Hi @Cory C ,
Sorry that I don't quite understand the issue, and you said this caused the accounts logon failure, logging on to OWA/ECP or clients?
And the mail flow is good?
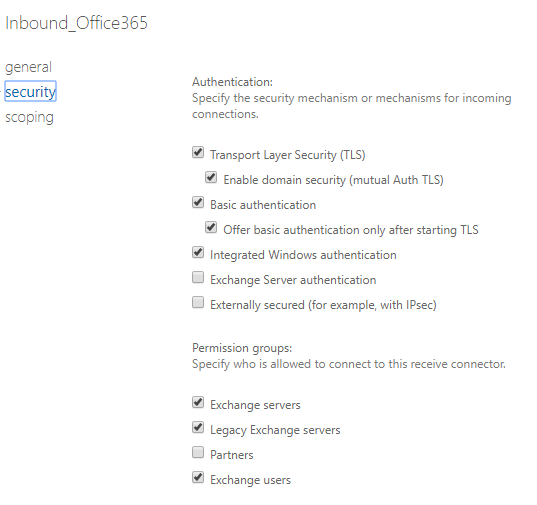
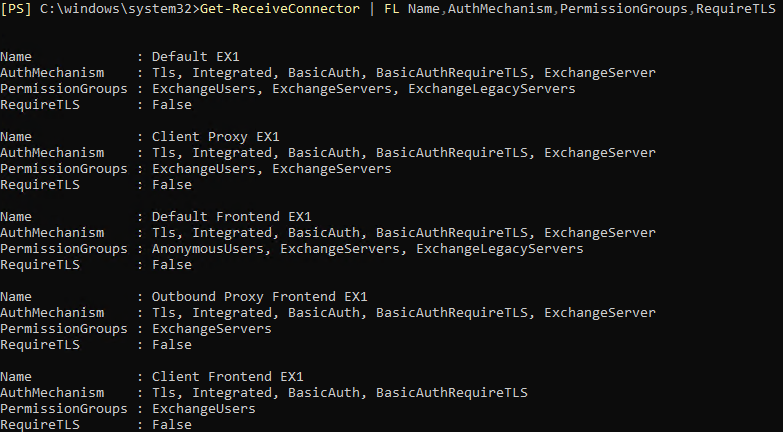
If you don't mind, restore the Connectors to the default status and check. And I'm thinking the Exchange Server is necessary member of the group list.
Regards,
Lou
If the response is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.