2 vpn connection.
Not sure how to fix that, I'll try suggestions if it's worthwhile to find a solution for others on the forum, but otherwise, I've identified the problem and my fix is just to avoid those hotspots.
Thanks for your help!