Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Monday, June 10, 2019 6:00 PM
Hi there,
I would to achieve centralized wireless authentication from several small offices NOT directly connected to the company's network.
In other words there are NOT mpls or vpn connections, thus internal NPS servers cannot be reached directly from branch offices.
I'm wondering if using NPS proxies published over Internet is a good idea or not ...
Can I secure enough the traffic using PEAP on internal NPS servers or still some sensitive parts of Radius packets are sent in clear text ?
Thank you
Riccardo
All replies (8)
Friday, June 14, 2019 8:38 AM ✅Answered
Hi,
Yes, you are right.
Since we use EAP or PEAP authentication, the user password is absolutely secure even on the Internet.
However, some attributes are sent in clear text, so you can consider it is not confidential enough.
Best regards,
Travis
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Tuesday, June 11, 2019 3:28 AM
Hi,
In general, a NPS proxy server is located in another domain and there is a secure connection between two stations such as VPN.
In your scenario, there is no secure connection but NPS server supports shared secret authentication.

Best regards,
Travis
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Tuesday, June 11, 2019 4:22 PM
Hi Travis,
thank you for your reply.
Of course, shared secret authentication is already in place between:
- the Wi-Fi access point at branch office and the Radius proxy (a NPS stand-alone server in DMZ)
- the Radius proxy in the DMZ and the authenticating Radius (NPS role installed on a Domain Controller).
To my knowledge some portions of Radius traffic are always sent in "clear text" even though "PEAP + certificate" is used. This causes some sensitive attributes (like the username...) to be sent in "clear text".
I did some traces and a "man in middle" can actually read this information sniffing the traffic between access point and Radius proxy.
Below you can find a picture depicting my scenario (slightly simplified): the red arrow represents the traffic I'm worrying about.
Is there a way to circumvent this issue ?
Any idea or suggestion will be appreciated.
Thank you
Riccardo
Wednesday, June 12, 2019 8:30 AM
Hi,
Thanks for your details.
Radius server is used for intranet, so it is not safe enough on the Internet.
Yes, you are right. Before PEAP tunnel is established, the username will be sent in "clear text" using EAP.
I am afraid that there is no better way unless you establish a secure tunnel between the branch office and the DMZ.
Best regards,
Travis
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Wednesday, June 12, 2019 6:17 PM
Hi Travis,
thank you for your reply.
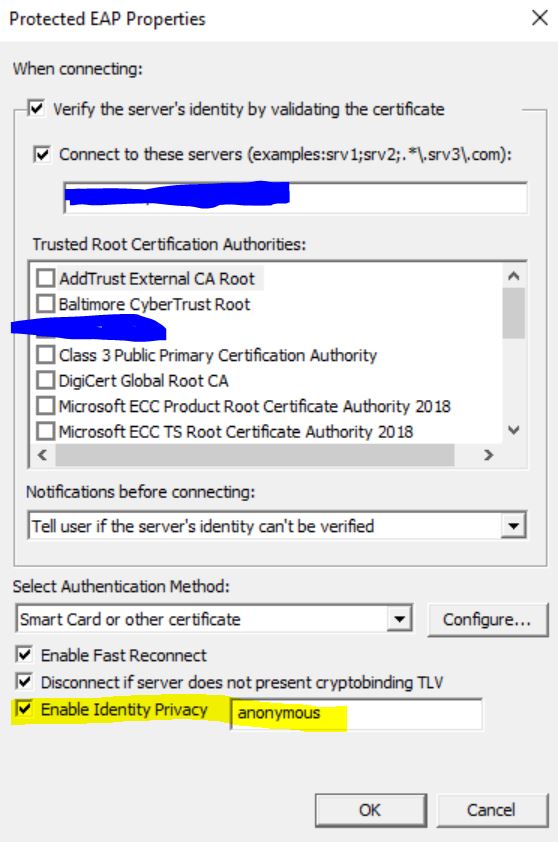
I have some news: I investigated further and tested the option "Identity Privacy". Added to proper configuration at NPS level it prevents from sending the username in clear text. Other attributes (NAS identifier, wireless SSID, NAS IP address, etc) are still sent in clear but I believe this may be acceptable for the customer.
You says "Radius server is used for intranet, so it is not safe enough on the Internet", so my question is:
are there other weaknesses I'm missing or using PEAP + Identity Privacy isn't enough to consider Radius protocol secure over Internet ?
Thanks
Riccardo
Thursday, June 13, 2019 9:21 AM
Hi,
Thanks for your sharing.
Don't worry, all application data is encrypted after the EAP-TLS handshake is completed.
You can check traffic packages.
Best regards,
Travis
Please remember to mark the replies as an answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected]
Thursday, June 13, 2019 10:09 PM
Thank you, Travis.
So to recap:
usually the reason why Radius protocol isn't considered secure over Internet is due the fact that some attributes (NAS identifier, wireless SSID, NAS IP address, etc.) are always sent in clear text. Nevertheless if, after appropriate assessment, anyone considers this information not confidential, then Radius protocol might be considered secure enough even over the Internet.
Is this statement correct ?
Thank you for your definitive answer.
Riccardo
Friday, June 14, 2019 9:19 AM
Thank you so much !
Best Regards
Riccardo