Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Question
Tuesday, May 16, 2017 10:17 PM | 1 vote
Hi everyone!
Please help me with little but urgent task
I need to identify which application/image/process performs DNS lookup for some hostname
For example;
I see that one of my PC generates DNS lookup for some hostname, for example DNS lookup for xxxxxx.com
My goal is to identify what image\process\application generate network traffic to that hosname
Very IMPORTANT to note, that xxxxxx.com is not resolvable to IP address (I am investigating unknown malware case ), xxxxxx.com was generated by Domain Generation Algorithm (common for malware)
I tried use sysinternals tools. I used system explorer and Microsoft Message Analyzer
With help of message analyzer I piked up DNS query and processid. In process explorer I found that process, but the problem is:
1) most dns querys are handled by svchost.exe
2) I don't see original application, I see that svhost.exe sends DNS query to my DNS server
For example when I try to reach xxxxxx.com from browser I see that svchost.exe performs DNS lookup to my DNS server, and process ID is 444 (whis is common for svchost.exe).
My goal is to see what original application or image search xxxxxx.com For example I need to see that Firefox browser did a call to svchost.exe for xxxxxxx.com hostname resolve
How do think is is possible ?
Best regards,
Max
All replies (12)
Tuesday, May 16, 2017 11:38 PM
NetMon should help here.
Have a look at this thread :
Arnav Sharma | http://arnavsharma.net/ Please remember to click “Mark as Answer” on the post that helps you, and to click “Unmark as Answer” if a marked post does not actually answer your question. This can be beneficial to other community members reading the thread.
Wednesday, May 17, 2017 12:58 AM
Hello Arnav,
NetMon does not show process ID at all, at least i tried but no result.
Wednesday, May 17, 2017 8:13 AM
Hi ,
On Windows, most DNS queries are made by the DNS Client service, hosted in svchost.exe, so it won't really help that much know which process made the actual network operation.
Best regards
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Wednesday, May 17, 2017 1:01 PM
Yest, I see what services in interested svchost.exe process, but still have question
can we see who requests DNS client and what request contains (hostname) ?
Wednesday, May 17, 2017 5:06 PM
I tried use sysinternals tools. I used system explorer and Microsoft Message Analyzer
Try ProcMon instead?
Robert Aldwinckle
Thursday, May 18, 2017 8:16 AM
Hi Robert Aldwinckle,
Have you successfully captured related information using process monitor?
I have tried on my side, but I am not good at it. Would you mind to share your experience with us?
Best regards
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact [email protected].
Thursday, May 18, 2017 12:21 PM
Hi Robert ,
But what I should search in ProcMon. Form MS Message Analyzer I have Process ID. In ProcMon I can see all info related interested process ID but it is tons of records. What records should show me exactly application/process name which called for hostame resolution to DNS client
Thanks
Max
Thursday, May 18, 2017 12:37 PM
Guys I want to share some screenshots 
Thursday, May 18, 2017 12:37 PM
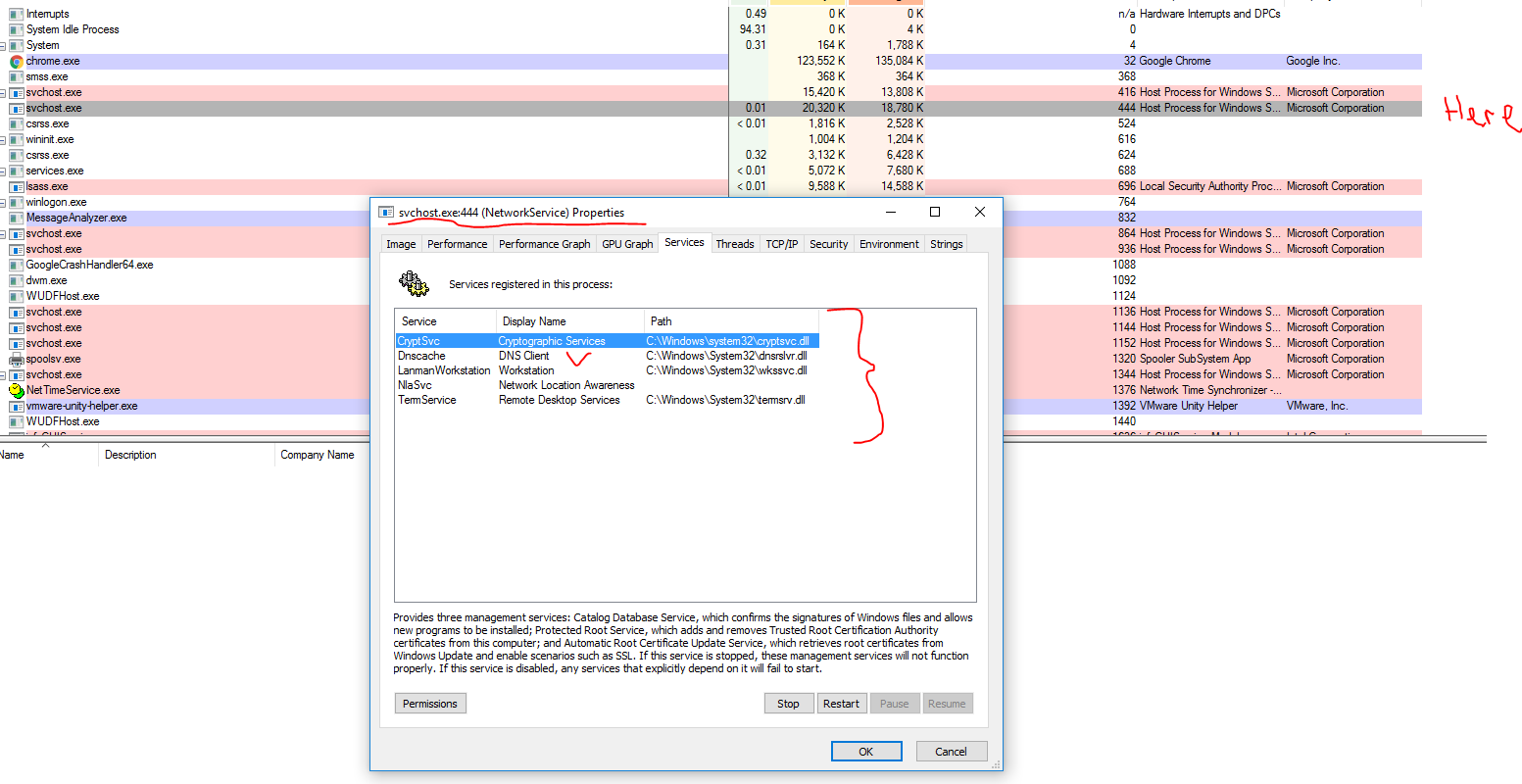
Thursday, May 18, 2017 12:41 PM
QUERY, Query Name: sdfasdfasdfasdf.com, RR Type: A, RR Class: Internet 444 svchost.exe
This is the question. Request was from browser (chrome) but in MS Message Analyzer we see procecc ID is 444 and process name is svchost.exe
In process explorer we can pick up process information
But how (where) I can find information that ORIGINAL call was from browser CHROME.EXE to DNS Client service and request was handled by SVCHOST.EXE ???
Windows Guru please help
Thursday, May 18, 2017 2:56 PM
What records should show me exactly application/process name which called for hostame resolution to DNS client
I don't know. I was only pointing out that ProcMon would contain more complete data than ProcExp. However, another advantage of using ProcMon is that you can add more tracing and then get a clue from it what that is doing. For example, I just tested nslookup social.technet.microsoft.com 8.8.8.8 with and without netsh trace start scenario=AddressAcquisition and think that ProcMon contains more detail even before I stopped the trace. I haven't looked at the NetTrace.etl yet. Perhaps MessageAnalyzer will help interpret it for me.
I would agree it would help to have more clarity about how svchost.exe gets dispatched. A surprise for me was that nslookup.exe and the threads it spawns actually end before any of the Network I/O it generates gets started.
Robert Aldwinckle
Friday, April 13, 2018 12:30 PM
You can try stopping "DNS Client" service. After that, I believe, you will be able to see the original executable which is generating DNS queries. It worked for me on Windows 7.