Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Thursday, October 8, 2015 6:06 AM | 2 votes
Hello, Windows 10 pupils in the class using a password without the user's authorization is a problem, says that the password is incorrect, the user, Windows 7, 8, 8.1 to enter a username without any problems.
All replies (11)
Thursday, October 8, 2015 10:06 AM | 1 vote
not quite understanding what you're trying to do here? Are you trying to create a user on a Windows 10 machine with a blank password? Are you trying to connect to another machine with a user that has a blank password?
Friday, October 9, 2015 7:23 AM | 3 votes
Hi,
I can repro your issue that when I disable following group policy, the blank password domain user fail to login with following error:
Computer Configuration\Windows Settings\Security Settings\Account Policies\Password Policy\Minimum password length set as 0
Computer Configuration\Windows Settings\Security Settings\Account Policies\Password Policy\Passwords must meet complexity requirements of the installed password filter set as Disable
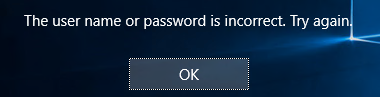
It seems an potential issue, I will report it up. Please also feedback in Windows Feedback App.
Please remember to mark the replies as answers if they help, and unmark the answers if they provide no help. If you have feedback for TechNet Support, contact [email protected].
Tuesday, October 20, 2015 5:01 PM | 1 vote
Hi Kate,
This problem is affecting me as well. Please let us know of any solutions or workarounds if you find any. Thanks!
Wednesday, October 21, 2015 9:34 AM | 1 vote
I'm facing same issue, for the moment I couldn't find any workaround....
Wednesday, October 21, 2015 10:27 AM | 1 vote
You may want to try this:
1. Open Local Security Policy by running secpol.msc,
2. Navigating to "password policy" under "account policies"
3. Edit the "minimum password length" setting to "0 characters."
Thursday, October 22, 2015 1:29 PM | 1 vote
The local setting "minimum password length" is already set to 0 (no password required) by default, at domain level the policy is OK. Users with empty passwords are allowed, but Windows 10 always prevents the login with error "The username or password is incorrect".
Monday, October 26, 2015 7:21 AM
There was a similar issue reported some time ago with HTTP header authentication being broken when W10 tries to authenticate a domain user to Server 2008R2 and later - with a bank password field.
A downloadable patch fixed that - but it resurfaced recently - maybe a recent update has squashed the patch... ? I have 10 desktops that can't login to the domain any more - which also work fine as Windows 7 Pro...! But after W10 upgrade they're all *broken *(I have to use a different user login profile that has a password string configured the site is for a bunch of retirees that barely remember their names, let alone passwords!)
Wednesday, December 2, 2015 7:09 PM | 2 votes
Hi,
I was just informed that this problem is now resolved with the November (1511) update for Windows 10.
Thanks!
Monday, March 7, 2016 6:26 PM
It Is the build update! :)
Monday, August 29, 2016 8:15 PM
This problem persists with Windows 10 Enterprise LTSB 2015, build 10240 even after updates.
It is not present under Windows 10 Enterprise, build 10586.
Is there possibly a hotfix patch to ammend this issue in the LTSB? It would be lovely to be able to not have to set a password currently only to turn around mid-year and re-deploy an OS in order to have the resolved issue in the 2016 LTSB.
Wednesday, January 11, 2017 3:15 PM | 1 vote
We just ran into this issue at our campus and I confirmed that for our issue on LTSB 2015 10240, if the password had EVER been set/initialized to blank or some other password and then set to blank, login for the account will NOT work under any condition for LTSB 2015. HOWEVER, recreating the account with "net user accountname /add /domain" (specifically NOT specifying the password at the time of creation) and then setting the attributes as needed from ADUC FIXES the problem. This is because creating the user with "net user" from the command line and not specifying a password at the time of creation establishes an uninitialized or null password, vs. establishing an initialized password. Once a password is set/reset on an account, it becomes initialized and resetting it to blank will never uninitialize it - so the only fix is to recreate. I also tried programmatically setting the password to a null string using powershell Set-ADAccountPassword and there is no facility for supplying a null as the source for the secure string...
Apparently in other versions of the Windows, the OS will attempt a password auth using no password and a blank password...very strange, only thing I can think of is that it's for backward compatibility.
This specific scenario had nothing to do with the min password length or password complexity... Oh and it should also be noted that local computer accounts (non-domain) were unaffected in blank vs uninitialized passwords so it must be just the AD auth api...