Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Friday, December 8, 2017 3:42 PM
Hello!
Please let me clarify a couple of questions regarding EAP and IKEv2 VPN.
The theory:
https://technet.microsoft.com/en-us/library/cc754179%28v=ws.10%29.aspx?f=255&MSPPError=-2147217396
"The NPS server authenticates the user and client computer with the authentication type that is selected for use with PEAP. The
authentication type can be either EAP-TLS (smart card or other certificate) or EAP-MS-CHAP v2 (secure password)."
From this I conclude that if I want to use EAP-TLS my clients will authenticate using ONLY their user certificates.
The practice:
/en-us/windows-server/remote/remote-access/vpn/always-on-vpn/deploy/always-on-vpn-deploy-overview
This guide suggests to create the network policy that checks the security group membership:

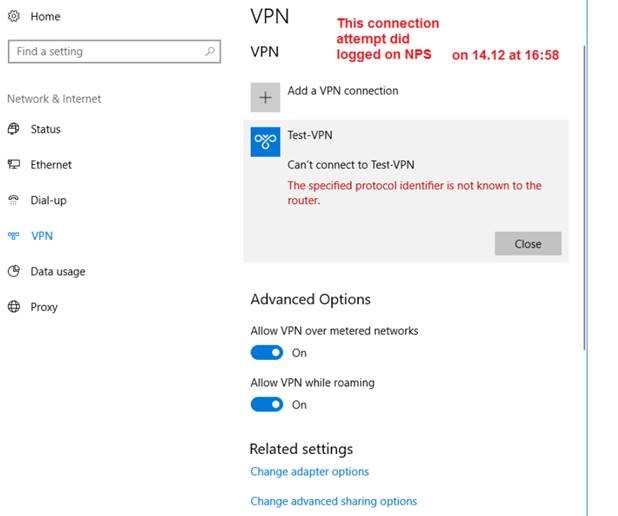
When I'm trying to connect to the VPN server I see that user name and domain information really gets logged on my NPS server :

...so
Q1: If EAP-TLS does NOT use user name/password checking how this information (domain/username) can reach NPS server?
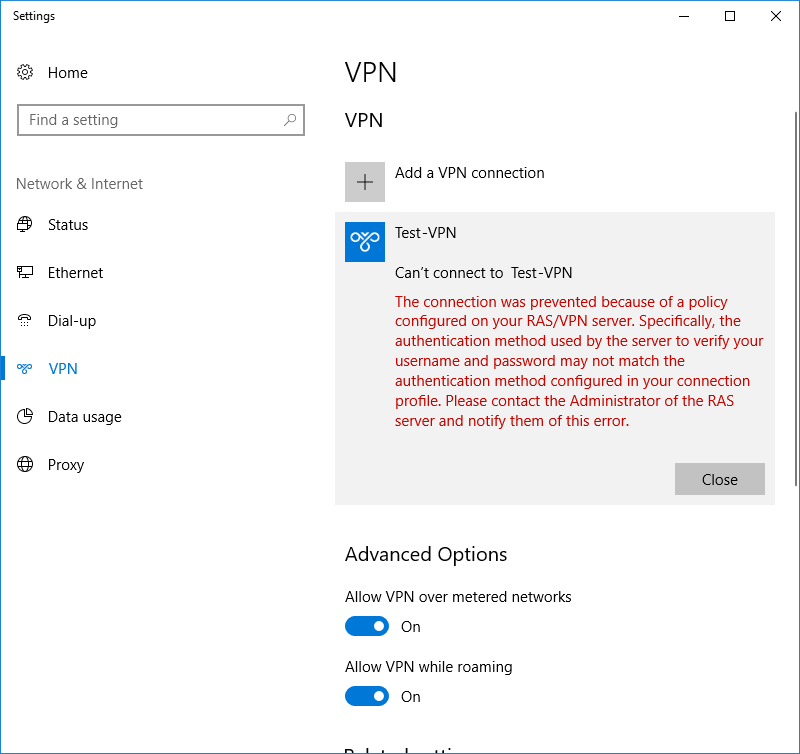
Q2: When I connect to VPN using IKEv2 protocol I see in the accounting log on NPS server that the connection attempt was successfull (and there are no errors on VPN or NPS server in the logs) but on the client I get this:
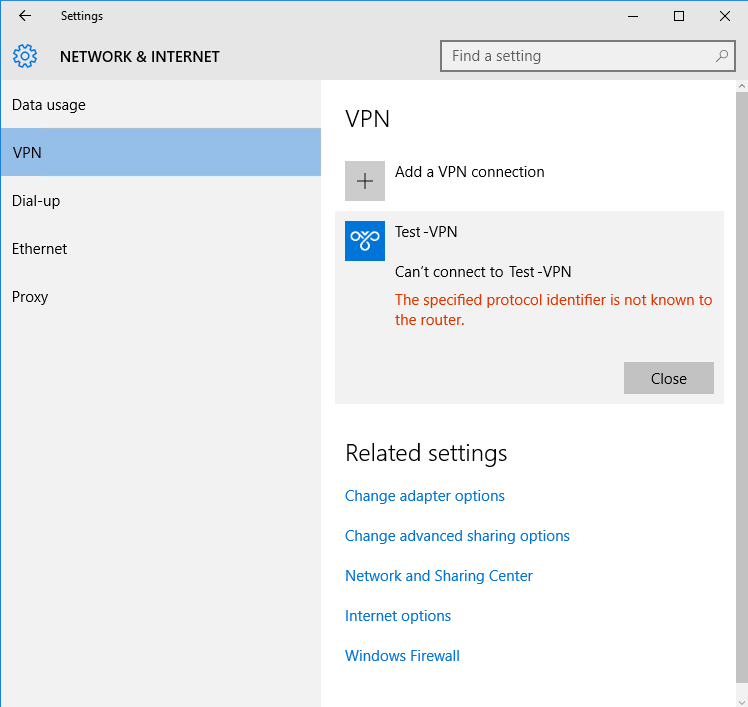
The error in the client's application log:
"The user Test\user1 dialed a connection named Test-VPN which has failed. The error code returned on failure is 902."
The error in the vpn server's log:
"[4544] 12-11 12:15:05:411: DeviceListenRequest: Clearing Autoclose flag on port VPN2-3
[4544] 12-11 12:15:05:411: onecoreuap\net\rras\ras\rasman\rasman\util.c: 2789: port 509 state chg: prev=4, new=1
[4544] 12-11 12:15:05:411: onecoreuap\net\rras\ras\rasman\rasman\util.c: 2820: port 509 async reqtype chg: prev=0, new=27
[4544] 12-11 12:15:05:411: Listen posted on port: VPN2-3, error code 600"
I failed to find any explanation to this issue ...
This error is being discussed here but there also seems to be no solution.
Thank you in advance,
Michael
All replies (20)
Tuesday, June 5, 2018 12:14 PM ✅Answered | 4 votes
Hi All,
after having the same isse (error 902) I called upon MS premier support who where able to give me the solution in 2 min.
The problem for the 902 error is normally an issue with ipv6 being disbaled on the system.
So if you have this issue please check the following:
* no GPO disabling ipv6
HKLM\SYSTEM\CurrentControlset\Services\Tcpip6\Parameters DisableComponents (DWORD) with dec value of 32Verify that ipv6 is selected on both of the networkadapters
Reboot server
Add the ipv6 key of the remoteaccess server back and restart the RRAS service
(HKLM\SYSTEM\CurrentControlSet\Services\RemoteAccess\remoteManagers\IPV6)
Monday, August 12, 2019 2:18 PM ✅Answered
Very glad to find your posting, sorry it had to come to using MS premier support, but the other info/comments about the cryptic 902 message online haven't helped much. You saved me from wasting more time troubleshooting.
One minor correction, the registry Key to add back in is the following, minor typo that people probably figure out...
HKLM\System\CurrentControlSet\Services\RemoteAccess\RemoteManagers\IPv6
The info helped a bunch.
Monday, December 11, 2017 3:24 AM
Hi,
Thank you for your question.
I am trying to involve someone familiar with this topic to further look at this issue. There might be some time delay. Appreciate your patience.
Thank you for your understanding and support.
Best Regards,
Frank
Please remember to mark the replies as answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Monday, December 11, 2017 7:37 AM
Thank you very much for the help, frank_song!
Regards,
Michael
Tuesday, December 12, 2017 3:40 PM
I did some more testing and came to the conclusion that the initial theory (and my conclusion that was based on it) was either wrong or at least incomplete:
"*"The NPS server authenticates the user and client computer with the authentication type that is selected for use with PEAP. The * authentication type can be either EAP-TLS (smart card or other certificate) or EAP-MS-CHAP v2 (secure password)."
From this I conclude that if I want to use EAP-TLS my clients will authenticate using ONLY their user certificates."
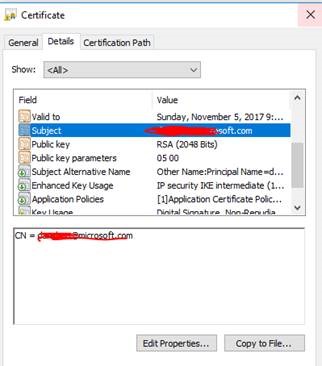
- the key point here is that even when using certificate-based EAP authentication the user name (but not the password) is also sent to the VPN/NAS servers: it can be seen by ticking the following checkbox:

After that the user can choose another certificate AND user name:

And if this another user is not a member of the group (VPN Users) for which the Network Policy has a permission to connect to the network, the corresponding error will arise:

The NPS log:
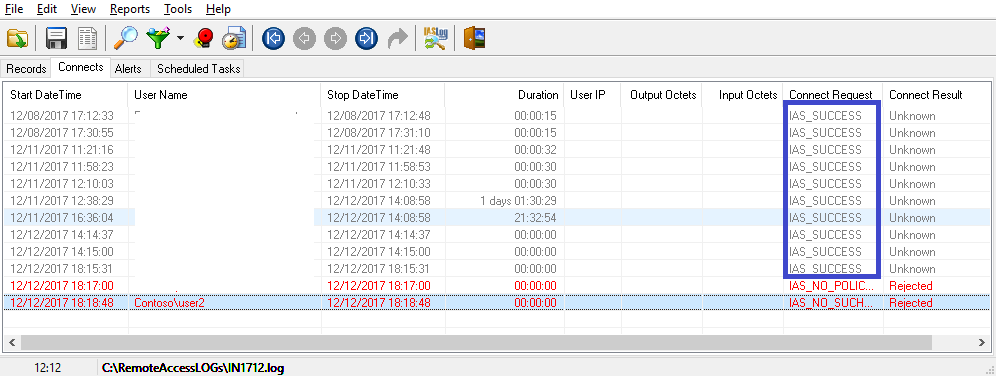
I just don't understand why no MS documents I've come across so far have ever mentioned that user name does get sent to VPN/NPS server along with the user certificate.
Thursday, December 14, 2017 10:48 AM
Q1: If EAP-TLS does NOT use user name/password checking how this information (domain/username) can reach NPS server?
Using PEAP under NPS, we can choose EAP-TLS or EAP-MS-CHAP v2 methods. If we choose EAP-TLS, we can use the client certificates, including either user certificates or computer certificates. If client uses the user certificate, it will be sent to NPS server, NPS server will extract the subject name of this user certificate, and make the LDAP query for DC, and make the following authentication check. If passed from DC response, NPS will grant the allow permission, and notify the VPN server that user has be granted.
Note: The same for computer certificate, we can also use the computer certificate for EAP-TLS authentication adding computer name into the subject name of one computer certificate.
Q2: When I connect to VPN using IKEv2 protocol I see in the accounting log on NPS server that the connection attempt was successful (and there are no errors on VPN or NPS server in the logs) but on the client I get this: failure 902 : The specified protocol identifier is not known to router.
Since NPS radius returns success to VPN server, but client Win10 PC still cannot succeed to dial the IKEv2 VPN, it seems that some phase goes abnormal, and we have to capture some logs and files for the analysis.
Can help to make the following teat and capture according to A,B,C?
[A] First of all, enable IKE logging:
Enable IKE logging
1. Enable IKElogging in registry: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\IKEEXT\Parameters\EnableLogging: DWORD, value=1
2. Restart "IKE and AuthIP IPsec Keying Modules" service (IKEEXT) (net stop ikeext && net start ikeext)
[B] two tests
Test 01:
Step 1: Under Client Win10 PC client, execute the Cmd as administrator, and run the following command:
netsh ras set tracing * enabled
netsh trace start capture=yes report=yes
Step 2: Reproduce this issue, dial VPN, and got the 902 failure.
Step 3: execute the following commands based on step1:
netsh trace stop
netsh ras set tracing * disabled
<collect logs: netsh trace output and files in %windir%\Tracing>
Test 02:
Step 1: Create one folder named “temp” under C disk. Under Client Win10 PC client, execute the Cmd as administrator, and run the following command:
netsh trace start scenario=WFP-IPsec capture=yes persistent=yes tracefile=c:\temp\NetTrace.etl
Step 2: Reproduce this issue, dial VPN, and got the 902 failure.
Step 3: execute the following commands based on step1:
netsh trace stop
[C] disable IKE logging and upload the files
1. Disable IKElogging in registry to flush the logs to file: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\IKEEXT\Parameters\EnableLogging: DWORD, value=0
2. Restart "IKE and AuthIP IPsec Keying Modules" service (IKEEXT) (net stop ikeext && net start ikeext)
3. Pick up the log file: %systemroot%\System32\Ikeext.etl
Step 4:
- Upload the Nettrace.etl , Ikeext.etl files and all files in %windir%\Tracing
- Upload the application log and system log of win10 client to us.
You could upload log to onedrive.
Please note your private message.
Best Regards
Frank
Please remember to mark the replies as answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Thursday, December 14, 2017 1:10 PM
First of all, thank you so much for your explanation regarding user names in EAP-TLS - I've never seen such explanations on EAP-TLS.
Of course I'll do all the tests, upload the files and post back!
Would you please also help with this:
"NPS server will extract the subject name of this user certificate, and make the LDAP query for DC, and make the following authentication check" - it means the certificate alone would be sufficient for user authentication, but in this case why does the posibsility exist to supply a certificate AND a user name separately???
I tried to supply the certificate for the user which is a member of the VPN users group ([email protected]) and the username of another user who is ALSO a member of the VPN users group ([email protected]) - in this test authentication failed.
It means that (presumably) the certificate name (the name of the user who requested the certificate) and the user name in the User field should be the same even if both "users" are members of the same group.
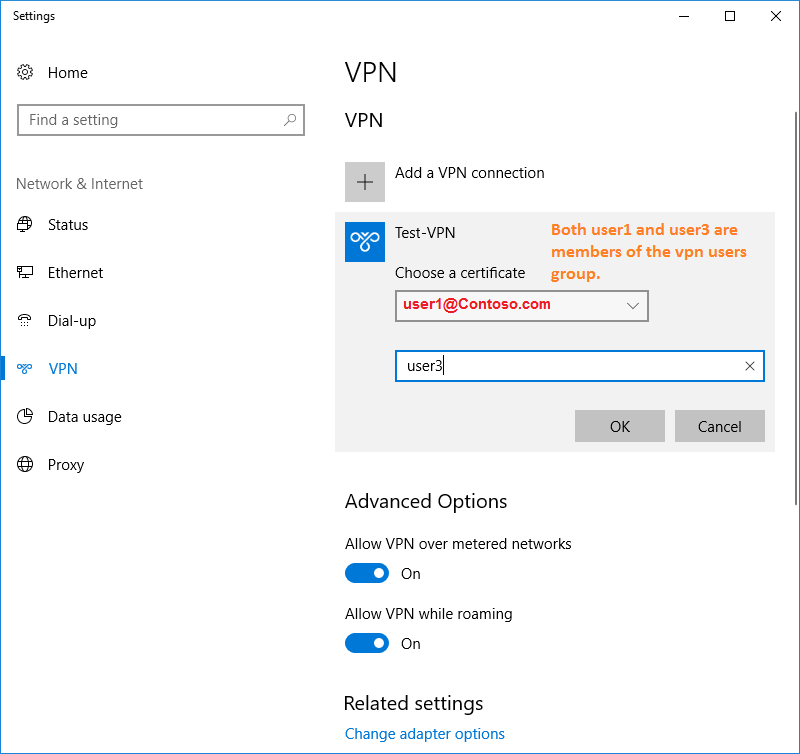

2) "Note: The same for computer certificate, we can also use the computer certificate for EAP-TLS authentication adding computer name into the subject name of one computer certificate." - does it mean I create the group containing computer accounts (~VPN Computers) and provide access based on computer names derived from the computer certificates?
Regards,
Michael
Thursday, December 14, 2017 2:23 PM
Here's the link:
https://1drv.ms/f/s!Aknw3yl5aLH6gQJxfhb43Or4m5iv
Tuesday, December 19, 2017 1:46 AM
Hi,
Here comes the VPN issue reported in the forum, please check it:
Q1:"NPS server will extract the subject name of this user certificate, and make the LDAP query for DC, and make the following authentication check" - it means the certificate alone would be sufficient for user authentication, but in this case why does the posibsility exist to supply a certificate **AND **a user name separately???
I tried to supply the certificate for the user which is a member of the VPN users group ([email protected]) and the username of another user who is ALSO a member of the *VPN users *group ([email protected]) - in this test authentication failed.
It means that (presumably) the certificate name (the name of the user who requested the certificate) and the user name in the *User *field should be the same even if both "users" are members of the same group.
Answer:
First, what does the “User a different user name for the connection” check box mean?
l If you want to use a different user name when the username is the smart card or certificate is not the same as the user name in the domain that you are logging on to, select the “User a different user name for the connection” check box
l If, for example, you work for a consulting company where you need to log on to the domain of the company to which you are assigned, but your smart card contains a user name specific to your home company, select the Use a different user name for the connection check box.
l If you select the Use a different user name for the connection check box, your certificate is exported without private keys and submitted to the administrator of your remote server to be explicitly mapped to your domain user account.
Second, but when you choose another different certificate, you should bind it with the correct domain username in Active Directory, that means the different user name is mapped/enrolled with your configured Certificate. The scenarios we mostly suffered, we can refer to the above.
Q2: *"Note: The same for computer certificate, we can also use the computer certificate for EAP-TLS authentication adding computer name into the subject name of one computer certificate." - *does it mean I create the group containing computer accounts (~VPN Computers) and provide access based on computer names derived from the computer certificates?
Answer:
Yes,you can create the groups contains domain computer accounts under NPS server.
Incident issue:
Suggestion: Could you help to check whether there is any NAT device between these two IPs: 10.3.0.63(RRAS Server), 10.3.3.50(VPN client).
If have, could help to remove VPN testing environment into another pure routing environment without NAT?
Or please follow the suggestion from this KB:
Best Regards,
Frank
Please remember to mark the replies as answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Tuesday, December 19, 2017 1:45 PM
Hi Frank,
Thank you very much for your answers!
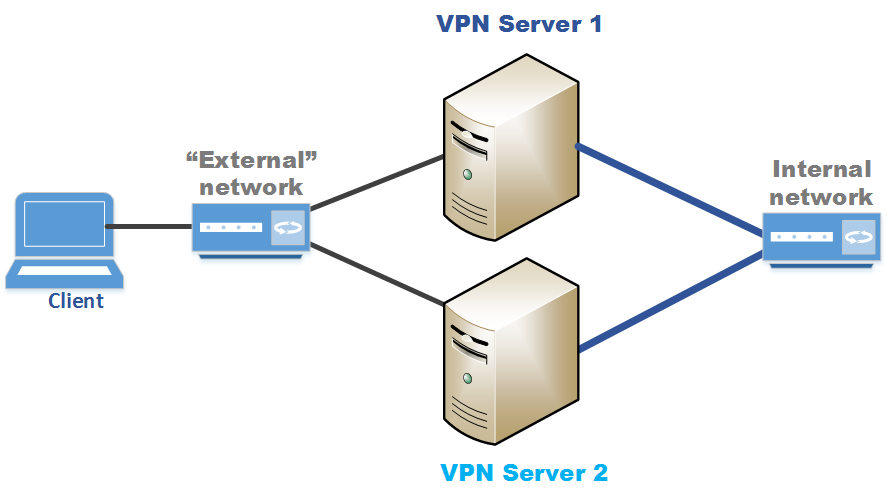
Regarding the NAT: there's no NAT device between the client and the vpn server: the network topology is very simple:
Yesterday I've installed the second vpn server - vpn2.contoso.com - (with exactly the same settings!!!) and tried to connect to the test internal network using the same vpn ikev2 connection created on my Client1 computer. All worked without a hitch! I even tried a "plain" computer certificate authentication (e.g. not the PEAP authentication) - it also worked without issues while I failed to connect to vpn server 1 using both PEAP and the computer certificate.
I then compared the settings on VPN1 and VPN2 and found no difference:




So I just can surmise that it is the computer itself (vpn server 1) which is causing the "The specified protocol identifier is not known to the router" error - is it possible that this error can sterm from some network adapter/motherboard etc. ... compatability issues?
If it is, it would be rather miserable situation because I can easily replace one test computer with another but what if the real server refuses to work in a production network?...
Regards,
Michael
Tuesday, December 19, 2017 2:26 PM
P.S. VPN Server 1 is also the ARR server - may it have any impact on RRAS?
Wednesday, December 20, 2017 4:17 AM
Hi,
Please disable windows firewall or any other third-party firewall under VPN Server 1 and check it further.
Best Regards,
Frank
Please remember to mark the replies as answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Wednesday, December 20, 2017 8:15 AM
Hi Frank,
There is no firewall on vpn server 1 (as well as on vpn server 2):
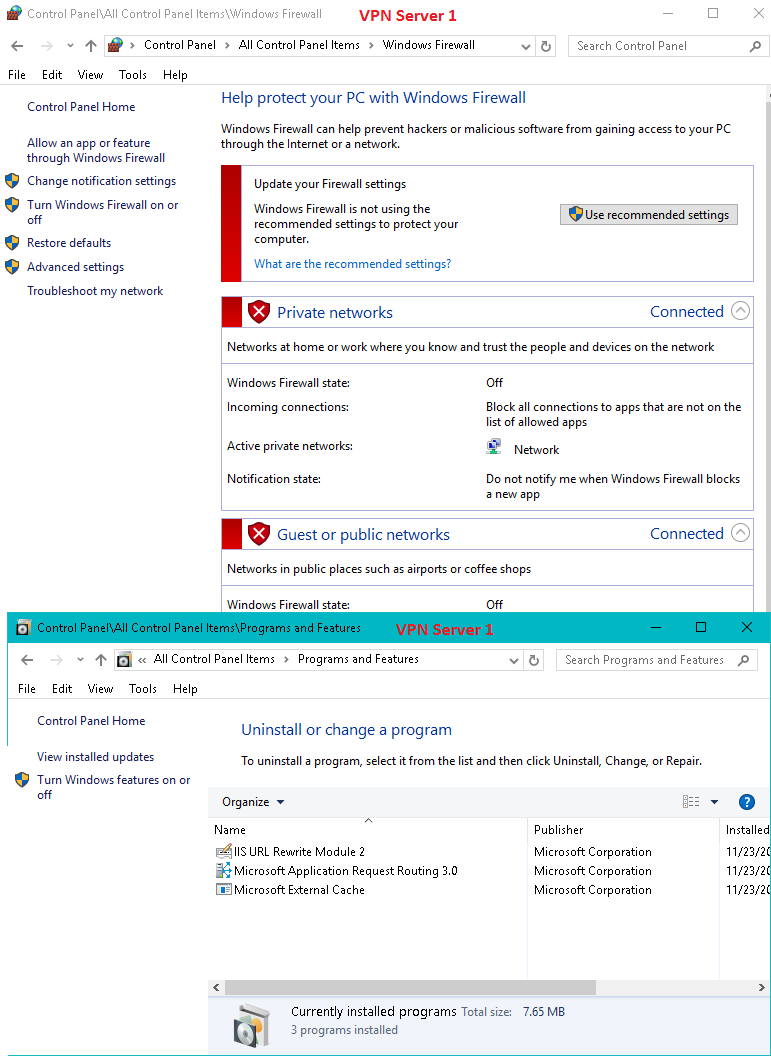
Would you please also comment on this:
"l If you select the Use a different user name for the connection check box, your certificate is exported without private keys and submitted to the administrator of your remote server to be explicitly mapped to your domain user account."
- I'm a bit confused by this explanation because as far as I see when I select the Use a different user name... checkbox the sole result of it is the appearing of the extra window in which I can type a different user name and/or select another certificate...
Regards,
Michael
Monday, December 25, 2017 9:21 AM
Hi,
Based on the complexity and the specific situation, we need do more researches. If we have any updates or any thoughts about this issue, we will keep you posted as soon as possible. Your kind understanding is appreciated. If you have further information during this period, you could post it on the forum, which help us understand and analyze this issue comprehensively.
Sorry for the inconvenience and thank you for your understanding and patience.
Best Regards,
Frank
Please remember to mark the replies as answers if they help and unmark them if they provide no help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Tuesday, December 26, 2017 9:58 AM
Thank you for your help, Frank!
Friday, January 12, 2018 5:24 PM
MF47, have you figured this out? I have a similar issue with my vpn server - any configuration I do ends up with "the specified protocol identifier is not known to the router"
Tuesday, January 23, 2018 10:07 AM
No, but I've reinstalled vpn on another test server and all worked as expected. Nevertheless, I don't know how to troublshoot this error should it ever happen again...
Here's the configuration that worked out for me:
https://michaelfirsov.wordpress.com/testing-ikev2-vpn-with-peap-authentication-in-windows-server-2016-part1/
Monday, June 11, 2018 4:40 PM
In my Windows 10 client, I don´t have Type of Sign-Info: PEAP. What win10 build are you using?
I use "certificate" selection here.
MCSE Mobility 2018. Expert on SCCM, Windows 10 and MBAM.
Wednesday, August 14, 2019 1:16 PM
Thank you all for your help!
Regards,
Michael
Saturday, February 22, 2020 11:44 PM
2 years later and your answer is still valid. Thanks, man. I was going to throw my servers out of the window...