Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Thursday, December 22, 2016 12:25 AM
I have installed Windows server 2016 for my domain and configured DNSSEC for this domain, when i DIG to the server I get an un validated response (not RRSIG's are returned) this also occurs when using it to resolve other domains that are signed correctly eg.
dig isc.org @myserver | returns A record
dig isc.org @8.8.4.4 | returns A record & RRSIG
I tried
un-signing and resigning the zone.
uninstalling and reinstalling the role.
I have reconfigured the zone and the same happens...
I saw a similar problem arose in windows server 2012 and the following hot fix was released:
https://support.microsoft.com/en-gb/kb/3051472
I'll try reinstalling the server next but I doubt its any change i've made.
Michael Booth
All replies (7)
Thursday, December 22, 2016 9:06 AM
Hi MichaelBooth,
>>dig isc.org @myserver | returns A record
Have you tried to run nslookup isc.org to resolve address? Could you please provide details information of result to here for further troubleshooting?
Here is information about verify zone signing for your reference:
Procedure: Verify Zone Signing
https://technet.microsoft.com/en-us/library/dn593691(v=ws.11).aspx
Windows server 2016 is new system and you could keep noticing on official update for this issues.
Best Regards
John
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Thursday, December 22, 2016 3:17 PM
Hi John,
Thanks for you reply, ISC is a domain (not mine) that returns RRSIG records,
I did a test by creating a new Zone contoso.com (I don't want to put the actual domain online) and running a dig to the DNS Server.

It can be seen in DNS Manager and shows as signed
however a DIG including DNSSEC does not return RRSIG
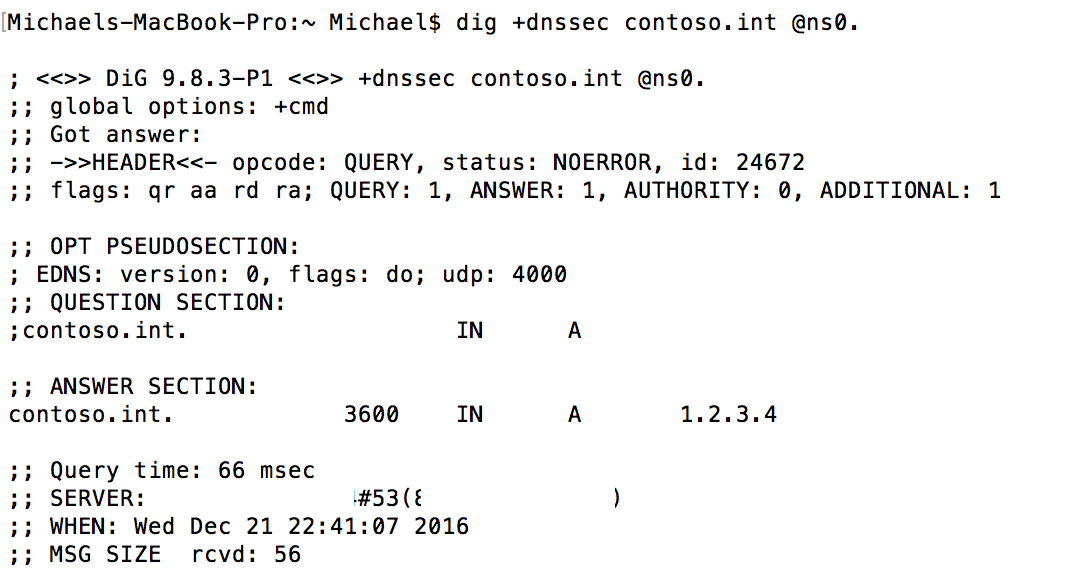
Michael Booth
Friday, December 23, 2016 7:25 AM
Hi Michael,
Did you run two commands on DNS server?
Please follow link below to deploy new DNSSec for test:
Step-by-Step: Demonstrate DNSSEC in a Test Lab
https://technet.microsoft.com/en-us/library/hh831411(v=ws.11).aspx#Configure DNS1
You could check article below to understand Windows server 2016 new DNS feature overview:
What's New in DNS Server in Windows Server 2016
https://technet.microsoft.com/en-us/windows-server-docs/networking/dns/what-s-new-in-dns-server
Best Regards
John
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Sunday, February 12, 2017 7:00 PM
I am definitely having the same issue. Just went through an extensive migration process, only to revert back to my server 2012 r2 checkpoint because of this. Did you end up finding a resolution for this?
Monday, April 3, 2017 5:23 PM
Hi,
There are some DNSSEC fundamentals that I think are causing your issue here.
An authoritative server will not reply with DNSSEC records unless validation is requested, because as far as the server knows the requestor is not DNSSEC aware. You can force DNSSEC records to be returned with dig by adding the +dnssec option.
When you query the google public resolvers for isc.org, these public servers have a root trust anchor installed. Therefore, they will request validation for any signed zone that has the proper secure delegation in place. In other words, since .org is signed and isc.org has a proper DS record, then isc.org will be validated by any server with a root trust anchor, such as 8.8.4.4.
However, when you attempt to resolve the zone contoso.int this is not a valid public zone. There is no parent TLD .int server with a trust anchor and no contoso.int DS record, so validation does not occur automatically.
Try adding +dnssec to your dig and it should work. The zone will never validate against a public DNS server, however.
Thanks,
-Greg
Sunday, July 16, 2017 6:52 AM
I'm having the same problem: I'm trying to migrate my DNS from a Win2012 R2 server to Win2016. However, I am also unable to get it to return RRSIG although they are there in the zone file.
On Windows 2012 R2, the DNS server config has an option "Enable DNSSEC validation for remote responses":

...but the same option is missing on Windows 2016:

Heeelp?!? Is Win2016 DNS broken, or has the config options for DNSSEC validation been moved elsewhere?
For cross-reference: I found an mailing list thread discussing the same issue, and I have posted a the same question on serverfault.com, hoping that there's some solution to this:
http://webcache.googleusercontent.com/search?q=cache:fEdkPUHEA40J:lists.cloudapp.net/pipermail/windns-users/2016-July/000133.html+&cd=2&hl=en&ct=clnk
https://serverfault.com/questions/862378/dnssec-broken-in-windows-2016s-dns-server
Sunday, July 16, 2017 8:09 AM
Hi,
It's enabled by default on 2016. You need to use Windows PowerShell to toggle the setting.
Below is how you would turn the setting off:
$a = Get-DnsServerSetting –all | $a.EnableDnsSec = $false $a | set-dnsServerSetting
To see the current setting just issue (Get-DnsServerSetting).EnableDnsSec
To turn the setting on you would set it to $true:
$a = Get-DnsServerSetting –all | $a.EnableDnsSec = $true $a | set-dnsServerSetting
Thanks,
-Greg