Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Tuesday, July 26, 2016 1:45 PM
My question is pretty simple, I've added a PowerShell script to the GPO Logon Scripts (PowerShell tab). Should I have a rule changing the ExecutionPolicy or Logon Scripts runs regardless of the local PowerShell ExecutionPolicy?
Thanks in advance.
All replies (6)
Tuesday, July 26, 2016 7:42 PM ✅Answered | 1 vote
Hi Tal,
you should sign your logon scripts so they run even with execution policy enabled. Basically you need a codesigning certificate (if you have a local PKI in your AD it can issue you one) and sign the script file. Some editors - for example Sapien's PowerShell Studio - provide an auto-sign feature to take the pain out of this process, once the certificate is available.
Other than this, yes, you need to modify execution policy if you roll out unsigned PowerShell scripts via GP.
Cheers,
Fred
There's no place like 127.0.0.1
Wednesday, July 27, 2016 6:14 AM ✅Answered
As Fred said, signing your script is probably the best option. One can also set the executionpolicy for all scripts. But there may be a third option. If you can get your GPO to run the script with the following syntax: "Powershell.exe <path>\script>.ps1", you can add the -ExecutionPolicy Bypass statement (Powershell.exe -ExecutionPolicy Bypass <path>\script>.ps1) and run just this one script unrestricted while maintaining the execution policy.
It should definitely be possible with running a batch script that in turn starts the Powershell script, but that's a somewhat inconvenient way.
Wednesday, July 27, 2016 4:03 AM
Hi Tal,
>>Should I have a rule changing the ExecutionPolicy or Logon Scripts runs regardless of the local PowerShell ExecutionPolicy?
From my humble opinion, if you trust the script, you could enabled the related switch on GPO, if not, a signed scripts is needed and you need to use certificates.
In addition, I suppose we could also consider using GPO to achieve this purpose:
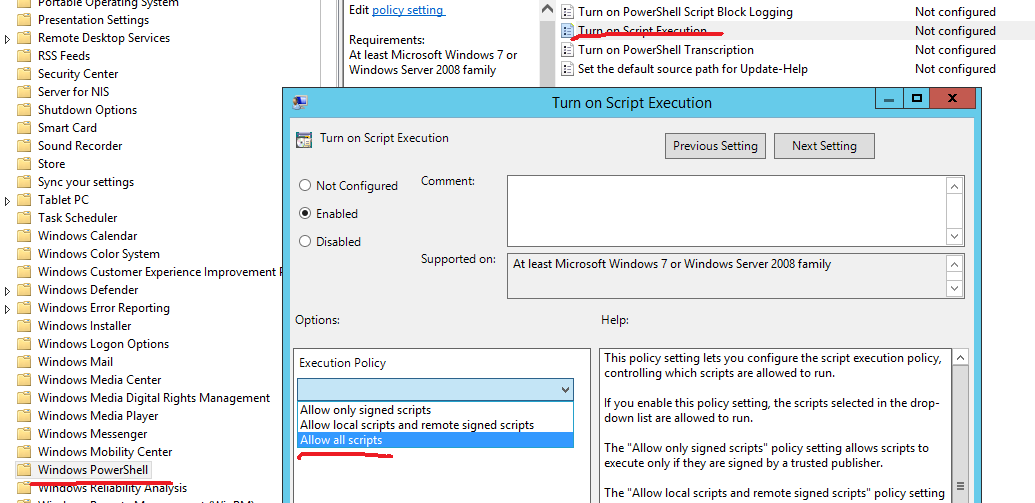
Location:Domain gpo\computer configuration\administrative templates\windows components\windows powershell\turn on script execution
More information about signed script:
Best regards,
Andy_Pan
Wednesday, July 27, 2016 6:43 AM
[...]From my humble opinion, if you trust the script, you could enabled the related switch on GPO, [...]
Hi Andy,
no offense, but that's some dangerous advice. Translated that's "If you trust this one script to do well, allow all scripts". Mind you, execution policy is not much of a security feature, but it's the argument here that's dangerous.
Cheers,
Fred
There's no place like 127.0.0.1
Wednesday, July 27, 2016 6:57 AM
Hi FWN,
>>Mind you, execution policy is not much of a security feature, but it's the argument here that's dangerous
I'm agree with you,Fred.
I assume OP wanted to test this issue on non-production machines.
If it is production environment, I'm also recommend using signed certificates. It's more safer but a little complicated.
Best regards,
Andy_Pan
Wednesday, July 27, 2016 12:08 PM
As Fred said, signing your script is probably the best option. One can also set the executionpolicy for all scripts. But there may be a third option. If you can get your GPO to run the script with the following syntax: "Powershell.exe <path>\script>.ps1", you can add the -ExecutionPolicy Bypass statement (Powershell.exe -ExecutionPolicy Bypass <path>\script>.ps1) and run just this one script unrestricted while maintaining the execution policy.
It should definitely be possible with running a batch script that in turn starts the Powershell script, but that's a somewhat inconvenient way.
FYI
This is also a bad solution and cannot be used in a GPO without using a batch file. This subverts any ability at applying basic security. It is also unnecessary.
\(ツ)_/