Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Sunday, March 25, 2018 9:14 AM
Guys, I am facing this issues recently, Whenever I enable the AES128_HMAC_SHA1 encryption method for kerberos in gpedit**(path)**, We are not able to change the local user password via crtl+alt+del screen options.
Also sure that I am trying to change the password of the local user, But the password can still be changed via computer management settings and user accounts options in control panel.
Why not on crtl+alt+del screen -> "Change a password" ?
(Path) = computer configuration -> Windows settings -> Security settings -> local policies -> Security options -> Network security: Configure encryption types allowed for Kerberos : AES128_HMAC_SHA1
But if I unchecked the option in gpedit, I am able to reset the password in the same screen.
Also tried rebooting the machine and executing the "gpupdate /force " command after the change , Its not working. It happens in all windows 10 machines (Checked in multiple machines)
Is this a bug in windows 10 or Am i missing anything ?
I have shared the images of the error and the images where i can reset the password after unchecking the encryption method.
Before enabling AES128_HMAC_SHA1:
**After Enabled AES128_HMAC_SHA1: **
Please note : I need to enable that encryption method so that the users in my domain can authenticate from the desktop, Please suggest any possible solution.
Kindly help regarding this, Thanks in advance !!
All replies (9)
Sunday, March 25, 2018 4:10 PM
By enabling AES128_HMAC_SHA1 and not selecting the others that disables them. From the Explain tab in Group Policy;
"If not selected, the encryption type will not be allowed. This setting may affect compatibility with client computers or services and applications. Multiple selections are permitted."
Related post for info.
Why did Enabling AES128_HMAC_SHA1 Break Kerberos
Sunday, March 25, 2018 4:31 PM
Thanks for the suggestion, i already went through that post. But the user I am trying to reset the password is a local user and the machine itself is not linked to domain.
In future we may link that machine to domain.
I am not sure, How kerberos is linked with local accounts and why enabling AES128_HMAC_SHA1 causes password reset issue with local account.
Sunday, March 25, 2018 7:00 PM
A bit of trial and error shows local password changes need AES256_HMAC_SHA1 (so select both). Not sure why Kerberos is required for local passwords, that's a question of Windows internals not an expert in that. Searching Kerberos local passwords changes brings back links for Linux which is interesting perhaps.
Monday, March 26, 2018 7:01 AM | 2 votes
Actually it is not a bug!
From my test,only when you enable the AES 256, then you can change the local user password using CTRL+ALT+DELETE. It is because when you enter CTRL+ALT+DELETE, you have to type Old password-new password-confirm password, system will authenticate the old password using kerberos AES 256. So if you change it to AES128, then the authenticate process failed.
You may confused that why you can change password via computer management settings. It is because that it is different from changing password via CTRL+ALT+DELETE. You don't have to type old password, you directly type the new password instead. So in this way, kerberos is not necessary.
Let me make a summary: any methods if it is required old password to change the local account password, then it needs Kerbose AES 256 to authenticate. From my test, I want to change password from Control Panel>user accounts>change password, which need to enter old password, then failed.
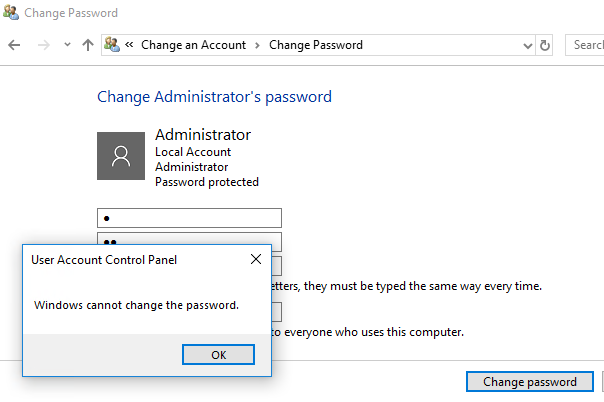
So as a result, if you want to both enable AES 128 and let change local user password via CTRL+ALT+DELETE, it is suggested that you can enable both AES128 and AES 256.


Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Monday, March 26, 2018 7:33 AM
This really helped me !! Thanks for the effort taken. +1
I would like to refer the documents related to this. let me know if you went through any documents
Monday, March 26, 2018 9:09 AM
I test without referring to documents.
As I know, the DES encryption type is not supported since Windows xp. So from windows 7 and later versions, DES encryption type is not recommended to choose. And if you choose one encryption, it means that other encryption types will be disabled.
As to AES encryption type, the 256 bit is more security than 128 bit. So windows may choose an more security method to authenticate.
Anyway, thanks for your time.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Tuesday, March 27, 2018 5:31 PM
I have one more question, Why local account uses kerberos to authenticate ?
Because the policy i am editing is to enable encryption method is for domain controller.
Is there any way to force the host machine to use AES 128 for local user ?
Answers for the above will be lot helpful.
Thanks in advance
Wednesday, March 28, 2018 1:28 AM
Generally, Kerberos is used to authenticate domain account and NTLM is used to authenticate local account.
After I discussed the issue with my colleagues, she explained that it may be a common policy that can be used both on domain and local account.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Thursday, March 29, 2018 7:58 AM
Hi,
Any further problems?
It is appreciated that you can mark it as an answer if the suggestion did any help on the issue.
Thanks
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].