Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Monday, July 30, 2012 6:39 PM
I have a 2 x 2003 domain controller that have DNS and DHCP Services installed
I was thinking of configuring DHCP to use a service account to update DNS records.
If I set this, do the DHCP Servers need to be members of the DNSUpdateProxy security group for the service account to work?>
All replies (41)
Monday, July 30, 2012 8:12 PM ✅Answered | 1 vote
Late edit, 5/31/2013 - From researching this further and speaking to the product group at Microsoft, you need both, the DnsUpdateProxy group and credentials to make this work. See my latest post, 5/31/2013, posted below for more specifics. If you are having any issues getting this to work, and have followed these basic rules and it's still not working, I highly recommend contacting Microsoft support for specific assistance with your environment and configuration.
===================================
No, they don't. You would choose to use one or the other, not both. If you use both, it will default to the group. And besides, you do not want to use the group if on a DC, or it reduces security.
.
Here's more on the whole thing:
This link covers the following:
DHCP Service Configuration, Dynamic DNS Updates, Scavenging, Static Entries, Timestamps, DnsUpdateProxy Group, DHCP Credentials, prevent duplicate DNS records, DHCP has a "pen" icon, and more...
Published by Ace Fekay, MCT, MVP DS on Aug 20, 2009 at 10:36 AM 3758 2
http://msmvps.com/blogs/acefekay/archive/2009/08/20/dhcp-dynamic-dns-updates-scavenging-static-entries-amp-timestamps-and-the-dnsproxyupdate-group.aspx .
.
DNS Record Ownership and the DnsUpdateProxy Group
"... to protect against unsecured records or to permit members of the DnsUpdateProxy group to register records in zones that allow only secured dynamic updates, you must create a dedicated user account and configure DHCP servers to perform DNS dynamic updates with the credentials of this account (user name, password, and domain). Multiple DHCP servers can use the credentials of one dedicated user account."
http://technet.microsoft.com/en-us/library/dd334715(WS.10).aspx
.
DNS Secure Dynamic Update
"Caution:
If you have installed the DHCP service on a domain controller, be absolutely certain not to make that server a member of the DNS Update Proxy group. Doing so would give any user or computer full control of the DNS records corresponding to the domain controllers, unless you manually modified the corresponding ACL. Moreover, if a DHCP server that is running on a domain controller is configured to perform dynamic updates on behalf of its clients, that DHCP server is able to take ownership of any record, even in the zones that are configured to allow only secure dynamic update. This is because a DHCP server runs under the computer account, so if it is installed on a domain controller it has full control over DNS objects stored in the Active Directory."
http://technet.microsoft.com/en-us/library/cc961412.aspx
.
Ace Fekay
MVP, MCT, MCITP EA, MCTS Windows 2008/R2, Exchange 2007 & Exchange 2010, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Monday, July 30, 2012 8:47 PM
Thank you Ace. That is very informative.
DHCP is on my domain controller and based on the information available it would be very dangerous to have this a member of the DNSProxyUpdate group. I visualise a linux computer connected to our infrastructure with the same name as one of our core servers, DHCP would essentially overwrite the existing server static record with linux record as this will perform non secure updates. By using a dedicated account it will only perform secure updates?
Monday, July 30, 2012 9:02 PM
Hi Ace
I was just looking at one of the links you posted and it states the following:
"To solve this problem, you can use a built-in security group called DnsUpdateProxy. However, to protect against unsecured records or to permit members of the DnsUpdateProxy group to register records in zones that allow only secured dynamic updates, you must create a dedicated user account and configure DHCP servers to perform DNS dynamic updates with the credentials of this account (user name, password, and domain). Multiple DHCP servers can use the credentials of one dedicated user account."
To me this suggests that you use the DNSUpdateProxy group in conjunction with the dedicated user account, the latter preventing against unsecured records or registering records in zones that only accept secure dynamic updates? It kind of contradicts itself no?
Monday, July 30, 2012 9:38 PM
Yea, it's a bit of a security risk!!
With the credentials method, DHCP will use those credentials to perform updates under that account, and can be updated when the record's IP changes. Just make sure you set DHCP DNS tab to force updates for all DHCP requests so DHCP owns all leased records.
Ace Fekay
MVP, MCT, MCITP EA, MCTS Windows 2008/R2, Exchange 2007 & Exchange 2010, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Monday, July 30, 2012 9:42 PM
It should be one or the other. I actually just emailed one of our contacts at Microsoft to clarify why it implies both. Hang in there for a response, which may not be today. In the meantime, jsut follow what I recommended, because that's how I've been doing it successfully for the past 6 years. :-)
Ace Fekay
MVP, MCT, MCITP EA, MCTS Windows 2008/R2, Exchange 2007 & Exchange 2010, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Thursday, August 2, 2012 3:01 PM
Ace
I tried your guidelines but I've having problems achieving what I want.
I configured my Windows 2008 R2 DC/DHCPs server as your article suggests. I used a standard windows user account as the DHCP service credential (see picture attached)
My observations:
1. User logon to Computer A receiving IP (192.168.1.50) from DHCP Server A.
2. Shutdown DC/DHCP Server to test resilience. IPCONFIG /release is runon Computer A. PTR records remains.
3. Computer A restarts. Obtains a new IP (192.168.1.100) from DHCP Server B. New PTR record is created for new IP (192.168.1.100). Reverse lookup zone now contains duplicate PTR records for Computer A. (192.168.1.50 & 192.168.1.100)
4. If I do an IPCONFIG /Release on Computer A, I noticed the PTR record for 192.168.1.100 is removed but 192.168.1.50 remains.
I thought using the DHCP service account on both DHCP servers would mean DNS PTR record of 192.168.1.50 would be updated by the DHCP service account rather than a new PTR record being created. My process seems to end up with multiple PTR records.
What am I missing?
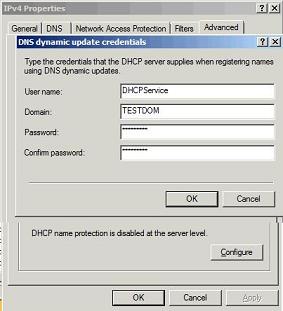
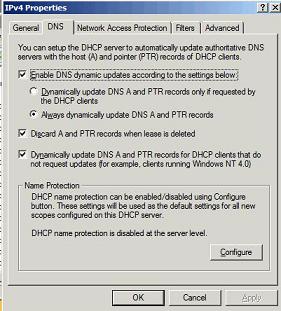
Thursday, August 2, 2012 4:52 PM
I assume before you tested this, an existing PTR didn't exist. When you look at the PTR's properties, security tab, who's the owner?
Ace Fekay
MVP, MCT, MCITP EA, MCTS Windows 2008/R2, Exchange 2007 & Exchange 2010, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Monday, August 6, 2012 11:40 AM
No PTR records existed, this was a new Windows XP VM that I provisioned and followed the above process. When I look at both PTR records, the owner is the DHCPService account. One record is stale, the other is valid. I'm assuming enabling scavenging will remove the state PTR record but to be honest I was expecting the DHCPService account to delete and update the existing PTR record.
Monday, August 6, 2012 4:45 PM
Delete both stale and new record, and try again.
Yes, scavenging will help. I assumed you had scavenging enabled? Sorry for the assumption, I should have asked. You know what they say about assuming? Follow my blog on scavenging to enable it. Make sure the lease is either greater than or equal to the scavenge periods and the lease is not less than 1 day.
Ace Fekay
MVP, MCT, MCITP EA, MCTS Windows 2008/R2, Exchange 2007 & Exchange 2010, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Tuesday, August 7, 2012 3:08 PM
Cheers Ace. I deleted both PTR records and started again. Same symptoms experienced.
Taking a step back, if I configure both DHCP servers to 'Dynamically update DNS A and PTR records only if requested by DHCP Clients’ (default Settings) and carry out the process described above, I get multiple PTR records which are owned by respective DHCP server that's issued the address. The DNS record security tab has DHCPA$ as the owner. This reflects what you described in your article. This explains why DNS records are not updated/managed if the DHCP server is replaced with a new one...quite simply it doesn't have permissions.
I then configured both DHCP servers to use Service Credentials and to 'Always dynamically update DNS A and PTR records' + Discard A and PTR records...etc.etc and carried out the process described above. I get multiple PTR records which are both owned by the DHCPService. The DNS record security tab has DHCPService as the owner. This too reflects what you described in your article BUT I still have multiple PTR records that exist. My assumption was the DHCPService account would update the existing PTR record regardless of which DHCP distributed the IP address (as the DHCP Service accounts owns both record) so that only one PTR record exists. This doesn't appear to be the case.
I've enabled scavenging, the DHCP lease is set to 4 days, so the No Refresh is set to 2 days and the Refresh is set to 1 day. Based on what I tested above I assume this will clean up the reverse lookup zones of stale records but I thought by using the DHCP service credentials would negate the need for scavenging to be run.
Does my ramblings make sense?? This is all new to me and I want to make sure I'm on the right lines.
Tuesday, August 7, 2012 5:18 PM
Rambling is allowed. :-)
I would match the scavenge settings with the lease length.
Post a screenshot of the DHCP DNS tab.
Ace Fekay
MVP, MCT, MCITP EA, MCTS Windows 2008/R2, Exchange 2007 & Exchange 2010, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Wednesday, August 8, 2012 9:35 AM
Attached is a screenshot of the DHCP DNS tab.. This is the same configuration on both DHCP servers.
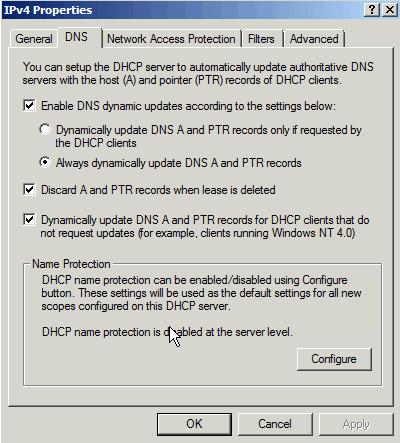
Friday, February 8, 2013 1:58 AM
Just to update this thread, the DnsProxyUpdate group AND DHCP Credentials must be used together. Just make sure nothing else other than DHCP servers are members of the group, or it may cause problems. For example, do not add a DNS server to the group.
I've updated my blog explaining this.
Thank you, and I apologize for the confusion.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Friday, May 31, 2013 11:21 AM
Just to update this thread, the DnsProxyUpdate group AND DHCP Credentials must be used together. Just make sure nothing else other than DHCP servers are members of the group, or it may cause problems. For example, do not add a DNS server to the group.
I've updated my blog explaining this.
Thank you, and I apologize for the confusion.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/This post is provided AS-IS with no warranties or guarantees and confers no rights.
What's the reason to put the DHCP Server into the DNSProxyUpdate Group?
From my understanding, after putting a DHCP Server into the DNSProxyUpdate Group, the only difference is that when the DHCP Server registers a record in DNS on behalf of a client, the authenticated users group has "write" access rights to this record which makes this DNS record insecure.
Now my question is, wouldn't it make more sense to just use DNS Dynamic Update Credentials, set these credentials to all DHCP serves in the organization, without adding the DHCP Server to the DnsProxyUpdate Group? Because this way, when a DHCP Server registes a record in DNS on behalf of the client, then the owner of the record is the Domain user account specified on the DNS Dynamic Update Credentials which make sense because then, if one DHCP Server would not be available for some reason, the other DHCP Server can update the record using the same user account specified DNS Dynamic Update Credentials. I just currently do not see the advantage of putting the DHCP Server(s) into the DNSProxyUpdate Group in this process.
Thanks for clarification.
Friday, May 31, 2013 3:36 PM
Just to update this thread, the DnsProxyUpdate group AND DHCP Credentials must be used together. Just make sure nothing else other than DHCP servers are members of the group, or it may cause problems. For example, do not add a DNS server to the group.
I've updated my blog explaining this.
Thank you, and I apologize for the confusion.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/This post is provided AS-IS with no warranties or guarantees and confers no rights.
What's the reason to put the DHCP Server into the DNSProxyUpdate Group?
From my understanding, after putting a DHCP Server into the DNSProxyUpdate Group, the only difference is that when the DHCP Server registers a record in DNS on behalf of a client, the authenticated users group has "write" access rights to this record which makes this DNS record insecure.
Now my question is, wouldn't it make more sense to just use DNS Dynamic Update Credentials, set these credentials to all DHCP serves in the organization, without adding the DHCP Server to the DnsProxyUpdate Group? Because this way, when a DHCP Server registes a record in DNS on behalf of the client, then the owner of the record is the Domain user account specified on the DNS Dynamic Update Credentials which make sense because then, if one DHCP Server would not be available for some reason, the other DHCP Server can update the record using the same user account specified DNS Dynamic Update Credentials. I just currently do not see the advantage of putting the DHCP Server(s) into the DNSProxyUpdate Group in this process.
Thanks for clarification.
John,
I got that information directly from Microsoft product owners. It's not an "advantage," rather both need to be configured for this to work. Here are my notes, but you've already read this thread and the links above. For your convenience, I'll post the relevant portions:
Why does the DnsUpdateProxy group needed in conjunction with credentials?
The technical reason is twofold:
DnsUpdateProxy:
Objects created by members of the DNSUpdateProxy group have no security; therefore, any authenticated user can take ownership of the objects.
DHCP Credentials:
Forces ownership to the account used in the credentials, which the DnsUpdateProxy group allowed to take ownership other than the registering client.
Otherwise, the default process is
Late Edit Note: This section was edited and updated on 3/3/2014 to reflect current operating systems behavior:
- By default, Windows 2000 and newer statically configured machines will register their own A record (hostname) and PTR (reverse entry) into DNS.
- If set to DHCP, a Windows 2000, 2003 or XP machine, will request DHCP to allow the machine itself to register its own A (forward entry) record, but DHCP will register its PTR (reverse entry) record.
- If Windows 2008/Vista, or newer, the DHCP server always registers and updates client information in DNS.
Note: "This is a modified configuration supported for DHCP servers
running Windows Server 2008 and DHCP clients. In this mode,
the DHCP server always performs updates of the client's FQDN,
leased IP address information, and both its host (A) and
pointer (PTR) resource records, regardless of whether the
client has requested to perform its own updates."
Quoted from, and more info on this, see:
http://technet.microsoft.com/en-us/library/dd145315(v=WS.10).aspx - The entity that registers the record in DNS, owns the record.
Note "With secure dynamic update, only the computers and users you specify
in an ACL can create or modify dnsNode objects within the zone.
By default, the ACL gives Create permission to all members of the
Authenticated User group, the group of all authenticated computers
and users in an Active Directory forest. This means that any
authenticated user or computer can create a new object in the zone.
Also by default, the creator owns the new object and is given full control of it."
Quoted from, and more info on this:
http://technet.microsoft.com/en-us/library/cc961412.aspx
-
DNS Record Ownership and the DnsUpdateProxy Group (explained here)
http://technet.microsoft.com/en-us/library/dd334715(v=ws.10).aspx
Secure Dynamic Update
http://technet.microsoft.com/en-us/library/cc961412.aspx
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Saturday, June 1, 2013 4:17 PM
Ace,
Many thanks for your answer. It would still be interesting to know the reason why the DNS Servers need to be added to the DnsUpdateProxy group, since based on my tests in the lab it is not neccessary to put the DHCP Servers into that group.
TechNet says the following about the DnsUpdateProxy group:
"DNS domain names that are registered by the DHCP server are not secure when the DHCP server is a member of the DnsUpdateProxy group."
Why are those entries not secure? Reason is, as soon as the DHCP Server is added to the DnsUpdateProxy, the authenticated users group has write access to that A record (assumed the DHCP Server registes the entry on behalf of the client and DNS Update Credentials is not configured):
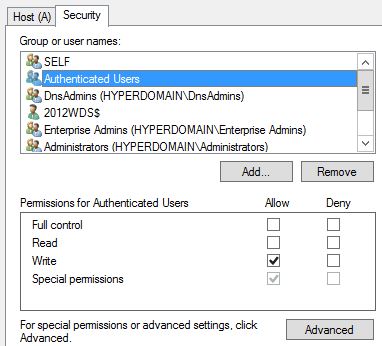
That's why TechNet tells us the entry is not secured. Now the big question is: Why does anybody want to put the DNS Server inside of the DNSUpdateProxy Group to have "insecure" entries in DNS?
Well one scenario in which this - might - be useful would be a DHCP migration scenario outlined in this article: http://technet.microsoft.com/en-us/library/cc787034(v=ws.10).aspx
That's why it's currently unclear to me why to add the servers to the DNSUpdateProxy Group. Why not just use the DHCP credentials without adding the server to the DNSUpdateProxy group? In the lab, this works well.
Saturday, June 1, 2013 11:50 PM
Ace,
Many thanks for your answer. It would still be interesting to know the reason why the DNS Servers need to be added to the DnsUpdateProxy group, since based on my tests in the lab it is not neccessary to put the DHCP Servers into that group.
TechNet says the following about the DnsUpdateProxy group:
"DNS domain names that are registered by the DHCP server are not secure when the DHCP server is a member of the DnsUpdateProxy group."
Why are those entries not secure? Reason is, as soon as the DHCP Server is added to the DnsUpdateProxy, the authenticated users group has write access to that A record (assumed the DHCP Server registes the entry on behalf of the client and DNS Update Credentials is not configured):
That's why TechNet tells us the entry is not secured. Now the big question is: Why does anybody want to put the DNS Server inside of the DNSUpdateProxy Group to have "insecure" entries in DNS?
Well one scenario in which this - might - be useful would be a DHCP migration scenario outlined in this article: http://technet.microsoft.com/en-us/library/cc787034(v=ws.10).aspx
That's why it's currently unclear to me why to add the servers to the DNSUpdateProxy Group. Why not just use the DHCP credentials without adding the server to the DNSUpdateProxy group? In the lab, this works well.
Just to be clear about your quoted sentence in red, and I'm nit sure if that is a misprint on your part:
Just the DHCP servers, NOT THE DNS SERVERS, must be in the DnsUpdateProxy group.
The TechNet article and your assessment are correct about the insecure records. That why you need both. And it's the way the engineers designed the product.
.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Sunday, June 2, 2013 10:41 AM
"It would still be interesting to know the reason why the DNS Servers need to be added to the DnsUpdateProxy Group."
Your are right, that's a misprint on my part. The correct sentence would be
"It would still be interesting to know the reason why the DHCP Servers need to be added to the DnsUpdateProxy Group."
So the original question was this:
I was thinking of configuring DHCP to use a service account to update DNS records. If I set this, do the DHCP Servers need to be members of the DNSUpdateProxy security group for the service account to work?
In my opinion, the correct answer to the question would be this:
No, adding the DHCP Server to be a member of the DNSUpdateProxy security group for the service account to work is not neccessary. Do not add the DCHP Servers to the DnsUpdateProxy Group unless you have a specific reason to do so.
Sunday, June 2, 2013 4:20 PM
In my opinion, the correct answer to the question would be this:
No, adding the DHCP Server to be a member of the DNSUpdateProxy security group for the service account to work is not neccessary. Do not add the DCHP Servers to the DnsUpdateProxy Group unless you have a specific reason to do so.
From my experience having seen issues with some of my own customers, and issues that others have posted in this forum, I disagree. And the Microsoft engineers say you need both. However, if you've found your solution works for you, by all means go with it! :-)
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Sunday, June 2, 2013 9:13 PM
In my opinion, the correct answer to the question would be this:
No, adding the DHCP Server to be a member of the DNSUpdateProxy security group for the service account to work is not neccessary. Do not add the DCHP Servers to the DnsUpdateProxy Group unless you have a specific reason to do so.
From my experience having seen issues with some of my own customers, and issues that others have posted in this forum, I disagree. And the Microsoft engineers say you need both. However, if you've found your solution works for you, by all means go with it! :-)
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/This post is provided AS-IS with no warranties or guarantees and confers no rights.
Yeah will do, I was always some kind of a maverick :-)
Thursday, July 11, 2013 3:10 PM
In my opinion, the correct answer to the question would be this:
No, adding the DHCP Server to be a member of the DNSUpdateProxy security group for the service account to work is not neccessary. Do not add the DCHP Servers to the DnsUpdateProxy Group unless you have a specific reason to do so.
From my experience having seen issues with some of my own customers, and issues that others have posted in this forum, I disagree. And the Microsoft engineers say you need both. However, if you've found your solution works for you, by all means go with it! :-)
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/This post is provided AS-IS with no warranties or guarantees and confers no rights.
Ace
Thanks for your responses and links provided. Was there ever an answer as to why, when using credentials, that the DNSUpdateProxy group membership is necessary? I'm trying to understand how the DNS registration process would differ with or without that group membership when DHCP is configured to use credentials.
Thanks
Thursday, July 11, 2013 3:49 PM
Ace
Thanks for your responses and links provided. Was there ever an answer as to why, when using credentials, that the DNSUpdateProxy group membership is necessary? I'm trying to understand how the DNS registration process would differ with or without that group membership when DHCP is configured to use credentials.
Thanks
I'm not totally sure, but surmising, it has to do with ownership. Remember, I got that requirement from the MSFT engineers.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Thursday, July 11, 2013 7:34 PM
Thanks for the response. I have one other question as well. When configuring DHCP in an existing environment with dozens of scopes and hundreds of reservations, it appears that modifying the DNS dynamic update settings, like "Always dynamically update DNS A and PTR records", on the DHCP server object does not modify those same settings on existing scopes or reservations. To make that change global, does that need to be changed, manually or via script, on every existing scope and reservation?
Thursday, July 11, 2013 8:27 PM
It only applies to new leases. We usually recommend scavenging to cleanup the older records, or go through them manually, or script it using netsh.
More on Scavenging:
This link covers the following:
DHCP Service Configuration, Dynamic DNS Updates, Scavenging, Static Entries, Timestamps, DnsUpdateProxy Group, DHCP Credentials, prevent duplicate DNS records, DHCP has a "pen" icon, and more...
Published by Ace Fekay, MCT, MVP DS on Aug 20, 2009 at 10:36 AM 3758 2
http://msmvps.com/blogs/acefekay/archive/2009/08/20/dhcp-dynamic-dns-updates-scavenging-static-entries-amp-timestamps-and-the-dnsproxyupdate-group.aspx
Good summary (use in blog)
How Dynamic DNS behaves with multiple DHCP servers on the same Domain?
http://social.technet.microsoft.com/Forums/en-US/winserverNIS/thread/e9d13327-ee75-4622-a3c7-459554319a27
Don't be afraid of DNS Scavenging. Just be patient
http://blogs.technet.com/b/networking/archive/2008/03/19/don-t-be-afraid-of-dns-scavenging-just-be-patient.aspx
Optimizing your network to keep your DNS squeaky clean
http://blogs.technet.com/b/networking/archive/2009/02/09/optimizing-your-network-to-keep-your-dns-squeaky-clean.aspx
Good article by Sean Ivey, MSFT:
How DNS Scavenging and the DHCP Lease Duration Relate
(Make the NoRefresh and Refresh each half the lease, so combined, they are equal or greater than the lease).
http://blogs.technet.com/b/askpfe/archive/2011/06/03/how-dns-scavenging-and-the-dhcp-lease-duration-relate.aspx
-
I haven't scripted anything for DHCP yet. Maybe the following NetSH command references will help:
HOWTO: Import and Export DHCP reservations in server 2003 (netsh)
http://koolbeans.wordpress.com/2007/07/31/howto-import-and-export-dhcp-reservations-in-server-2003/
Netsh commands for DHCP
http://technet.microsoft.com/en-us/library/cc787375(WS.10).aspx
More Netsh commands for DHCP
http://technet.microsoft.com/en-us/library/bb490941.aspx
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Thursday, July 18, 2013 11:30 AM
In my opinion, the correct answer to the question would be this:
No, adding the DHCP Server to be a member of the DNSUpdateProxy security group for the service account to work is not neccessary. Do not add the DCHP Servers to the DnsUpdateProxy Group unless you have a specific reason to do so.
From my experience having seen issues with some of my own customers, and issues that others have posted in this forum, I disagree. And the Microsoft engineers say you need both. However, if you've found your solution works for you, by all means go with it! :-)
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/This post is provided AS-IS with no warranties or guarantees and confers no rights.
Ace
Thanks for your responses and links provided. Was there ever an answer as to why, when using credentials, that the DNSUpdateProxy group membership is necessary? I'm trying to understand how the DNS registration process would differ with or without that group membership when DHCP is configured to use credentials.
Thanks
There is no reason to do that. Sorry Ace, no offence mate, but you are wrong regarding this matter and the initial question is answered incorrectly in this thread.
The real answer is, when updates using DHCP credentials, you should not add the DHCP Server to the DNSUpdateProxy Group unless you have a specific reason to do so.
In fact it is easy to reproduce: Just set up a lab and use DHCP Credentials, and don't add the DHCP Server to the DNSUpdateProxy Group. You will see that it works without any issues. I also use this set-up in production environments and it works well.
Thursday, July 18, 2013 4:08 PM
I have my environment setup as stated, with DHCP servers in proxy group and using DNS Credentials. The issue I am running into is that my users move around to different offices with non windows DHCP servers and the actual clients are unable to update their records since their outdated records are owned by the DHCP user account.
Has anyone else seen this or have an idea on how to get around it?
Thursday, July 18, 2013 6:23 PM
Unfortunately in that scenario, you must manually keep track of the records. If you can use all Windows DHCP servers, and configure them with the same DHCP credentials and add them to the DnsUpdateProxy group, they will all work together.
I assume you have enabled scavenging? That will help partially. Links on this were provided in post above yours.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Monday, January 6, 2014 8:45 PM
Sorry to resurrect an old thread.... but I have to ask:
Does enabling secure only updates matter (or work) in conjunction with forcing DHCP to update all records AND having credentials configured for DNS dynamic updates registration credentials with a user that is a member of DNSUpdateProxy group?
Secure only should only allow machines that are members of the domain update DNS, but if we are forcing all clients to be registered via DHCP credentials - wouldn't they all work? Or am I misunderstanding something?
Monday, January 6, 2014 9:14 PM
Just in response to my own question... please correct me if I am wrong:
by setting secure only updates, only machine that are a member of the domain can update DNS AND machines must adhere to the ACL list for updating DNS records - meaning server and static records will also be better protected
If we force DHCP to update DNS records and we have the credentials set, this nulls the first line above (machines not on the domain will be able to register in DNS via DHCP credentials)
Tuesday, January 7, 2014 7:07 AM
Sorry to resurrect an old thread.... but I have to ask:
Does enabling secure only updates matter (or work) in conjunction with forcing DHCP to update all records AND having credentials configured for DNS dynamic updates registration credentials with a user that is a member of DNSUpdateProxy group?
Secure only should only allow machines that are members of the domain update DNS, but if we are forcing all clients to be registered via DHCP credentials - wouldn't they all work? Or am I misunderstanding something?
No, do NOT put the credential accounts in that group. The only thing that goes in it are the DHCP server computer objects, nothing else.
Here's a summary I've accumulated over time that may help:
===
In summary:
- Configure DHCP Credentials. The credentials only need to be a plain-Jane, non-administrator, user account. But give it a really strong password.
- Set DHCP to update everything, whether the clients can or cannot.
- Set the zone for Secure & Unsecure Updates. Do not leave it Unsecure Only.
- Add the DHCP server(s) to the Active Directory, Built-In DnsUpdateProxy security group.
- Make sure ALL other non-DHCP servers are NOT in the DnsUpdateProxy group.
- For example, some believe that the DNS servers or other DCs not running DHCP should be in it. They must be removed or it won't work.
- Make sure that NO user accounts are in that group, either. (I hope that's crystal clear - you would be surprised how many will respond asking if the DHCP credentials should be in this group.)
- On Windows 2008 R2 or newer, DISABLE Name Protection.
- If DHCP is co-located on a Windows 2008 R2 or Windows 2012 DC, you can and must secure the DnsUpdateProxy group by running the following:
dnscmd /config /OpenAclOnProxyUpdates 0 - Configure Scavenging on ONLY one DNS server. What it scavenges will replicate to others anyway.
- Set the scavenging NOREFRESH and REFRESH values combined to be equal or greater than the DHCP Lease length.
*
Here are a couple of good discussions on it since you've last posted:
How Dynamic DNS behaves with multiple DHCP servers on the same Domain?
http://social.technet.microsoft.com/Forums/en-US/winserverNIS/thread/e9d13327-ee75-4622-a3c7-459554319a27
Thread: "DNS problem" December 18, 2013
http://social.technet.microsoft.com/Forums/windowsserver/en-US/37b8b6b3-6cb1-496c-8492-09ded13bab18/dns-problem?forum=winserverNIS
*
Cheers!
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Tuesday, January 7, 2014 7:08 AM
Just in response to my own question... please correct me if I am wrong:
by setting secure only updates, only machine that are a member of the domain can update DNS AND machines must adhere to the ACL list for updating DNS records - meaning server and static records will also be better protected
If we force DHCP to update DNS records and we have the credentials set, this nulls the first line above (machines not on the domain will be able to register in DNS via DHCP credentials)
If you force DHCP, it will update everything. Make sure Option 015 is set to your AD domain name so it can update into that zone for machines that are not joined, including Apple devices, Linux, Unix, phones, tablets, Smart TVs, XBOX, etc, etc.
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/
This post is provided AS-IS with no warranties or guarantees and confers no rights.
Tuesday, January 7, 2014 1:29 PM
Ace, I very much appreciate your quick response!
It looks as though I confused myself... currently, my DHCP is on a DC and I thought I read not to add DCs to the DNSUpdateProxy group. Please see my responses below to your checklist:
- Configure DHCP Credentials. The credentials only need to be a plain-Jane, non-administrator, user account. But give it a really strong password.
- ^DHCP credentials are configured and plain-Jane with the exception of it being a member of DNSUpdateProxy. Sounds like I need to remove this user from the DNSUpdateProxy group and add my DHCP server (which is also a DC)
- Set DHCP to update everything, whether the clients can or cannot.
- ^This I plan on doing soon
- Set the zone for Secure & Unsecure Updates. Do not leave it Unsecure Only.
- ^Currently, we are set for unsecure and secure. We want to change it to secure only.
- Add the DHCP server(s) to the Active Directory, Built-In DnsUpdateProxy security group.
- Make sure ALL other non-DHCP servers are NOT in the DnsUpdateProxy group.
- For example, some believe that the DNS servers or other DCs not running DHCP should be in it. They must be removed or it won't work.
- Make sure that NO user accounts are in that group, either. (I hope that's crystal clear - you would be surprised how many will respond asking if the DHCP credentials should be in this group.)
- ^I need to add my DHCP server to this group and run the command below since it is a DC. *Also* - we plan on later moving DHCP to a non-DC server. Should I go ahead and add that server to the proxy group as well?
- On Windows 2008 R2 or newer, DISABLE Name Protection.
- ^currently disabled
- If DHCP is co-located on a Windows 2008 R2 or Windows 2012 DC, you can and must secure the DnsUpdateProxy group by running the following:
dnscmd /config /OpenAclOnProxyUpdates 0 - ^I need to run this. I assume it is ran via command line on the DC. Once we move DHCP, do we need to run any other commands?
- Configure Scavenging on ONLY one DNS server. What it scavenges will replicate to others anyway.
- ^this was just turned on and is only on one DNS server.
- Set the scavenging NOREFRESH and REFRESH values combined to be equal or greater than the DHCP Lease length.
- ^Done
And to comment on your other reply, we do have option 015 set to our domain name.
Tuesday, January 7, 2014 1:39 PM
oh and a follow-up question on bullet item #2:
- Set DHCP to update everything, whether the clients can or cannot.
- ^This I plan on doing soon
Does it matter if the clients can update DNS? Or should we work with the desktop team to disable DDNS on the client-side?
I was originally going to just leave ddns enabled client-side but then I came across this post and it steered me in the other direction....

Thursday, February 27, 2014 8:53 PM | 1 vote
I have to agree with John here. I don't think it's reasonable to just say 'ms told us so'. We need a technical before and answer is given. I have multiple DHCP servers and I use a security account on them to register the records and never use the DNSUpdateProxy Group and I have no problems. My thinking is this:
Assume we are using Integrated Secure Zones in AD:
Scenario 1:
- Windows DHCP server i registering records on behalf of clients
- Not a member of DNSUpdateProxy Group and not using dedicated account
- Records will have owner as *dhcpserver$ *and only that account can update
- This is a problem if that DHCP server fails
- Also, non Windows DHCP server with no AD account cannot update
Scenario 2:
- Windows DHCP server i registering records on behalf of clients
- Member of *DNSUpdateProxy Group *and not using dedicated account
- Records will have owner as *SYSTEM *and authenticated users can updated meaning any user or client on that domain
- No problem if that DHCP server fails as any other authorized DHCP server can update
- Non Windows DHCP servers can updated if they have a domain machine account
Scenario 3:
- Windows DHCP server i registering records on behalf of clients
- Using a dedicated account
- Records added with owner same as this dedicated account
- Another DHCP server that also uses this same account can updated the records
- A non windows DHCP server that can use this account can also update the records
Now, can someone from MS please clarify the technical reason they say that in Scenario 3, you must add the DHCP servers to the DNSUpdateProxy group ?
http://technet.microsoft.com/en-us/library/cc780538(v=ws.10).aspx
Saturday, March 1, 2014 5:40 PM | 1 vote
In my opinion, the correct answer to the question would be this:
No, adding the DHCP Server to be a member of the DNSUpdateProxy security group for the service account to work is not neccessary. Do not add the DCHP Servers to the DnsUpdateProxy Group unless you have a specific reason to do so.
From my experience having seen issues with some of my own customers, and issues that others have posted in this forum, I disagree. And the Microsoft engineers say you need both. However, if you've found your solution works for you, by all means go with it! :-)
Ace Fekay
MVP, MCT, MCITP/EA, MCTS Windows 2008/R2 & Exchange 2007, Exchange 2010 EA, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Technical Blogs & Videos: http://www.delawarecountycomputerconsulting.com/This post is provided AS-IS with no warranties or guarantees and confers no rights.
>>> Ace
>>> Thanks for your responses and links provided. Was there ever an answer as to why, when using credentials, that the DNSUpdateProxy group membership is necessary? I'm trying to understand how the DNS registration process would differ with or without that group membership when DHCP is configured to use credentials.
>>> Thanks
>>> There is no reason to do that. Sorry Ace, no offence mate, but you are wrong regarding this matter and the initial question is answered incorrectly in this thread.
>>> The real answer is, when updates using DHCP credentials, you should not add the DHCP Server to the DNSUpdateProxy Group unless you have a specific reason to do so.
>>> In fact it is easy to reproduce: Just set up a lab and use DHCP Credentials, and don't add the DHCP Server to the DNSUpdateProxy Group. You will see that it works without any issues. I also use this set-up in production environments and it works well.
The DnsUpdateProxy group, along with configuring credentials, has to do with records ownership to eliminate duplicates. If you're not concerned with this part, then sure, DHCP-DNS registration works FINE without adding the DHCP server to the group.
Sorry if I was not clear about that.
Ace Fekay
MVP, MCT, MCSE 2012, MCITP EA & MCTS Windows 2008/R2, Exchange 2013, 2010 EA & 2007, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This posting is provided AS-IS with no warranties or guarantees and confers no rights.
Saturday, March 1, 2014 5:50 PM
I have to agree with John here. I don't think it's reasonable to just say 'ms told us so'. We need a technical before and answer is given. I have multiple DHCP servers and I use a security account on them to register the records and never use the DNSUpdateProxy Group and I have no problems. My thinking is this:
Assume we are using Integrated Secure Zones in AD:
Scenario 1:
- Windows DHCP server i registering records on behalf of clients
- Not a member of DNSUpdateProxy Group and not using dedicated account
- Records will have owner as *dhcpserver$ *and only that account can update
- This is a problem if that DHCP server fails
- Also, non Windows DHCP server with no AD account cannot update
Scenario 2:
- Windows DHCP server i registering records on behalf of clients
- Member of *DNSUpdateProxy Group *and not using dedicated account
- Records will have owner as *SYSTEM *and authenticated users can updated meaning any user or client on that domain
- No problem if that DHCP server fails as any other authorized DHCP server can update
- Non Windows DHCP servers can updated if they have a domain machine account
Scenario 3:
- Windows DHCP server i registering records on behalf of clients
- Using a dedicated account
- Records added with owner same as this dedicated account
- Another DHCP server that also uses this same account can updated the records
- A non windows DHCP server that can use this account can also update the records
Now, can someone from MS please clarify the technical reason they say that in Scenario 3, you must add the DHCP servers to the DNSUpdateProxy group ?
http://technet.microsoft.com/en-us/library/cc780538(v=ws.10).aspx
I guess this link didn't help?
DNS Record Ownership and the DnsUpdateProxy Group
"... to protect against unsecured records or to permit members of the DnsUpdateProxy group to register records in zones that allow only secured dynamic updates, you must create a dedicated user account and configure DHCP servers to perform DNS dynamic updates with the credentials of this account (user name, password, and domain). Multiple DHCP servers can use the credentials of one dedicated user account."
http://technet.microsoft.com/en-us/library/dd334715(WS.10).aspx
-
Just to add:
Why is the DnsUpdateProxy group needed in conjunction with credentials?
The technical reason is twofold:
DnsUpdateProxy:
Objects created by members of the DNSUpdateProxy group have no security; therefore, any authenticated user can take ownership of the objects.
DHCP Credentials:
Forces ownership to the account used in the credentials, which the DnsUpdateProxy group allowed to take ownership other than the registering client.
Otherwise, the default process is outlined below, and this applies to non-Microsoft operating systems, too, but please note that non-Microsoft operating systems can't use Kerberos to authenticate to dynbamically update into a Secure Only zone, however you can configure Windows DHCP to do that for you.
1. By default, Windows 2000 and newer statically configured machines will
register their own A record (hostname) and PTR (reverse entry) into DNS.
2. If set to DHCP, a Windows 2000, 2003 or XP machine, will request DHCP to allow
the machine itself to register its own A (forward entry) record, but DHCP will register its PTR
(reverse entry) record.
3. If Windows 2008/Vista, or newer, the DHCP server always registers and updates client information in DNS.
Note: "This is a modified configuration supported for DHCP servers
running Windows Server 2008 and DHCP clients. In this mode,
the DHCP server always performs updates of the client's FQDN,
leased IP address information, and both its host (A) and
pointer (PTR) resource records, regardless of whether the
client has requested to perform its own updates."
Quoted from, and more info on this, see:
http://technet.microsoft.com/en-us/library/dd145315(v=WS.10).aspx
4. The entity that registers the record in DNS, owns the record.
Note "With secure dynamic update, only the computers and users you specify
in an ACL can create or modify dnsNode objects within the zone.
By default, the ACL gives Create permission to all members of the
Authenticated User group, the group of all authenticated computers
and users in an Active Directory forest. This means that any
authenticated user or computer can create a new object in the zone.
Also by default, the creator owns the new object and is given full control of it."
Quoted from, and more info on this:
http://technet.microsoft.com/en-us/library/cc961412.aspx
More on this discussed in:
http://social.technet.microsoft.com/Forums/windowsserver/en-US/6f5b82cf-48df-495e-b628-6b1a9a0876ba/regular-domain-user-uses-rsat-to-create-dns-records?forum=winserverNIS
-
If that doesn't help, I highly suggest to contact Microsoft Support to get a definitive response. If you do, I would be highly curious what they say if it's any different than what I found out from the product group (mentioned earlier in this thread).
And of course, if you can update what you find out, it will surely benefit others reading this thread that have the same question!
Thank you!
Ace Fekay
MVP, MCT, MCSE 2012, MCITP EA & MCTS Windows 2008/R2, Exchange 2013, 2010 EA & 2007, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This posting is provided AS-IS with no warranties or guarantees and confers no rights.
Sunday, March 2, 2014 4:21 PM
Thanks Ace, and apologies If I sounded curt (which was not intentional and you are a huge contributor of valuable info here!) but posting from smart phones has a habit of making me do that ;)
In terms of the following remark:
Why is the DnsUpdateProxy group needed in conjunction with credentials?
The technical reason is twofold:
DnsUpdateProxy:
Objects created by members of the DNSUpdateProxy group have no security; therefore, any authenticated user can take ownership of the objects.
- Agreed. Basically, we have unsecured records.
DHCP Credentials:
Forces ownership to the account used in the credentials, which the DnsUpdateProxy group allowed to take ownership other than the registering client.
- Again, but why use both? Are you saying that when specifying credentials, it allows the DHCP server using the credentials and another DHPC not using credentials but a member of the DNSUpdateProxy group to modify the records?
Tuesday, March 4, 2014 3:10 AM
Thanks Ace, and apologies If I sounded curt (which was not intentional and you are a huge contributor of valuable info here!) but posting from smart phones has a habit of making me do that ;)
In terms of the following remark:
Why is the DnsUpdateProxy group needed in conjunction with credentials?
The technical reason is twofold:
DnsUpdateProxy:
Objects created by members of the DNSUpdateProxy group have no security; therefore, any authenticated user can take ownership of the objects.- Agreed. Basically, we have unsecured records.
DHCP Credentials:
Forces ownership to the account used in the credentials, which the DnsUpdateProxy group allowed to take ownership other than the registering client.- Again, but why use both? Are you saying that when specifying credentials, it allows the DHCP server using the credentials and another DHPC not using credentials but a member of the DNSUpdateProxy group to modify the records?
No problem, I didn't think you were curt, just upset that you don't have a definitive and black and white answer other than the TechNet articles I've posted explaining it.
Again, a call to Microsoft may be your better bet. And I hope you can post their response, if you could.
Cheers!
Ace Fekay
MVP, MCT, MCSE 2012, MCITP EA & MCTS Windows 2008/R2, Exchange 2013, 2010 EA & 2007, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This posting is provided AS-IS with no warranties or guarantees and confers no rights.
Friday, July 11, 2014 12:03 PM
Hello,
I have DHCP servers on 2003 and 2008 r2 on different side installed on DCs.
After an ADRAS a server 2003 , this issue is notified :
(Event ID 1056, DHCP, DHCP Running on a DC with Default Credentials)
I saw that we didn't need to add the servers the DnsUpdateProxy group beacause giving to much rights on DCs
I would like to know if it's necessary to configure a service account to register dynamically dns records.
aND I didn't understand why they gave us only a server2003
For me it's not necessary but if it is can you confirm to me , do i need to configure a service account ?
Maybe if somebody hack the server to register dns record ?
Sunday, July 13, 2014 10:16 PM
Hello,
I have DHCP servers on 2003 and 2008 r2 on different side installed on DCs.
After an ADRAS a server 2003 , this issue is notified :
(Event ID 1056, DHCP, DHCP Running on a DC with Default Credentials)
I saw that we didn't need to add the servers the DnsUpdateProxy group beacause giving to much rights on DCs
I would like to know if it's necessary to configure a service account to register dynamically dns records.
aND I didn't understand why they gave us only a server2003
For me it's not necessary but if it is can you confirm to me , do i need to configure a service account ?
Maybe if somebody hack the server to register dns record ?
I can't answer the question as to why you got a 2003 server for this role other than probably your company hasn't yet tested any newer operating system.
As for the DnsUpdateProxy group and creating credentials, they are both needed in order for DHCP to "own" the records it registers into DNS.
The implications are if you don't add it, you may wind up with duplicate records for DHCP clients in the DNS Forward and Reverse zones.
You don't have to add it, if you feel it's a security concern. That's up to you. But both are required to make this work, along with the configuration I posted above.
Ace Fekay
MVP, MCT, MCSE 2012, MCITP EA & MCTS Windows 2008/R2, Exchange 2013, 2010 EA & 2007, MCSE & MCSA 2003/2000, MCSA Messaging 2003
Microsoft Certified Trainer
Microsoft MVP - Directory Services
Complete List of Technical Blogs: http://www.delawarecountycomputerconsulting.com/technicalblogs.php
This posting is provided AS-IS with no warranties or guarantees and confers no rights.
Wednesday, September 2, 2015 6:39 PM | 1 vote
DHCP Credentials:
Forces ownership to the account used in the credentials, which the DnsUpdateProxy group allowed to take ownership other than the registering client.
- Again, but why use both? Are you saying that when specifying credentials, it allows the DHCP server using the credentials and another DHPC not using credentials but a member of the DNSUpdateProxy group to modify the records?
There's a ton of misinformation about this topic throughout the forums and Microsoft's own documentation, so I'll do what I can to clear it up:
There's no reason to put the DHCP Server's computer account in the DnsUpdateProxy group if you're using a service account to do your dynamic updates, full stop.
There's a Microsoft DNS Service property named "OpenACLOnProxyUpdates" and when that property's value is set to 1 (which is the default), then the DNS Service applies a very permissive ACL to any records created or updated by a member of that group, one that allows any authenticated user to take ownership of and modify the record. If the OpenACLOnProxyUpdates property is set to 0 on any given DNS server, then the DnsUpdateProxy group membership check isn't performed at all, and the permissive ACL is never applied to records registered through that server. Note that this is a relatively new configurable property (2008 R2 and newer); prior to its introduction, MS DNS servers just always behaved as if the property was set to 1.
As you may have deduced, when you configure a DHCP server to use a service account to perform dynamic registrations, the server's computer account isn't used to authenticate the registration request to the DNS server, so there's no point whatsoever to adding that computer account to the DnsUpdateProxy group. If you want the dynamic records created by your DHCP service to be created with permissive ("unsecured") ACLs, then you should add the service account to the DnsUpdateProxy group, not the DHCP server's computer account. However, if you only ever want your DHCP servers updating those dynamic records, then set the options on the "DNS" tab of the "IPv4" or zone object accordingly, and don't put anything in the DnsUpdateProxy group.
Finally, note that if you want your DHCP service account for DNS registration to be able to alter existing DNS records, you would need to make the service account a member of the DnsAdmins, Domain Admins, or Enterprise Admins groups, even if you put the service account in the DnsUpdateProxy group, because membership in this group does not allow a group member to bypass the existing ACL on a record. The group member still initially needs write access to the record before the DNS server will wipe out its ACL. I do not recommend that anyone do this, by the way, but if you wanted this functionality, that's the only way to do it. Which, frankly, is annoying; Microsoft should introduce some other way to permit this, so that domain member PCs and DHCP servers can both modify dynamic client records.