Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Sunday, March 19, 2017 6:35 PM
Windows 10 boots and opens several port, such as:
**49410, 49411, 49673, 49674, 49676, 49677, 49678, 49679, 49680, 49684, 49686, 49687, 49688, 49689 **
These connections are being started by svchost. Most of the foreign hosts look to be innocent enough such as Microsoft, Norton (my antivirus), Akamai, and my ISP provider's email server but others seem to be hosting servers which makes me think they may not be legitimate. Moreover, I don't know why these connections are being used. I know Microsoft needs connections for Cortana and frequently checks licensing but I'd like to know if I am giving away the whole farm by allowing these connections. To date, I use the netstat -ano to determine the task ID associated with these ports and then look at task manager (I start this first and pause updates so it retains the tasks at bootup). I'm not as clear about finding the configuration files for svchost files but I can see what is running under each in task manager. I am also curious about the network setup since upgrading to the 1607 anniversary update. I click start --> settings --> network & internet --> view your network properties. I see Microsoft Wi-Fi Virtual Adapter, Wi-Fi (my real hardware adapter), isatap.telus adapter (no idea), local area connection 6 (teredo tunneling pseudo interface) (again no idea), local area connection 3 (Microsoft Wi-Fi Direct Virtual Adapter #2) (again, no idea).
The tunneling interfaces would be encrypted, correct? So has Microsoft done this to ensure confidentiality of information being transferred to them? Why do they need so many connections? What purpose are these connections?
signed Curious
All replies (5)
Monday, March 20, 2017 8:05 AM ✅Answered
Hi,
Some drivers explanation here:
**Microsoft Teredo Tunneling Adapter:**Teredo tunneling is a transition technology that gives full IPv6 connectivity for IPv6-capable hosts which are on the IPv4 Internet but which have no direct native connection to an IPv6 network. At the moment most home systems connected to the internet do not have native IPv6 connectivity and as more websites move to the new system teredo tunneling needs to be used so our IPv4 sytsems can have access and process IPv6 address data.
Microsoft Wi-Fi Direct Virtual Adapter: Virtual WiFi is a technology that virtualizes your network adapter much in the same way VMWare virtualizes your entire operating system. Once virtualized, you can basically convert one physical wireless adapter into two virtual ones. This allows you to then connect one virtual network adapter to your regular wireless network and use the other virtual adapter to connect to another network such as an ad-hoc network or to create a WiFi hotspot and allow other to connect to your Windows 7 machine wireless like they would connect to a normal wireless access point.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Monday, March 20, 2017 9:04 PM ✅Answered
You may find TCPView helpful. It will list the process (that may help) for the connections and can also right click the connections and Whois lists the domain details (also resolves addresses by default so they can be seen).
Tuesday, March 21, 2017 7:12 AM ✅Answered
Hi,
These ports you mentioned are for system process or services:
You can google to see the detailed information about what these process or services do.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Monday, March 20, 2017 7:46 AM
Hi,
As we know, The Well Known port range is from 0 – 1023, Registered ports run from 1024 – 49151, and the Dynamic ports run from 49152 – 65535. The ports you mentioned could be Dynamic ports.
Can you see in details that which service or detailed process use the ports you mentioned?
Please run command as below:
tasklist /svc
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Monday, March 20, 2017 7:06 PM
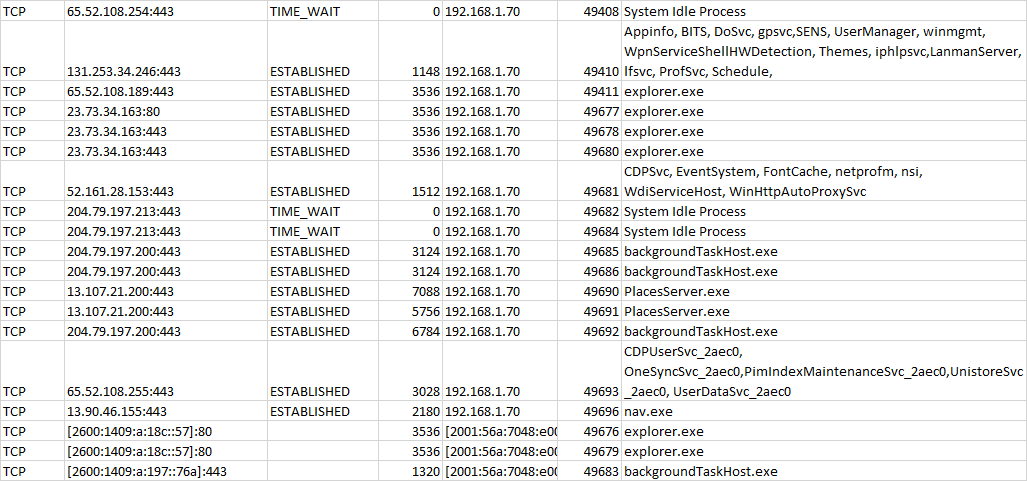
Ok here are details of what I see for connections right after a bootup, followed by the tasklist.
here is my netstat -ano for established connections
TCP 192.168.1.70:49408 65.52.108.254:443 TIME_WAIT 0
TCP 192.168.1.70:49410 131.253.34.246:443 ESTABLISHED 1148
TCP 192.168.1.70:49411 65.52.108.189:443 ESTABLISHED 3536
TCP 192.168.1.70:49677 23.73.34.163:80 ESTABLISHED 3536
TCP 192.168.1.70:49678 23.73.34.163:443 ESTABLISHED 3536
TCP 192.168.1.70:49680 23.73.34.163:443 ESTABLISHED 3536
TCP 192.168.1.70:49681 52.161.28.153:443 ESTABLISHED 1512
TCP 192.168.1.70:49682 204.79.197.213:443 TIME_WAIT 0
TCP 192.168.1.70:49684 204.79.197.213:443 TIME_WAIT 0
TCP 192.168.1.70:49685 204.79.197.200:443 ESTABLISHED 3124
TCP 192.168.1.70:49686 204.79.197.200:443 ESTABLISHED 3124
TCP 192.168.1.70:49690 13.107.21.200:443 ESTABLISHED 7088
TCP 192.168.1.70:49691 13.107.21.200:443 ESTABLISHED 5756
TCP 192.168.1.70:49692 204.79.197.200:443 ESTABLISHED 6784
TCP 192.168.1.70:49693 65.52.108.255:443 ESTABLISHED 3028
TCP 192.168.1.70:49696 13.90.46.155:443 ESTABLISHED 2180
TCP [2001:56a:7048:e00:d08c:411c:8fd9:5178]:49676 [2600:1409:a:18c::57]:80 ESTABLISHED 3536
TCP [2001:56a:7048:e00:d08c:411c:8fd9:5178]:49679 [2600:1409:a:18c::57]:80 ESTABLISHED 3536
TCP [2001:56a:7048:e00:d08c:411c:8fd9:5178]:49683 [2600:1409:a:197::76a]:443 ESTABLISHED 1320
here is my tasklist -svc
Image Name PID Services
========================= ======== ============================================
System Idle Process 0 N/A
System 4 N/A
smss.exe 360 N/A
csrss.exe 604 N/A
wininit.exe 680 N/A
csrss.exe 692 N/A
winlogon.exe 764 N/A
services.exe 816 N/A
lsass.exe 824 KeyIso, SamSs, VaultSvc
svchost.exe 924 BrokerInfrastructure, DcomLaunch, LSM,
PlugPlay, Power, SystemEventsBroker
svchost.exe 1004 RpcEptMapper, RpcSs
dwm.exe 1108 N/A
svchost.exe 1148 Appinfo, BITS, DoSvc, gpsvc, iphlpsvc,
LanmanServer, lfsvc, ProfSvc, Schedule,
SENS, ShellHWDetection, Themes,
UserManager, winmgmt, WpnService
svchost.exe 1192 Wcmsvc
svchost.exe 1236 BFE, CoreMessagingRegistrar, DPS, MpsSvc
svchost.exe 1252 AudioEndpointBuilder,
DeviceAssociationService, hidserv,
NcbService, NgcSvc, PcaSvc, SysMain,
TrkWks, wudfsvc
svchost.exe 1284 Dhcp, EventLog, lmhosts, NgcCtnrSvc, RmSvc,
TimeBrokerSvc, wscsvc
svchost.exe 1512 CDPSvc, EventSystem, FontCache, netprofm,
nsi, WdiServiceHost, WinHttpAutoProxySvc
svchost.exe 1572 CryptSvc, Dnscache, LanmanWorkstation,
NlaSvc
WUDFHost.exe 1668 N/A
igfxCUIService.exe 1680 igfxCUIService1.0.0.0
svchost.exe 1844 Audiosrv
svchost.exe 1980 Wlansvc
spoolsv.exe 504 Spooler
svchost.exe 812 WbioSrvc
DptfPolicyCriticalService 2112 DptfPolicyCriticalService
BTDevMgr.exe 2120 BTDevManager
svchost.exe 2128 StiSvc
svchost.exe 2136 StateRepository, tiledatamodelsvc
DptfParticipantProcessorS 2148 DptfParticipantProcessorService
DptfPolicyLpmService.exe 2172 DptfPolicyLpmService
nav.exe 2180 NAV
svchost.exe 2212 DiagTrack
Memory Compression 2332 N/A
nav.exe 2948 N/A
sihost.exe 2992 N/A
svchost.exe 3028 CDPUserSvc_2aec0, OneSyncSvc_2aec0,
PimIndexMaintenanceSvc_2aec0,
UnistoreSvc_2aec0, UserDataSvc_2aec0
PresentationFontCache.exe 3052 FontCache3.0.0.0
taskhostw.exe 3136 N/A
igfxEM.exe 3376 N/A
igfxHK.exe 3400 N/A
igfxTray.exe 3444 N/A
explorer.exe 3536 N/A
RuntimeBroker.exe 3604 N/A
SearchIndexer.exe 3988 WSearch
ShellExperienceHost.exe 4016 N/A
SearchUI.exe 2012 N/A
backgroundTaskHost.exe 3124 N/A
RemindersServer.exe 4112 N/A
smartscreen.exe 4472 N/A
cmd.exe 4528 N/A
conhost.exe 4536 N/A
cmd.exe 4624 N/A
conhost.exe 4632 N/A
DptfPolicyLpmServiceHelpe 4680 N/A
Lenovokb.exe 4704 N/A
dasHost.exe 4940 N/A
LSCNotify.exe 5644 N/A
Taskmgr.exe 5984 N/A
svchost.exe 2820 SSDPSRV
backgroundTaskHost.exe 1160 N/A
backgroundTaskHost.exe 1320 N/A
PlacesServer.exe 5756 N/A
backgroundTaskHost.exe 6752 N/A
backgroundTaskHost.exe 6784 N/A
SettingSyncHost.exe 6880 N/A
PlacesServer.exe 7088 N/A
tasklist.exe 7976 N/A
WmiPrvSE.exe 8020 N/A