Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Monday, September 10, 2018 7:33 AM | 1 vote
What rights would you give someone who should only be able to start/stop a VM and connect (RDP) to the VM via the Azure Portal?
Virtual Machine Contributor doesn't seem to cut it. It allows starting/stopping the VM but when using the portal "Connect" button the user gets: "You do not have permission to view network interface with ID: /subscriptions/..../resourceGroups/.../providers/Microsoft.Network/networkinterfaces/networkinterfacename".
Currently I'm using "Virtual Machine Contributor" rights on the VM in combination with "Reader" rights on the networkinterface. Still it feels a a bit off. Why wouldn't Microsoft give the role Virtual Machine Contributor rights to the underlying networkinterface?
All replies (8)
Monday, September 10, 2018 10:55 AM ✅Answered | 1 vote
I thought those groups were for Linux VM's only but I must have mistaken. I created a test user and granted it the "Virtual Machine Administrator Login" role. When (re)starting/stopping the VM you receive the error "...does not have authorization to perform action 'Microsoft.Compute/virtualMachines/start/action'...".
When connecting to the running VM via the Connect button you get:
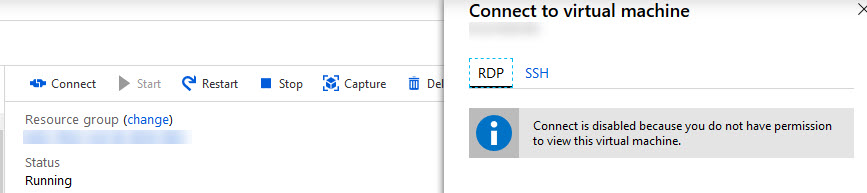
So using "Virtual Machine Contributor" rights on the VM in combination with "Reader" rights on the networkinterface still seems to be the most valid/secure option unless I'm missing something?
Monday, September 10, 2018 8:44 AM
Hello,
Try assigning the user to the 'Virtual Machine User Login' role.
Monday, September 10, 2018 9:52 AM | 1 vote
As said by "Ioannis Gantsidis" you can assign " 'Virtual Machine User Login' role. You can also assign " 'Virtual Machine Administrator Login' role that allows read access to public ip address, virtual network, load balancer and network interface definitions.
If you need a user role with access to VM's underlying network and storage account, grant "Contributor" role at the resource group level.
If this answer was helpful, click “Mark as Answer” and Up-Vote. To provide additional feedback on your forum experience, click here
Tuesday, September 11, 2018 7:37 AM | 1 vote
As said in the previous post, you need to give contributor role at RG level to accomplish your scenario.
Sunday, September 16, 2018 5:57 AM
Checking in to see if the above suggestions helped or you need further assistance on this issue. If that answers your query, do click “Mark as Answer” and Up-Vote for the same.
Monday, March 11, 2019 1:59 PM
Granting "Contributor" role at the resource group level solved the issue for me.
Thursday, July 25, 2019 7:14 PM
Additional information for those using a Load Balancer.
Do not assign permission to the resource group, this is not best practice for least permissions. You should apply the "read" permission to the resource(s).
If your VM is behind a Load Balancer you will also need to assign the "read" permission to
1. NIC - Allows you to download the RDP client
2. Load Balancer - Required for the port if using a NAT
3. Public IP address assigned to the Load Balancer - Required for the public IP
Thursday, July 25, 2019 7:15 PM
Do not assign permission to the resource group, this is not best practice for least permissions necessary. You should apply the "read" permission to the necessary resource(s) only.